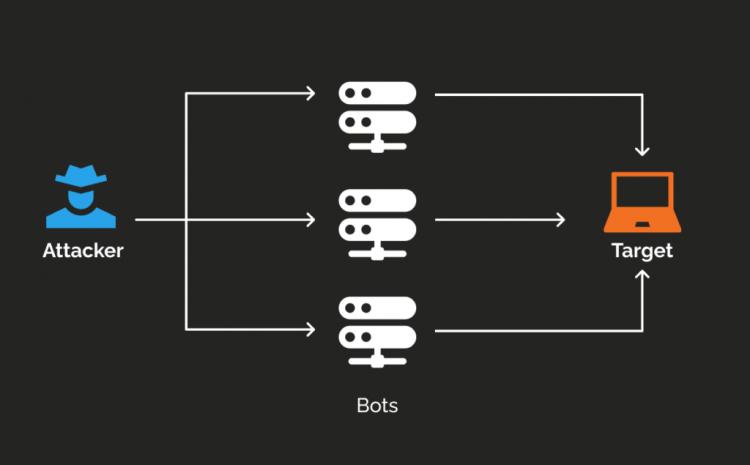
What Are DDoS Attacks and How Can They Be Prevented
If your website or app suddenly goes offline due to a massive influx of traffic, it has likely been targeted by a DDoS or Denial-of-Service Attack. These types of cyber attacks are increasing rapidly, and…