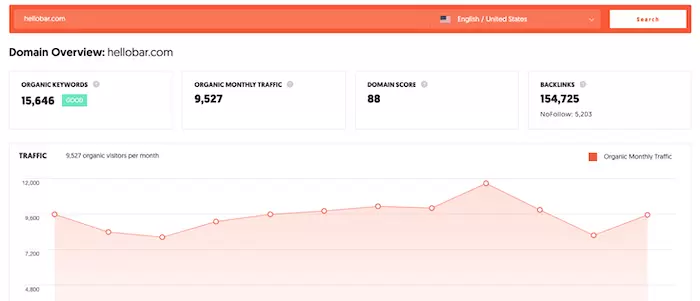
How to Check if a Site is Legit? 7 simple and reliable signs?
There are dozens of unreliable sites for every reputable site, full of fake and inaccurate or unreliable information. Such sites can cause problems for inexperienced and reckless journalists and researchers. Here and in this article,…