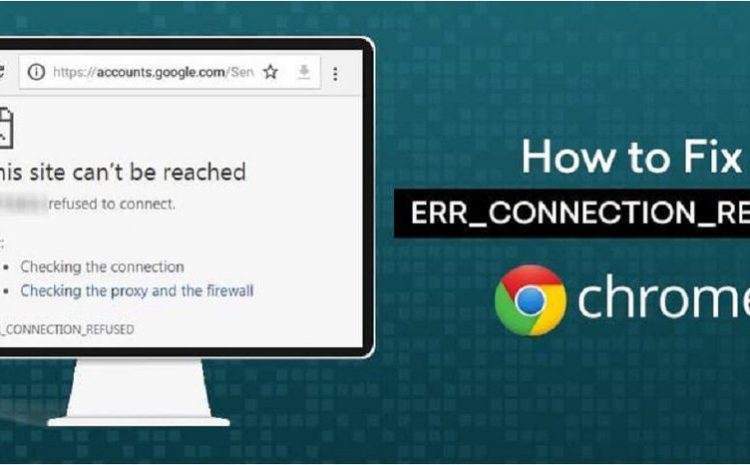
Solutions for Common Network Error Messages: Quick Fixes and Explanations
If Your Network Connection Is Not Configured Properly Or Has A Technical Glitch, You Will Usually See Some Error Messages On The Screen. These Messages Provide Useful Clues About the Nature Of The Problem, Which…