Demilitarized Zone
As you may know, In terms of computer security, a DMZ is a physical or logical subnet. Moreover, it includes services from an organization that is exposed to the outside world, which is an unreliable and generally larger network such as the Internet. The purpose of a DMZ is to add an extra layer of security to an organization’s LAN. In addition, this way, each external network node can only access what is provided through the DMZ, leaving the rest of the organization’s network behind the firewall. The DMZ functions as a small, isolated network between the Internet and the private network. In this article, we try to answer the question of what DMZ is and what its uses are.
The word DMZ stands for “demilitarized zone”, meaning that military operations are not allowed there. Note that DMZ does not belong to any of its enclosed networks. This metaphorical naming means that DMZ is used as a gateway to the public Internet. This area is not as secure as the internal network nor as insecure as the public Internet. Moreover, Hosts inside the DMZ are limited to having limited connectivity to certain hosts on the internal network, as DMZ content is not as secure as the internal network. Similarly, communication between hosts in the DMZ and communication with the external network is limited to provide more security for the area and the possibility of providing these special services. In this way, DMZ internal hosts can communicate with both internal and external networks, while one firewall provides integrated traffic between DMZ servers and internal network clients, and the other firewall provides levels of control to protect DMZ against the network. External acts.
DMZ architecture in the network
There are several ways to design a network with DMZ. The two basic methods are to use one or two firewalls, however, many modern DMZs are designed with two firewalls. This basic approach can be extended to create more complex architectures.
A single firewall with at least three network interfaces can be used to build a network architecture involving DMZ. The external network is formed by connecting to the public Internet (via ISP) to the firewall at the first network interface. The internal network is formed by connecting the second network interface and the DMZ network itself, which is connected to the third network interface.

A set of different firewall rules is set up to monitor traffic between the Internet and DMZ, LAN and DMZ and LAN and Internet to carefully control which ports and types of traffic are allowed to enter the DMZ from the Internet, thus connecting certain hosts in They restrict the internal network and prevent unwanted connections to both the Internet and the LAN.
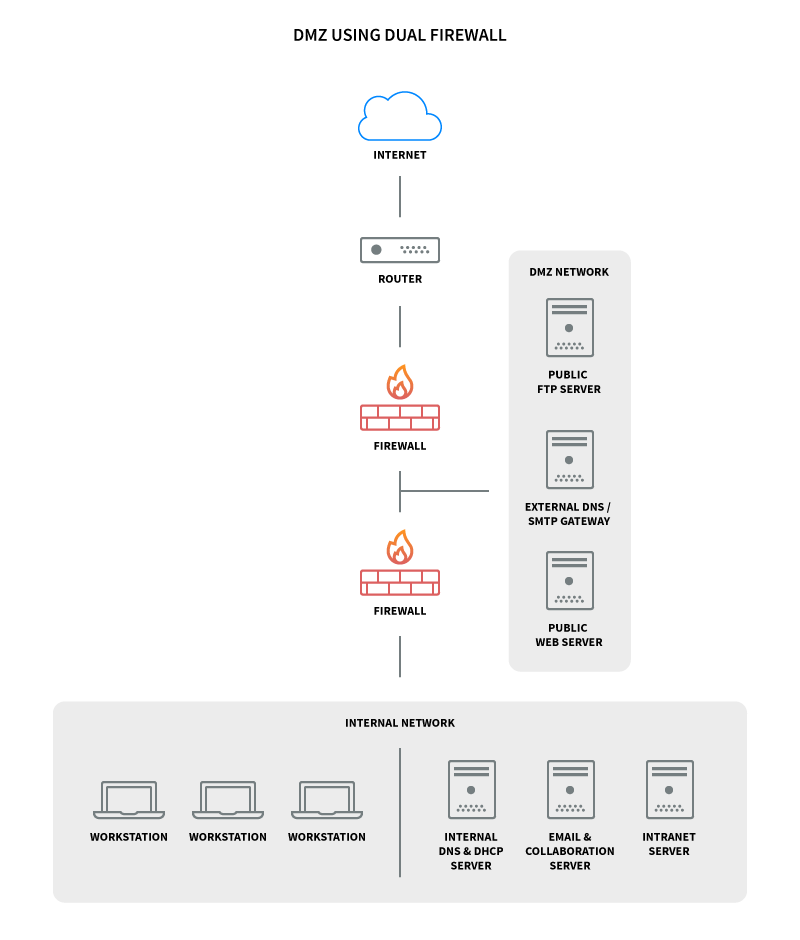
A more secure approach to creating a DMZ network is to configure two firewalls in which the two firewalls are implemented and the DMZ is located between the two. The first firewall, called a perimeter firewall, is configured to allow only external traffic to the DMZ destination. The second firewall, which is an internal firewall, only allows traffic from the DMZ to the internal network. This situation is more secure because, in order for an attacker to have access to the internal LAN, he has to go through two devices.
Security controls can be configured to be specific to each specific network segment. For example, a network intrusion detection system located in the DMZ can be configured to block all traffic except HTTPS requests to port 443.
How does DMZ work?
DMZs are designed to act as a middle ground between the public Internet and the private network. Implementing a DMZ between two firewalls means that all network incoming packets are screened using a firewall or other security measures before they reach the organization’s hosted servers in the DMZ.
If an attacker can bypass the first firewall, he must gain unauthorized access to these services in order to be harmed, and obviously, these systems are also prepared for such attacks. Finally, assuming that an attacker with the right resources can bypass the external firewall and take over a DMZ-hosted system, it must also bypass the internal firewall to access the organization’s sensitive resources. When a determined attacker can break through even the best DMZ security architectures, the attacking DMZ must issue warnings and provide security experts with information about intrusion into the organization.
