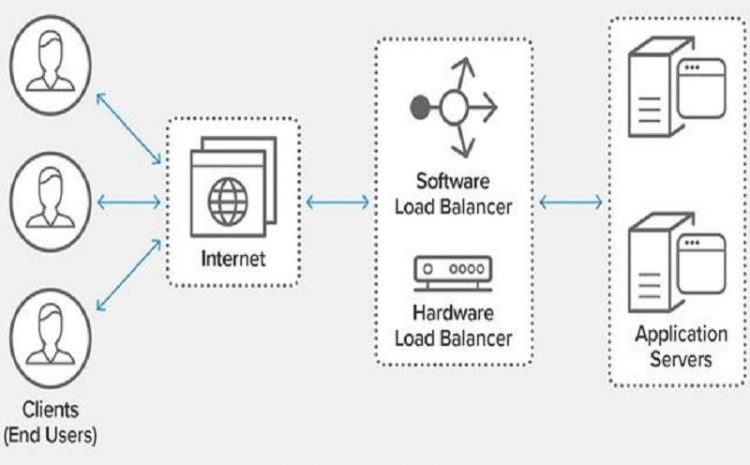
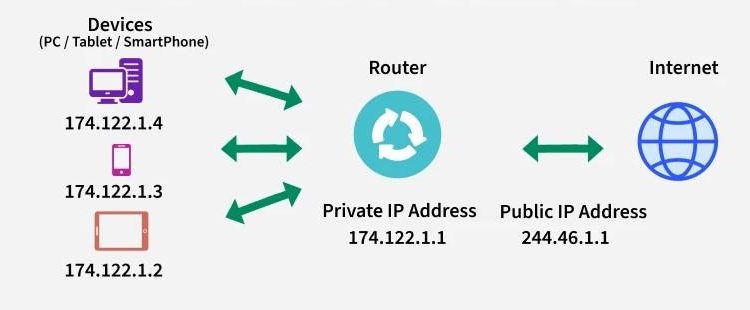
What Is Error 401: Understanding Unauthorized Access
One of the most common error codes is 401 (Unauthorized). This error occurs when the request sent to the desired website or web application cannot be authenticated. Fortunately, this error can be fixed quickly in…