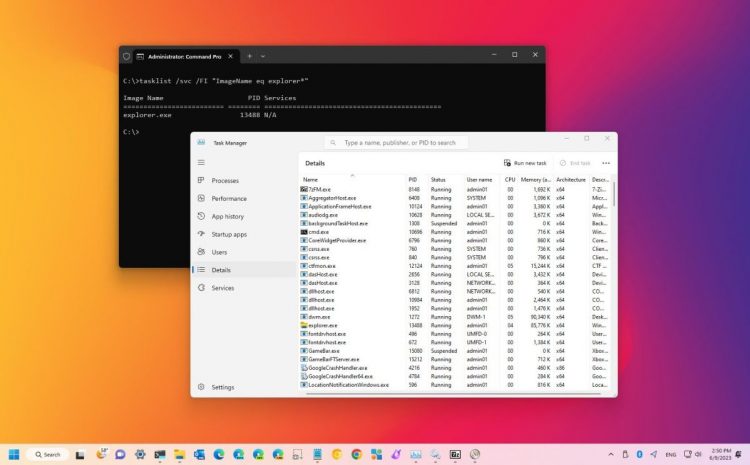
How to Determine the Process ID of a Program in Windows 11
In Windows 11, Programs And Services Receive Identification Numbers Called “Process IDs” (Pids) To Identify Each Process Running On The System And To Distinguish Between Different Instances Of The Same Program. With these simple steps,…