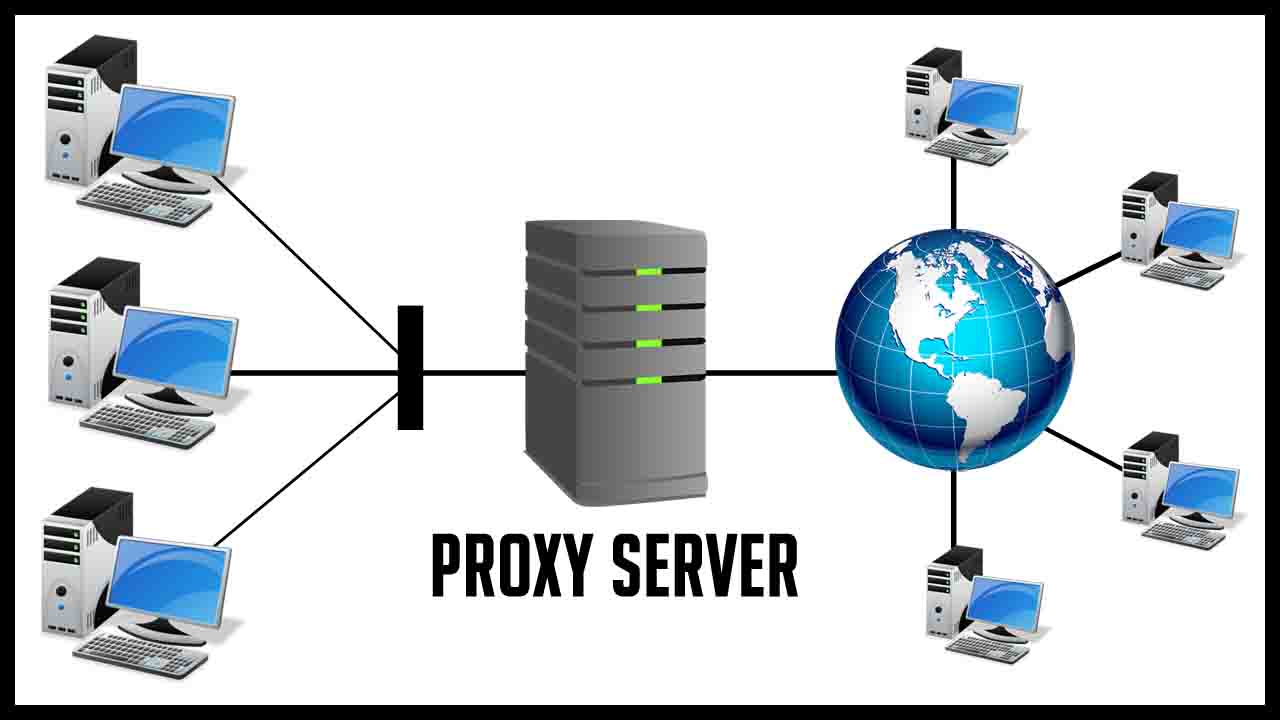
What Is a Proxy Server?
A proxy server provides a gateway between users and the Internet. It is a server, referred to as an “intermediary” because it goes between end-users and the web pages they visit online.
When a computer connects to the Internet, it uses an IP address. This address is similar to your home’s street address, telling incoming data where to go and marking outgoing data with a return address for other devices to authenticate. A proxy server is essentially a computer on the Internet that has an IP address of its own.
Proxy Servers and Network Security
Proxies provide a valuable layer of security for your computer. They can be set up as web filters or firewalls, protecting your computer from internet threats like malware.
This extra security is also valuable with a secure web gateway or other email security products. You can filter traffic according to its level of safety or how much traffic your network, or individual computers, can handle.
How to use a proxy? Some people use proxies for personal purposes, such as hiding their location while watching movies online. For a company, however, they can be used to accomplish several key tasks, such as:
- Improve security
- Secure employees’ internet activity from people trying to snoop on them
- Balance internet traffic to prevent crashes
- Control the website’s employees and staff access in the office
- Save bandwidth by caching files or compressing incoming traffic
How a Proxy Works
Because a proxy server has its IP address, it acts as a go-between for a computer and the Internet. Your computer knows this address, and when you send a request on the Internet, it is routed to the proxy, which then gets the response from the web server and forwards the data from the page to your computer’s browser, like Chrome, Safari, Firefox, or Microsoft Edge.
