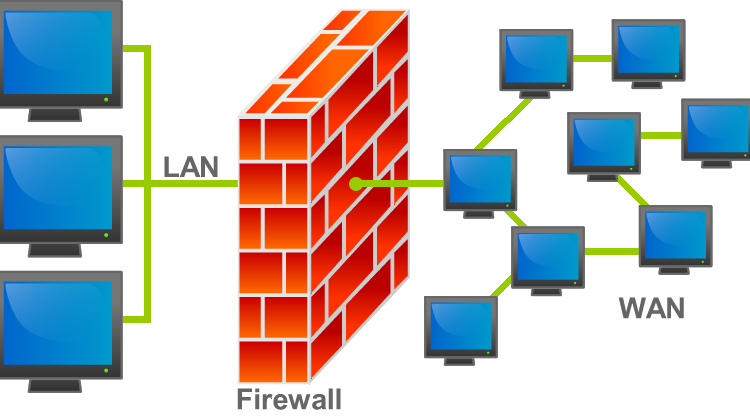
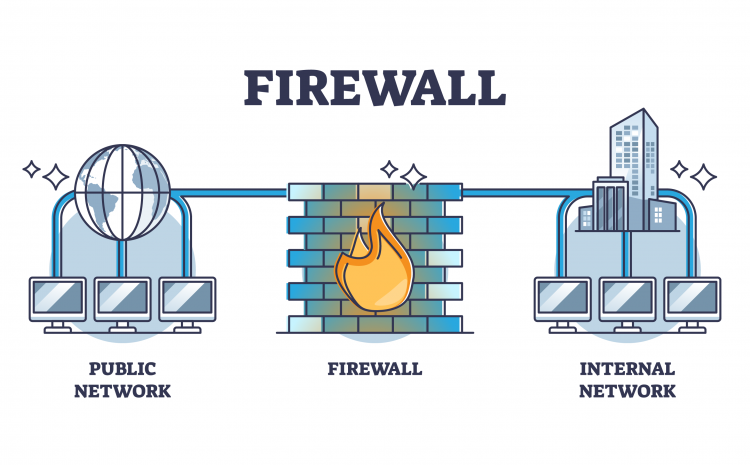
Essential Security Tips for Using Free Public Wi-Fi Safely
When Using Free Wi-Fi Networks In Public Places, You Should Take Care Of Your Security. Otherwise, You Will Lose All Your Data! In recent years, the concept of remote work has attracted more attention from employers,…