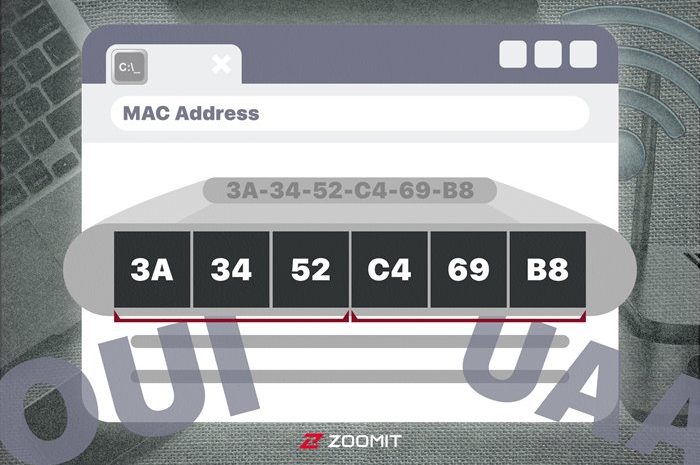
What Is Corporate Wireless Internet
Corporate Wireless Internet: With The Advancement Of Technology And The Increasing Influence Of The Internet On Daily Activities, The Use Of Wireless Communication Is Expanding Rapidly. Currently, the activities of many organizations and large administrative…