How to Get a Proxy
There are hardware and software versions. Hardware connections sit between your network and the Internet, where they get, send, and forward data from the web. Software proxies are typically hosted by a provider or reside in the cloud. You download and install an application on your computer that facilitates interaction with the proxy.
A software proxy can often be obtained for a monthly fee or for free. The free versions tend to offer users fewer addresses and may only cover a few devices, while the paid proxies can meet the demands of a business with many devices.
How Is the Server Set Up?
To start using a proxy server, you must configure it on your computer, device, or network. Each operating system has its setup procedures, so check the steps required for your computer or network.
However, in most cases, setup means using an automatic configuration script. If you want to do it manually, you can enter the IP address and the appropriate port.
How Does the Proxy Protect Computer Privacy and Data?
A proxy server performs the function of a firewall and a filter. The end-user or a network administrator can choose a proxy designed to protect data and privacy. This examines the data going in and out of your computer or network. It then applies rules to prevent you from having to expose your digital address to the world. Hackers or other bad actors see only the proxy’s IP address. Without your IP address, people on the Internet cannot access your data, schedules, apps, or files directly.
With it in place, web requests go to the proxy, which reaches out and gets what you want from the Internet. If the server has encryption capabilities, passwords and other personal data get an extra tier of protection.
Types of Proxy Servers
While all proxy servers give users an alternate address to use the Internet, there are several different kinds, each with its features.
- Forward Proxy
- Transparent Proxy
- Anonymous Proxy
- High Anonymity Proxy
- Distorting Proxy
- Data Center Proxy
- Residential Proxy
- Public Proxy
- Shared Proxy
- SSL Proxy
- Rotating Proxy
- Reverse Proxy
Forward Proxy
A forward proxy sits in front of clients and is used to get data to groups of users within an internal network. When a request is sent, the proxy server examines it to decide whether it should make a connection.
A forward proxy is best for internal networks that need a single point of entry. It provides IP address security for network users and allows for straightforward administrative control. However, a forward proxy may limit an organization’s ability to cater to the needs of individual end-users.
Transparent Proxy
A transparent proxy can give users an experience identical to what they would have if they were using their home computer. In that way, it is “transparent.” They can also be “forced” on users, meaning they are connected without knowing it.
Transparent proxies are well-suited for companies that want to use proxies without making employees aware they are using one. They provide a seamless user experience. On the other hand, transparent proxies are more susceptible to certain security threats, such as SYN-flood denial-of-service attacks.
Anonymous Proxy
An anonymous proxy focuses on making internet activity untraceable. It works by accessing the Internet on behalf of the user while hiding their identity and computer information.
A transparent proxy is best for users who want complete anonymity while accessing the Internet. While transparent proxies provide some of the best identity protection possible, they have drawbacks. Many view transparent proxies as underhanded, and users sometimes face pushback or discrimination.
High Anonymity Proxy
A high anonymity proxy is an anonymous proxy that takes anonymity one step further. It erases your information before the proxy connects to the target site.
The server is best suited for users for whom anonymity is necessary, such as employees who do not want their activity traced back to the organization. On the downside, some of them, particularly the free ones, are decoys set up to trap users to access their personal information or data.
Distorting Proxy
A distorting proxy identifies itself as a proxy to a website but hides its own identity. It does this by changing its IP address to an incorrect one.
Distorting proxies are a good choice for people who want to hide their location while accessing the Internet. This type of proxy can make it look like you are browsing from a specific country and give you the advantage of hiding your identity and that of the proxy. This means your identity is still secure even if you are associated with the proxy. However, some websites automatically block distorting proxies, which could keep an end-user from accessing sites they need.
Data Center Proxy
Datacenter proxies are not affiliated with an internet service provider (ISP) but are provided by another corporation through a data center. The proxy server exists in a physical data center, and the user’s requests are routed through that server.
Datacenter proxies are a good choice for people who need quick response times and an inexpensive solution. They are, therefore, a good choice for people who need to gather intelligence on a person or organization very quickly. They carry the benefit of giving users the power to swiftly and inexpensively harvest data. On the other hand, they do not offer the highest level of anonymity, which may risk users’ information or identity.
Residential Proxy
A residential proxy gives you an IP address that belongs to a specific, physical device. All requests are then channeled through that device.