Advantages of DMZ
The main advantage of DMZ is that it allows public Internet users to access certain security services while maintaining a buffer zone between these users and the private internal network. The security advantages of this area are many, some of which are as follows:
Access control for the organization
Organizations can allow users outside of the private network located on the public Internet to access their various services. The DMZ network provides access to these essential services while also providing a level of network classification that increases the number of barriers an unauthorized user has to access the organization’s private network. In some cases, the DMZ includes a proxy server that centralizes internal traffic flow and facilitates traffic monitoring and recording.
Protection against IP fraud
In some cases, attackers try to circumvent some access control restrictions by forging licensed IPs. In these cases, DMZ can suspend potential IP forgers, while other services on the network test the legitimacy of the IP address by testing its accessibility.
In either case, the DMZ provides a level of network classification that provides space for traffic management, and public services can be accessed at a safe distance from the private network.
What are the uses of DMZ?
DMZ networks have been an important part of enterprise network security for a long time, almost since the introduction of firewalls, and have been used mainly for similar reasons, mainly involving the protection of enterprise systems and sensitive resources. DMZ networks can be used to isolate and keep potential attackers’ systems away from internal networks, as well as to reduce and control access to these systems from outside the organization. Using DMZ is an old-fashioned approach to hosting enterprise resources and making them available to at least a number of external users.
In recent years, organizations have begun to use virtual machines or containers to separate different parts of the network or specific applications from the rest of the organizational environment. Cloud technologies have also largely eliminated the need for many organizations to have internal web servers. Many external-facing infrastructures, such as SaaS applications that were once part of the enterprise DMZ, have now been moved to the cloud.
The following is a list of some DMZ applications:
- Web servers with general information
- Front application (backend must be behind DMZ and secure)
- Mail server
- Authentication services
- Services such as HTTP for public use, secure SMTP, secure FTP, and secure Telnet
- VoApplication gateways servers
- Testing and staging servers
DMZ installation guide on servers
Before you can configure a DMZ, you must decide which services will run on each server. The DMZ server typically runs physically and logically on a different part of the network. This means that you must use a separate server to host services that you want to be public, such as DNS, web, email, and so on.
From the point of view of productivity, DMZ is implemented on different subnets from LAN. To build a “civilian area network” (DMZ) you must have a firewall with three network interfaces, one for untrusted networks (Internet), one for DMZ, and one for the internal network. All servers you want to connect to the external network must be on the DMZ network, and all servers containing sensitive data must be located behind the firewall.
When configuring the firewall, you should impose strict restrictions on traffic to the internal network, but you can be less strict with DMZ traffic. You will then need to provide NAT for computers on the LAN so that they can access the Internet for client hosts. You must also allow clients to connect to DMZ servers. In the image below, you can see the stop diagram of a DMZ network:
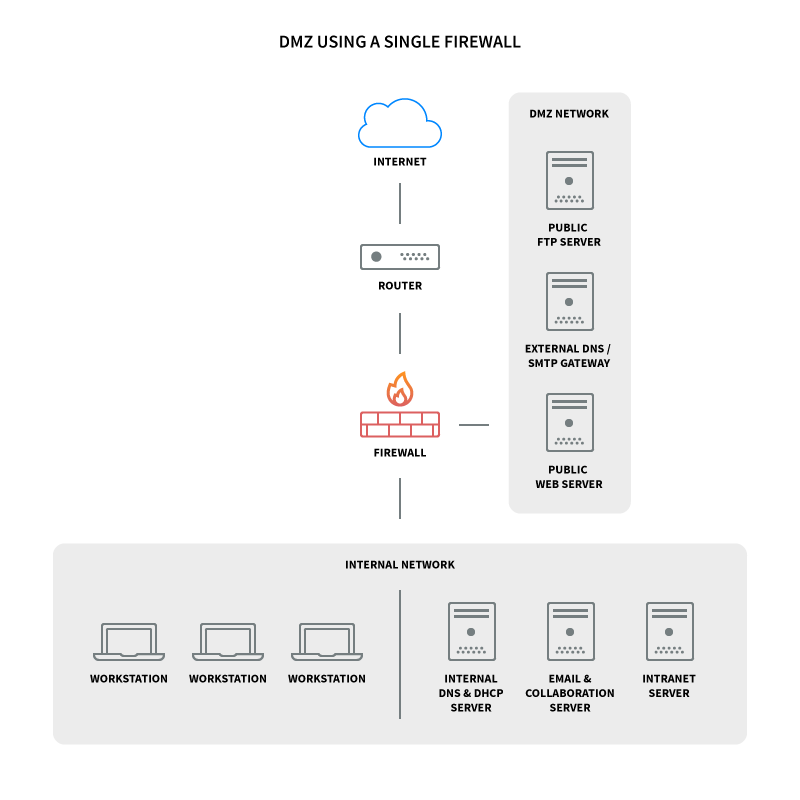
This configuration is also known as the tripod model. You can use two firewalls to increase the level of security. In this setting, one of the firewalls only allows traffic with DMZ destination, while the second firewall allows traffic with DMZ destination from the internal network. This creates an extra layer of security, as two devices must be compromised for an attacker to gain access to the internal network. The DMZ network diagram with two firewalls is as follows:
Summary of DMZ
The simplicity of the DMZ network concept is the main factor in its power. That is why it is recommended to use DMZ in your various infrastructures to strengthen the defense and security layers of your applications. Note, however, that while DMZ can be considered a defensive layer, it is not itself a security measure. Implementing DMZ with well-designed infrastructure and intrusion detection systems (IDS) and intrusion prevention systems (IPS) makes it a stronghold against attackers or unwanted and unnecessary traffic.












