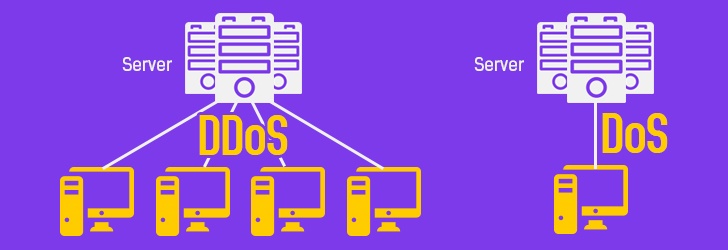
What Is the Difference Between Malware, Spyware, Virus, and Worm
Many PC users believe that malware, viruses, spyware, adware, worms, and trojans are all the same thing. Although all of these infection control trojans are the same, it is worth noting that they are not…