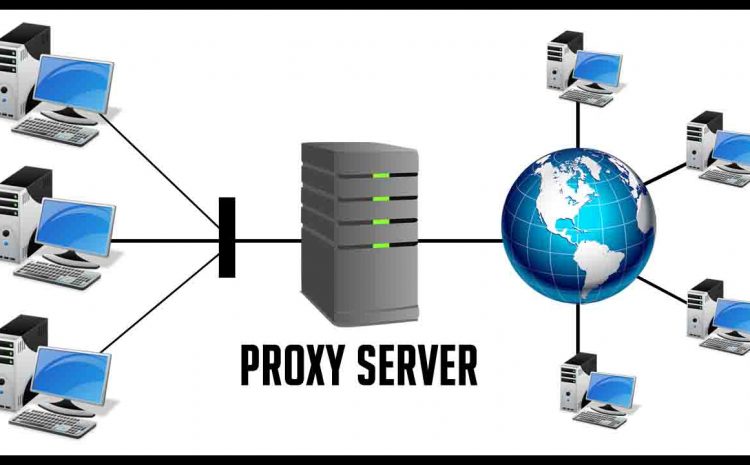
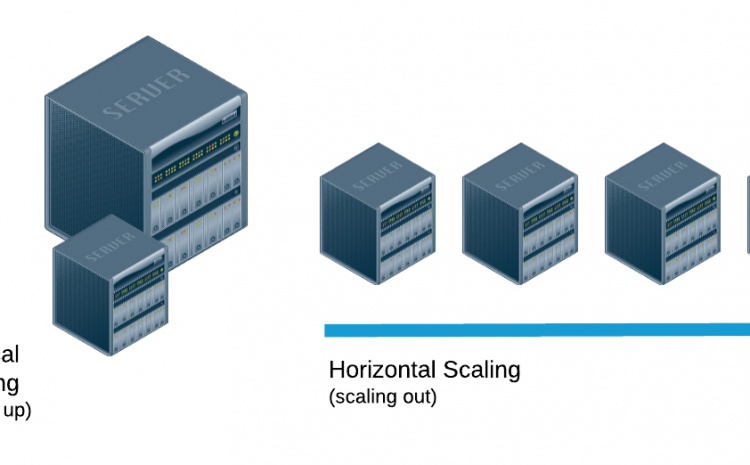
What Is a Firewall? every thing you need about it.
What Is a Firewall? A Firewall is a network security device that monitors. And filters incoming and outgoing network traffic based on an organization’s previously established security policies. At its most basic, a firewall is…