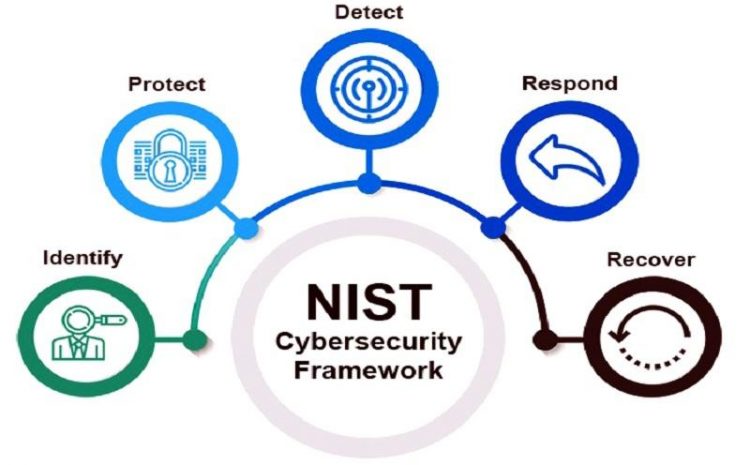
Understanding and Installing UA Analytics on Your Website
Installing ua analytics is one of the most important steps that internet business owners should learn. Internet activity without analytics is like expecting a mechanic without tools to open a car engine. Therefore, if you…