What Is The NIST Cybersecurity Information Security Framework And What Are Its Steps?
If You Look At The Articles Published In The Field Of Security, You Will See That Most Of These Articles Are About Technical Issues And Working With Tools, While There Are Other Important Issues Such As Governance, Risk, And Compliance For Success In The World Of Security.
How do we implement these three essential principles as a practical process? The answer is summarized in a framework concept, which provides a coherent infrastructure for risk management or security controls.
The significant advantage of the framework is that it offers a lot of freedom to implement policies according to business needs.
In general, frameworks are divided into three essential groups: risk frameworks, information security frameworks, and enterprise architecture frameworks.
An overview of frameworks
A framework is a basic structure at the heart of large security architectures on which solutions are implemented. Therefore, frameworks are used in information technology and cyber security to provide a system based on which we can manage risks, develop organizational architectures, and secure all our assets.
Frameworks are road maps that IT and cybersecurity experts of an organization agree on and are developed considering various issues. Frameworks have different components, the most important of which should be mentioned below:
Risk
- NIST RMF is a risk management framework created by the National Institute of Standards and Technology. It is the result of the convergence of three policies presented by the NIST Special Publications, namely 800-39, 800-37, and 800-30. In the risk subcategory, there are the following four essential standards:
- ISO/IEC 27005 is a framework that focuses on risk management and was published by the International Organization for Standardization in the ISO/IEC 27000 subseries.
- OCTAVE: Critical Operations Threat, Asset and Vulnerability Assessment Framework developed by Carnegie Mellon University and focused on risk assessment.
- FAIR is an information risk analysis framework published by the FAIR Institute and focuses on more accurately measuring the probability of incidents and their impact on business activities.
Security Program
- The ISO/IEC 27000 series is a set of international standards for developing and maintaining an information security management system (ISMS) created by two organizations, ISO and IEC.
- NIST Cybersecurity Framework: The NIST Cybersecurity Framework is designed to secure systems used in government institutions. This widely used and comprehensive framework focuses on ensuring high-risk information.
Security Controls
- NIST SP 800-53 lists selected controls and processes to be relied upon to protect susceptible systems.
- CIS Controls: The non-profit Center for Internet Security provides one of the most straightforward approaches to protecting sensitive corporate information and assets that can implement in companies large and small.
- COBIT 2019 is a business framework focusing on managing and governing information technology in companies.
Enterprise Architecture
- Zachman Framework: It is a model for developing enterprise architectures developed by John Zachman.
- Open Group Architecture Framework: It is a model for developing organizational architectures.
- SABSA: Sherwood Applied Business Security Architecture is a model and method for developing risk-oriented enterprise information security architecture and service management. The main feature of the SABSA model is that it focuses heavily on analyzing business requirements to secure them.
Risk frameworks
Risk Management Framework (RFM) should be defined as a structured process that allows the organization to identify and assess risk, reduce it to an acceptable level, and ensure that risk exists in an adequate and controlled group. RMF is a structured approach to risk management.
As you can see, there are a wide variety of management frameworks available; what should be important to you as an information security professional is to ensure that the organization has an RMF that works smoothly. Organizations more accept some frameworks because they have proven to work well over the years. Hence, when choosing a framework, you should do thorough research and select the option that aligns with the organization’s business strategies or edit and implement it if necessary. One of the successful and vital frameworks in this field is NIST RMF, which we intend to learn about its concept and components.
NIST RMF
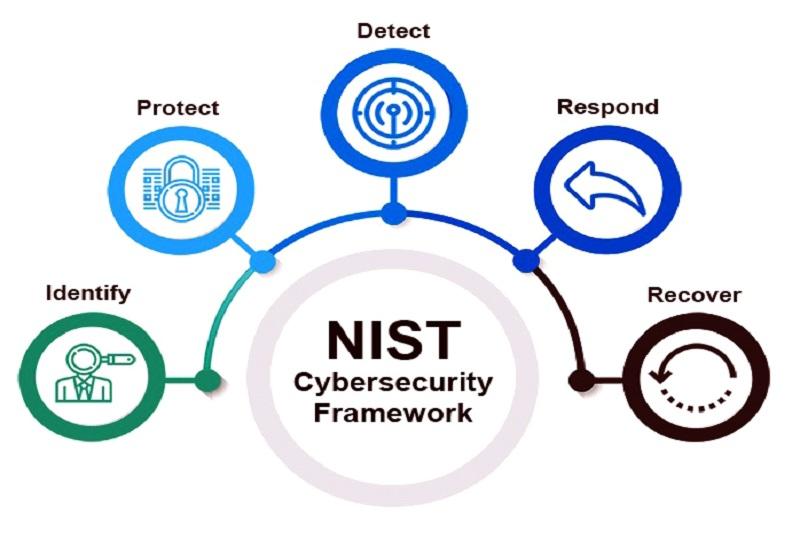
The NIST framework is designed to help organizations of various sizes, primarily large, and focuses on protecting privacy when providing a product, service, or information. The primary purpose of this directive is to improve the security of the critical infrastructure of large organizations against internal and external attacks. Specifically, NIST proposes five main approaches to managing data and information security risks. These functions are identification, protection, diagnosis, response, and recovery.
