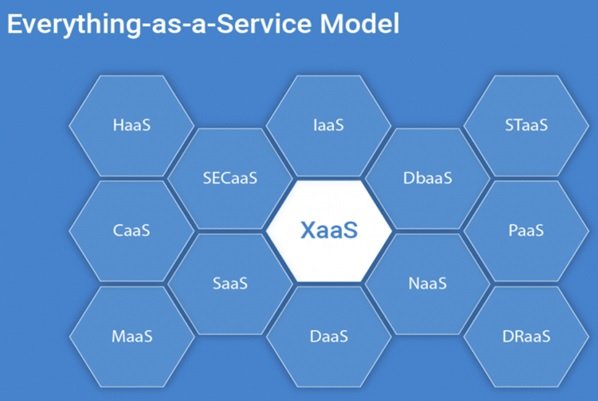
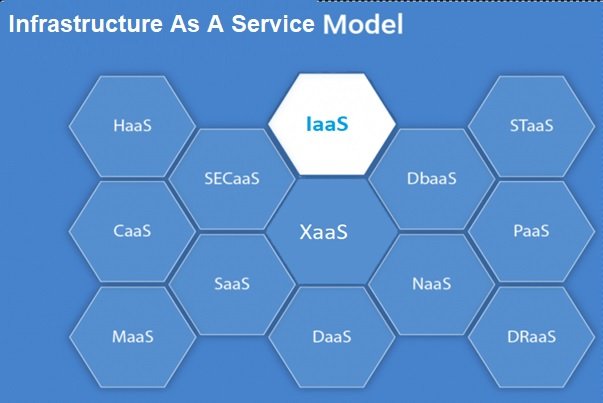
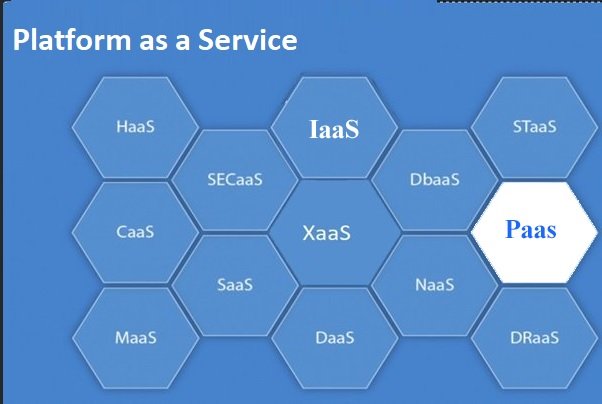
The Best Patterns And Worst Mistakes Around Server Virtualization
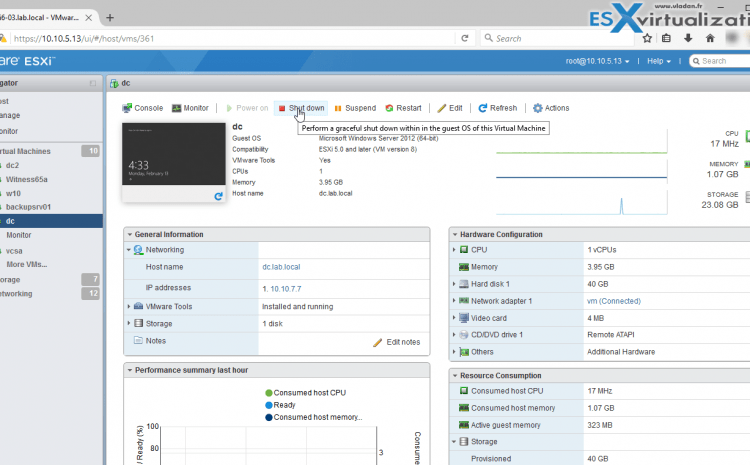
Virtualization Is A Relatively New And Popular Way To Manage Data Centers. There Are Several Benefits To Setting Up Virtual Data Centers At The Heart Of Physical Examples. Multiple virtual servers can implement on a single…