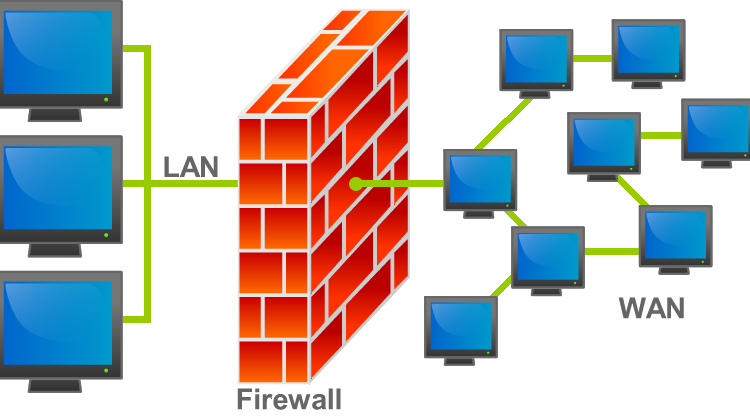
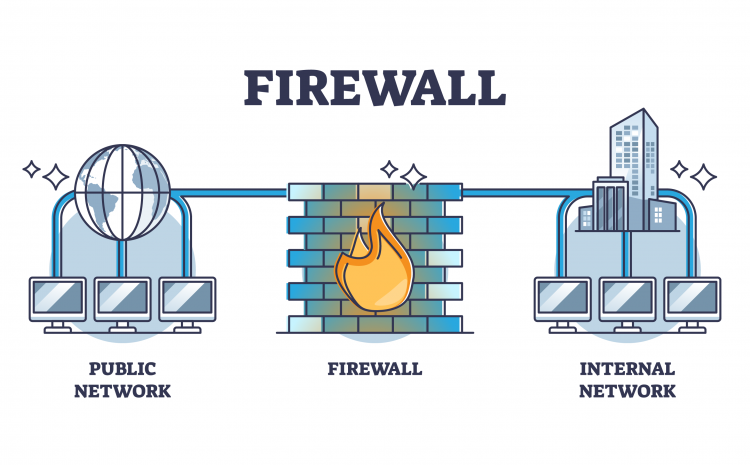
Backup and Recovery: Protecting against cyber-attacks
Backup and recovery are critical components of any IT infrastructure, and their importance cannot be overstated. Cyber-attacks can result in data loss or System failure, and backup and recovery solutions can ensure that data can…