DoS vs. DDoS; What is the difference between these two types of cyber attacks?
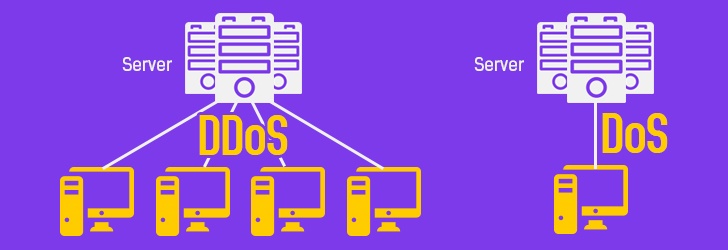
A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service, or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic.
DDoS attacks achieve effectiveness by utilizing multiple compromised computer systems as sources of attack traffic. Exploited machines can include computers and other networked resources such as IoT devices.
At a high level, a DDoS attack is akin to an unexpected traffic jam that clogs up the highway, preventing regular traffic from reaching its destination.
What is the meaning of a DDoS attack? How is this type of attack different from DoS attacks? Although the difference between the two types of cyberattacks is small, the conditions for launching these types of attacks are slightly different.
When a website or online service crashes, we usually come across the words DDoS and DoS. The two are very similar, and even their effect is very similar, but that does not mean that each can be used in another place.
Now, you need to determine which phrase to use in case your favorite website crashes.
What is a DoS attack?
A Denial-of-Service (DoS) attack is an attack meant to shut down a machine or network, making it inaccessible to its intended users. DoS attacks accomplish this by flooding the target with traffic or sending it information that triggers a crash. In both instances, the DoS attack deprives legitimate users (i.e., employees, members, or account holders) of the service or resource they expected.
Victims of DoS attacks often target web servers of high-profile organizations such as banking, commerce, and media companies, or government and trade organizations. Although DoS attacks do not typically result in the theft or loss of significant information or other assets, they can still cost the victim a substantial amount of time and money to address.
There are two general methods of DoS attacks: flooding services or crashing services. Flood attacks occur when the system receives too much traffic for the server to buffer, causing it to slow down and eventually stop. Widespread flood attacks include:
- Buffer overflow attacks – the most common DoS attack. The concept is to send more traffic to a network address than the programmers have built the system to handle. It includes the attacks listed below, in addition to others that are designed to exploit bugs specific to certain applications or networks
- ICMP flood – leverages misconfigured network devices by sending spoofed packets that ping every computer on the targeted network, instead of just one specific machine. The network is then triggered to amplify the traffic. This attack is also known as the Smurf attack or the Ping of Death.
- SYN flood – sends a request to connect to a server, but never completes the handshake. Continues until all open ports are saturated with requests and none are available for legitimate users to connect to.
DDoS vs. DoS; There is not much difference between the two methods
It’s best to start with confusing acronyms. DoS stands for Denial of Service and DDoS stands for Distributed Denial of Service. To understand what a DDoS attack is, you must first understand the concept of DoS. Denying the service is not always a malicious act in itself. This situation occurs when users can not access a website because the server capacity of the website in question is full.
This can occur for several reasons. For example, an article on a website may be noticed by many users for unexpected reasons, and because more people share the link to the article on their social media accounts, hundreds of thousands, or even millions, of people will visit the website simultaneously. They will refer to the desired.
Most large websites, such as major news media and social media platforms, use high-capacity servers with backup servers. Thus, the servers of these sites are unlikely to be down for a while.
DDoS and DoS; From accident to attack
DoS itself is an inevitable part of being online. But DoS, which happens by accident, is very different from DoS or DDoS attacks.
Launching a DoS or DDoS attack is often used by many cyber criminals as a means of sabotage or cyber terrorism. But unlike other cyber attacks, DoS attacks do not require much technical expertise to execute.
The difference between DoS and DDoS attacks is the source of fake traffic. With a DoS attack, the offender sends fake and fast traffic from one place to the destination website or online platform. These attacks are easier to execute, but identifying and blocking them in a timely manner to prevent server crashes is not difficult.
In addition, DoS attacks are relatively low in intensity and take some time to execute. DDoS attacks, on the other hand, make up for all the shortcomings of DoS attacks. DDoS attacks are much more difficult to predict and block because it will take a long time for security systems to detect these types of attacks when distributed.
Sometimes, the site security system can not detect the attack pattern in a timely manner. DDoS can pump a much larger amount of traffic to the destination website, which will make the website almost immediately inaccessible and inaccessible.
These two methods are still a big concern
You may think of those large websites, because of the simple nature of this type of attack. Already have solutions in place to stay safe, and only small websites will be affected. But this image is wrong, and in fact, there are many different types of DDoS attacks present.
The first DoS documentary attack took place in February 2000; An attack in which a 15-year-old Canadian hacker manages to shut down several e-commerce websites such as Amazon and eBay.
Amazon has reportedly detected and stopped an attempted DDoS attack in early 2020. The attack had a traffic rate of 2.3 terabits per second. This traffic is equivalent to more than one trillion bits. Which broke the previous record of 1.7 terabits per second of DDoS. The record of 1.7 terabits per second is related to the DDoS attack of GitHub in 2018.
These types of attacks will not go away.
The Internet has become faster with the introduction of 5G. These conditions, along with increased Internet and computer literacy and the availability of remote hardware such as servers. And IoT-related devices, mean that DDoS attacks are more likely to occur.
Conclusion
The only way to prevent a DDoS attack is to detect it early before it overloads your servers. Methods are also used to more accurately detect human and fake traffic.