What Are XSS Attacks and How Can They Be Prevented?
Cross-site scripting, or XSS, is one of the most common attacks by hackers for malicious purposes on the Web. Although the main abbreviation for this attack is CSS, because it is confused with CSS code, it is considered for it. Today, we are going to introduce XSS attacks and teach you how to prevent them from happening. So stay tuned until the end of the article.
What are XSS attacks?
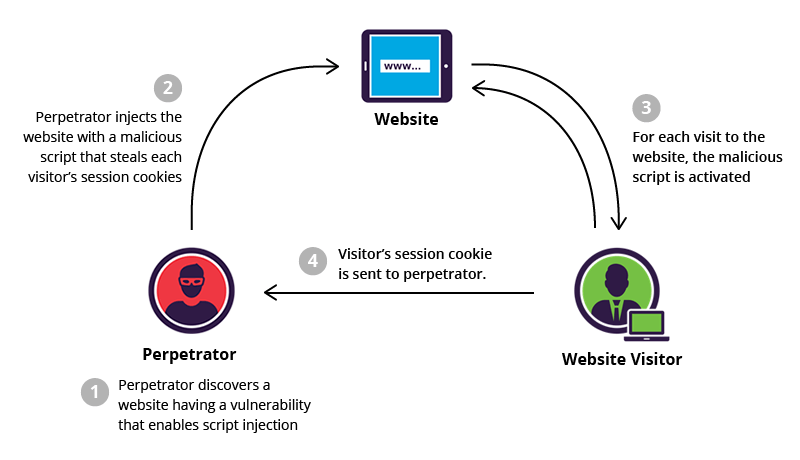
XSS attacks are a type of code injection attack on the client side. In this attack, the attacker tries to execute malicious code through a legitimate web page in the Internet user’s browser, and the main attack occurs when the victim visits that web page or web application.
In fact, the hacker uses the web page or web application to send malicious code to the user’s browser. Sites such as forums, message boards, and web pages that allow users to post comments are the best ways to inject malicious scripts.
If the web page uses the input of infected users in its generated output, it becomes vulnerable to XSS attacks, and the user input must then be parsed by the victim’s browser. XSS attacks can occur in VBScript, ActiveX, Flash, and even CSS. Of course, most attacks occur in JavaScript because this language is one of the main elements of Internet browsers.
XSS attacks and users
Suppose a hacker exploits an XSS vulnerability on a page to inject malicious JavaScript code into a user’s browser. In that case, the web application and its users’ security will be compromised. Unlike security issues, XSS attacks don’t limit users, so if they are dangerous to your website users, they will affect you.
Some hackers also use XSS attacks to disable websites instead of targeting users. In this case, the hacker can inject scripts to change the website’s content or redirect the victim’s browser to the infected pages.
Hacker and JavaScript
XSS attacks are less risky than SQL injections. Injecting JavaScript into a web page may not be dangerous at first glance because most web browsers execute JavaScript code in a completely controlled environment. JavaScript also imposes restrictions on access to the operating system and user files. However, it can be very dangerous if JavaScript is a part of malicious content:
- Malicious JavaScript can infiltrate all objects on other web pages to gain access to the parts that malicious JavaScript users can access. Because Session Tokens are usually stored in user cookies, if a user has them, they can perform profiteering activities by forging the user’s identity and accessing sensitive data.
- Malicious JavaScript can read the Internet browser DOM and then make changes to it. Fortunately, this is only possible on pages where JavaScript is running.
- JavaScript can use the XMLHttpRequest object to send custom HTTP requests to any destination.
- JavaScript in modern browsers can use the HTML5 API, which allows it to access the geographical location, microphone, webcam, and specific files of the user’s computer system. Most of these APIs require the user’s presence, but hackers can use social engineering to solve this problem.
In general, a hacker can easily carry out advanced attacks such as cookie theft, Trojan planting, keylogging, phishing, and identity theft through the items mentioned and a little bit of social engineering. Hackers can use XSS attacks first to launch a powerful attack or use them alongside other attacks, such as CSRF.
How do XSS attacks work?
A typical XSS attack is divided into two parts:
- To execute malicious code in a victim’s browser, the hacker must first find a way to inject the code into a web page that the user is visiting.
- The victim must then visit the malicious, infected web page. If the attack is intended for a specific person, the hacker can use social engineering or phishing to send them an infected URL.
For the first step to be possible, the website must receive user input directly on its pages. The hacker can then insert the malicious string into the web page; this string is the source code used by the user’s browser. Of course, in some cases, the hacker uses social engineering to persuade the victim to click on malicious URLs.
How to prevent XSS attacks
You must keep your website traffic safe to protect yourself from XSS attacks. Your application should not send input directly to users’ browsers without checking the input data. Preventing XSS attacks is not easy, as the techniques to deal with them depend on the type of XSS attack, the user input platform, the framework, and the programming language of the website in question. However, there are some basic principles to stay safe from XSS attacks, which we will briefly explain below:
1- Educating and maintaining the awareness of developers
Everyone involved in developing an application or website should know the risks associated with XSS vulnerabilities. Therefore, you should provide the necessary training on application security to all programmers, quality assurance staff, DevOps team, and system administrators.
2- Lack of trust in user input
Consider all user inputs as untrusted inputs. Any user input part of the HTML output is susceptible to XSS attacks. Therefore, you should treat valid inputs and internal users as public inputs.
3- Using Escaping / Encoding technique
Use the Escaping / Encoding technique depending on where the user inputs are used. For example, you can use HTML, JavaScript, CSS, and URL escape libraries. In other words, use your escapes only when needed.
4- Clear HTML
If the user input must be HTML, you can not use the Escaping / Encoding technique, which will destroy the valid tags. You must use a valid library to parse and clear HTML in such cases.
You can choose the library according to the programming language used in the application development. For example, the HtmlSanitizer library for .NET or SanitizeHelper for Ruby on Rails is a good option.
5- Using the HttpOnly flag in cookies
You can use the HttpOnly flag feature in your cookies to reduce the intensity of XSS attacks. In fact, by doing so, HttpOnly flag cookies are not read by JavaScript on the user side and are virtually unavailable.
6. Use a Content Security Policy (CSP)
You can also use a content security policy, or CSP, to reduce the consequences of XSS attacks. This security template is an HTTP response header and allows you to specify the resources allowed to load according to the source request.
7- Continuous scanning of web pages
XSS vulnerabilities may sometimes be identified by developers or through libraries, modules, and software related to your web pages. Therefore, it is better to constantly scan the vulnerability of your web pages using scanners such as Acunetix.
FAQ
What is an XSS attack and what are the main types?
XSS (Cross‑Site Scripting) is when an attacker injects malicious client‑side code (usually JavaScript) into pages viewed by other users. The main types are reflected (payload delivered via a URL/request), stored (payload saved on the server and served to many users), and DOM‑based (vulnerable client‑side code executes injected data).
How can developers prevent XSS in web applications?
Validate and sanitize input, always encode/escape output according to context (HTML, attribute, JS, CSS, URL), use frameworks/templates that auto‑escape, apply a strict Content Security Policy (CSP), set cookies with HttpOnly and Secure flags, and minimize dangerous APIs like innerHTML or eval.
What immediate actions should I take if I discover an XSS vulnerability on my site?
Remove or neutralize the vulnerable code path, patch the root cause (proper encoding and input handling), invalidate affected sessions or rotate sensitive tokens if needed, deploy a CSP and WAF rule as temporary mitigation, and run a full audit to find similar issues.