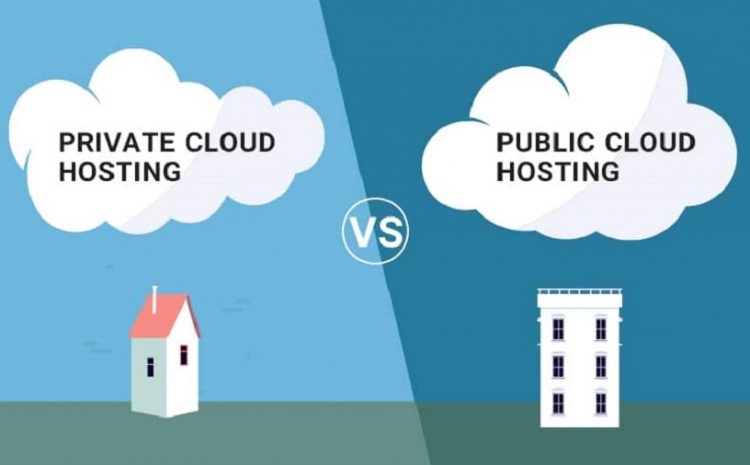
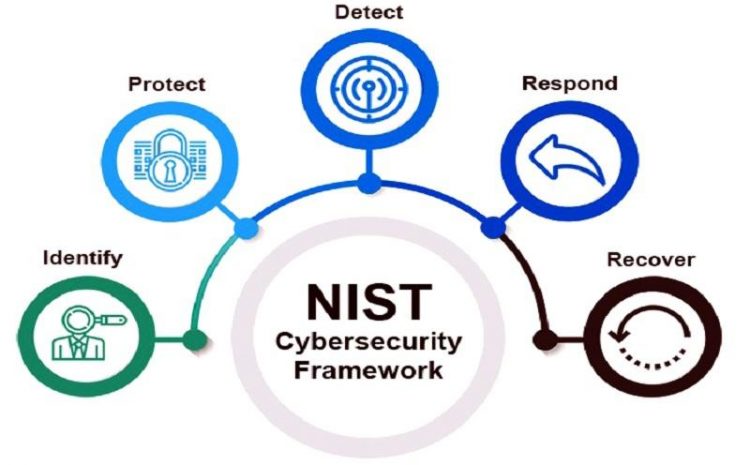
All about learning to search in Google
Nowadays, many people turn to Google to find the answer to any of their questions. To receive your answer from Google professionally, you should review and study Google search training partially and periodically. Some people…