Residential proxies are well-suited for users who need to verify the ads that appear on their website so that they can block cookies, suspicious or unwanted ads from competitors, or bad actors. Residential proxies are more trustworthy than other proxy options. However, they often cost more, so users should carefully analyze whether the benefits are worth the extra investment.
Public Proxy
A public proxy is free and accessible to anyone. It works by giving users access to its IP address and hiding their identity as they visit sites.
Public proxies are best suited for users for whom cost is a major concern and security and speed are not. Although free and easily accessible, they are often slow because they get bogged down with free users. When you use a public proxy, you also run an increased risk of having your information accessed by others on the Internet.
Shared Proxy
More than one user uses shared proxies at once. They give you access to an IP address that other people may share, and then you can surf the Internet while appearing to browse from a location of your choice.
Shared proxies are a solid option for people who do not have much money to spend and do not necessarily need a fast connection. The main advantage of a shared proxy is its low cost. Because others share them, you may get blamed for someone else’s bad decisions, which could get you banned from a site.
SSL Proxy
A secure sockets layer (SSL) proxy provides encryption between the client and the server. As the data is encrypted in both directions, the proxy hides its existence from the client and the server.
These proxies are best suited for organizations that need enhanced protection against threats that the SSL protocol reveals and stops. When used in connection with a website, Google prefers servers that use SSL, an SSL proxy, which may help its search engine ranking.
Rotating Proxy
A rotating proxy assigns a different IP address to each user that connects to it. As users connect, they are given an address unique from the device that connected before it.
Rotating proxies are ideal for users who need to do a lot of high-volume, continuous web scraping. They allow you to return to the same website again and again anonymously. However, you have to be careful when choosing rotating proxy services. Some of them contain public or shared proxies that could expose your data.
Reverse Proxy
Unlike a forward proxy, which sits in front of clients, a reverse proxy is positioned in front of web servers and forwards requests from a browser to them. It works by intercepting requests from the user at the web server’s network edge. It then sends the requests to and receives replies from the origin server.
Reverse proxies are a strong option for popular websites that must balance the load of many incoming requests. They can help an organization reduce bandwidth load because they act like another web server managing incoming requests. The downside is that reverse proxies can potentially expose the HTTP server architecture if an attacker can penetrate it. This means network administrators may have to beef up or reposition their firewall if they are using a reverse proxy.
Proxy Server vs VPN
Proxy servers and virtual private networks (VPNs) are designed to protect the user’s privacy. Yet they have slightly different goals and accomplish them in different ways.
Proxy Servers are primarily designed to protect the user from the server they connect to. This may include concealing their identity (via anonymous proxies) or filtering web traffic (such as blocking potentially malicious or inappropriate sites). Proxy servers are generally not designed to protect a user from third parties.
Remote Access VPNs are designed to protect the confidentiality of the connection between a client and a server. All traffic flows through an encrypted tunnel, which makes it impossible for eavesdroppers to view the traffic. However, the server at the other end of the connection has full access to the traffic, meaning that a VPN does nothing to protect a user’s privacy or security against a malicious server.
Benefits of a Proxy Server
A proxy server provides several benefits to its users, such as:
- Increased Privacy: A proxy server can conceal a user’s IP address from the server and make multiple clients appear to be a single computer. This can increase the privacy of Internet users.
- Blocking Malicious Sites: Proxy servers are commonly used to implement content filtering. A server can be designed to block access to malicious or inappropriate sites.
- Content Filtering: A proxy server can block certain types of content on websites, helping to decrease the risk of infections from malicious sites.
- Site Caching: A user may regularly visit a site with static content. A proxy server can save a copy of this content and serve it directly to the user, enabling the user to access it more quickly.
- Bypassing Restrictions: Some websites are only available from certain countries or regions. A proxy server in an accepted location can allow users to bypass these restrictions.
Proxy Server Limitations
While a proxy server has several benefits, it also has its limitations, including:
- Slower Speeds: A proxy server adds a step as traffic flows between the client and the server. This means that any non-cached content may load more slowly.
- No Encryption: Unlike a VPN, most proxy servers don’t provide traffic encryption, which means they provide no additional protection against third-party threats.
- Server Logging: All user traffic flows through the proxy server. This means that a server can log a user’s Internet history, putting privacy and security at risk.