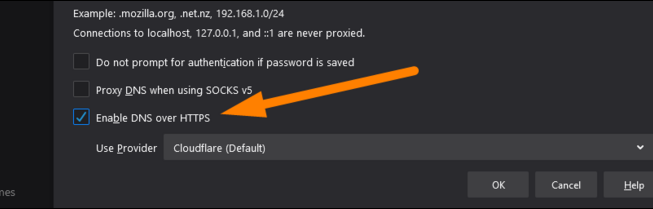
How to Change DNS Server Settings and How to Enable DoH
Laptops, PCs, mobiles, and tablets: Use the default DNS set on the router. They do unless we change them. This DNS is what the Internet service provider (ISP) provides. This DNS server weakens Security and…