A brief description of each function is as follows:
- Identify: Helps organizations identify security risks around assets, business environment, and IT governance through comprehensive risk assessment and management processes.
- Protect: Defines the security controls needed to protect information systems and data and includes access control, training and awareness, data security, information protection methods, and maintenance of protective technologies.
- Detect: provides instructions for detecting anomalies in security, surveillance, and network systems to separate security incidents from non-security incidents such as equipment failure.
- Repones: includes recommendations and techniques for planning to respond to security incidents, risk reduction, and incident response processes.
- Recovery: Provides guidelines that organizations can use to return to stable conditions in the event of a cyber attack.
This framework includes the critical elements of risk management that you need to know about as a security professional. It is essential to mention that the above framework is designed for large organizations, and you may have to change its overall structure for implementation. The NIST RMF operates based on a seven-step process (Figure 1).
Note the important point that the cycle shown in Figure 1 is never-ending because information systems are constantly changing. Any changes should analyze to determine if there is a need to make changes to other steps. The explanation of each of the steps shown in Figure 1 is as follows:
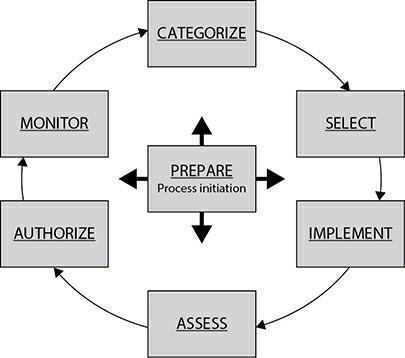
figure 1
Prepare
The first step is to ensure that the activities of senior managers (at both strategic and operational levels) are aligned within an organization. It includes agreeing on roles, priorities, limits, and risk tolerance. Another critical activity in the preparation phase is conducting an enterprise risk assessment that provides a clear view to the security team to understand the risks better. One of the results of this assessment is the identification of valuable assets that should protect in the best way.
Categorize
The next step is classifying information systems based on their sensitivity and hosting sensitive information to be accessed, processed, or transmitted by client equipment. The goal is to create classifications for our systems based on their sensitivity and importance so that we can use appropriate security tools to protect them. Today, most European and American organizations must implement the NIST SP 800-60 framework.
NIST SP 800-60 attempts to determine the vulnerability of systems by focusing on the sensitivity and importance of organizational assets (confidentiality, integrity, and availability). For example, let’s say you have a customer relationship management (CRM) system. If its privacy is compromised, significant damage will be done to the company, especially if the information falls into the hands of competitors.
Still, in contrast to the violation of the integrity and availability of the system, it will probably not have critical and severe consequences for the business. Therefore, it is considered a risky asset. It is under classified. Based on this definition, the security classification for a customer relationship management system is calculated through the following formula:
SCCRM= {(Confidentiality, High), (Integrity, Low), (Accessibility, Low)} The SP 800-60 uses three levels of security classification, low, medium, and high. The standard label refers to information systems that do not have essential information. As a result, violating the three principles of confidentiality, integrity, and availability of business does not face a severe challenge.
The moderate label refers to systems where a violation of at least one of the three principles disrupts the performance of business activities. The title above refers to systems where a breach of any of these principles will cause business operations to stop. In our example, violating the code of confidentiality is very important because it damages the brand’s reputation.
Select
Once you’ve categorized your systems, it’s time to select and possibly configure the controls you’ll use to protect your assets. The NIST RMF defines three types of security controls: common, specific, and hybrid.
Joint control is a control that is defined and applied to several systems. For example, in the CRM scenario, if we implement a web-based application firewall (WAF) for CRM, we have used a common security control mechanism because it is possible to use the firewall in connection with other software components and services of the organization. WAF goes beyond monitoring a single CRM system and can protect the CRM of other networked systems.
Specific controls are implemented across systems and only protect a particular system. For example, imagine a CRM login page that uses the Transport Layer Security (TLS) protocol to encrypt confidential user information. If the authentication subsystem is an integral part of CRM, this is an example of a specific control.
At first glance, everything seems black or white in the NIST framework, but the security world is more complex, and often, controls fall between standard and specific commands. A hybrid control is partly shared and partly particular to a system. In the CRM example, a hybrid control could be security education and awareness.
Implementation
At this stage, must do two essential tasks; Implementation and documentation. The work is simple. The first part is very straightforward. For example, if you determined in the previous step that you need to add a rule to the WAF to filter out attacks such as Structured Query Language (SQL) injection, you run that rule. The part that most of us struggle with is documenting the changes we make.
Documentation is essential for two reasons. First, it allows us to understand what controls exist, where they are located, and why they are defined and implemented. You try to understand specific parameters or rules but hesitate to change them because it might disrupt the system’s performance. Have you ever been put in charge of a system whose configuration is in critical condition?
This problem occurs due to missing or misconfigured documentation, which allows hackers to exploit hidden vulnerabilities or misconfigurations and successfully implement a cyber attack. A second reason for the importance of documentation is that it will enable us to fully integrate controls into the overall monitoring and evaluation program and have accurate information regarding rules that have become obsolete and ineffective over time.
Assessment
Evaluation of controls plays a vital role in proper risk management. The security controls we intend to implement will prevent cyber attacks only if we can evaluate them. Organizations must have a comprehensive plan that considers all security controls (standard, hybrid, and system-specific) against the risks they are intended to address. This plan must be reviewed and approved by the relevant authorities to implement.
For this reason, it is essential to evaluate all the processes, tools, and policies implemented. The evaluation should show that the developed framework can best deal with the risks and protect the organizational assets. Therefore, the framework development team should not evaluate it. This responsibility should be entrusted to the organization’s security expert to assess the controls’ effectiveness and ensure that the right tools are selected, and the documents are correctly compiled.
The evaluation of security controls is called an “audit.” the review should determine whether the authorities’ implementation is adequate. Hence, the results should be documented in the reports to be used as a reference for subsequent evaluations. If the rules are ineffective, corrective actions should take to eliminate the deficiencies, and the result of the secondary assessment should be documented. Finally, security plans are updated to incorporate evaluation findings and recommendations.
Authorize
As you know, no system in the world is without risks. One of the biggest problems that security experts in an organization face are getting various permissions from senior managers to implement security policies in the organization’s network architecture.
At this stage, it should deliver the risk assessment and controls results to the decision maker to issue an approval for the connection of security controls to information systems. This person (or group) is legally responsible and accountable for ensuring that systems continue to operate without problems after authorities are implemented. Therefore, they should provide reliable information because the responsibility for any network malfunction will be on these people and not on the person responsible for implementing security mechanisms.
In most organizations, permissions to implement security frameworks are issued for a specific period in the form of a Plan of Action and Milestone (POAM or POA&M). For this reason, the people who prepare the security framework must clearly explain to the CEO what risks are challenging for the organization and what losses the organization will face if the stakes are ignored. Sometimes, after developing the security framework, you have to revise the operational plan so that you can react quickly in the event of a cyber-attack and that hackers fail in quickly exploiting hidden weaknesses and shortcomings in information systems.
Monitor
We must periodically review all controls to determine whether they are still effective. Have there been changes in the pattern of tactical and technical threats, have new vulnerabilities been discovered, has an undocumented or unapproved change in configuration caused the effectiveness of security controls to decrease, and have the level of risk around organizational assets approached a critical group? These are just some of the issues that we can answer through continuous monitoring and continuous improvement.
last word
The NIST RMF framework is one of the most important and widely used information security risk management frameworks. This framework defines guidelines for managing information security risk in an organization but does not dictate a specific approach to its implementation. In other words, the framework tells us what to do, not how.