Comprehensive Guide to Active Directory: Key Terms, Definitions & Fundamentals
Active Directory Stores Information About Network Objects By Providing A Hierarchical Structure and efficiently Organizes Domains And Resources. Microsoft First Introduced Active Directory Services, Along With Windows Server 2000, As The Primary Repository For Storing User Information, Computers, Services, And Other Resources On The Microsoft Network.
Although later versions of Active Directory, which came with Windows Server 2003, 2008, 2012, 2016, and 2019, introduced new security features, they still provide similar functionality in some basic services by providing authentication processes.
Focused, integrated, and fully accurate access to organizations, large and small, allows management users and clients to work on the network as accurately as possible.
Before introducing Active Directory, if you wanted to access a shared file on the network, you would need to know the server’s name or IP address, the path of the file, and its name. Although this solution works for small networks, it can not be generalized as the network grows.
A directory service helps solve this problem by mapping all the names of network resources, such as shared files, printers, servers, etc., and matching them to their addresses. Today, an integrated service such as Active Directory is critical to large enterprise networks.
Active Directory supports almost all essential processes and applications, such as resource provisioning, capacity planning, security, network services, resource management, and more.
Active Directory Basics
Directory service
A directory service is a store of information stored in a hierarchical structure. This service allows you to store, search, and manage resources easily and quickly within the network. Each network resource is considered an object. It is important to note that a directory service is more than just a database; it is a service, as its name implies.
A database is a physical storage resource accessible through a computer system, while a directory service uses a database to request and receive object information.
Active Directory
Active Directory (AD) is a directory service for Windows domain networks. Every Windows server has Active Directory Domain Services installed. It is primarily used to store, authorize, and manage information about users and their resources, and can store information as an object.
A resource in a network includes user accounts, passwords, computers, applications, printers, shared files and folders, security groups, and their permissions.
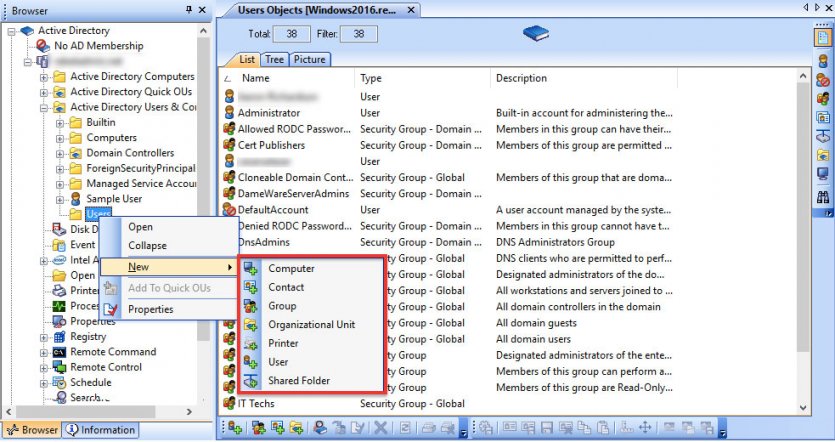
Windows Domain Controller (DC) The Windows Domain Controller is the server on which Active Directory Domain Services rules are installed. It consists of hardware and software that provide AD services.
A domain controller’s main task is to verify the credentials of all users and their resources in a Windows domain network (Figure 1).
The best example of AD is when a user logs into a computer part of a Windows domain. AD checks the identity information in the database, and the user can log in to the computer if the username and password are valid.
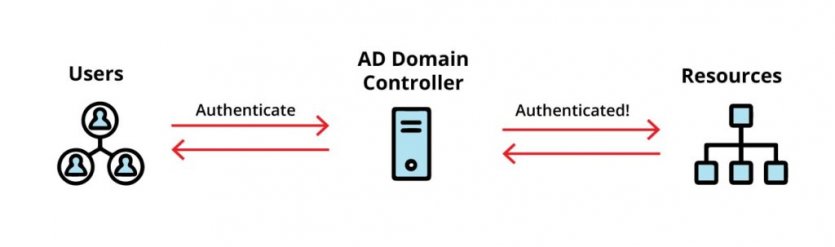
figure 1
Active Directory structure
Active Directory organizes all your network resources into one logical structure. This model is logically independent of the network’s physical structure. In other words, AD does not care about network topology or the number of domain controllers and only organizes resources logically. So, AD allows users to find a resource by name instead of by looking for its source based on its physical location.
Active Directory allows you to organize network elements, such as users or computers, based on a hierarchical logical structure. The forest is at the top of this hierarchy, followed by the trees, which have one or more slopes. Within a domain are organizational units (OU) (Figure 2).
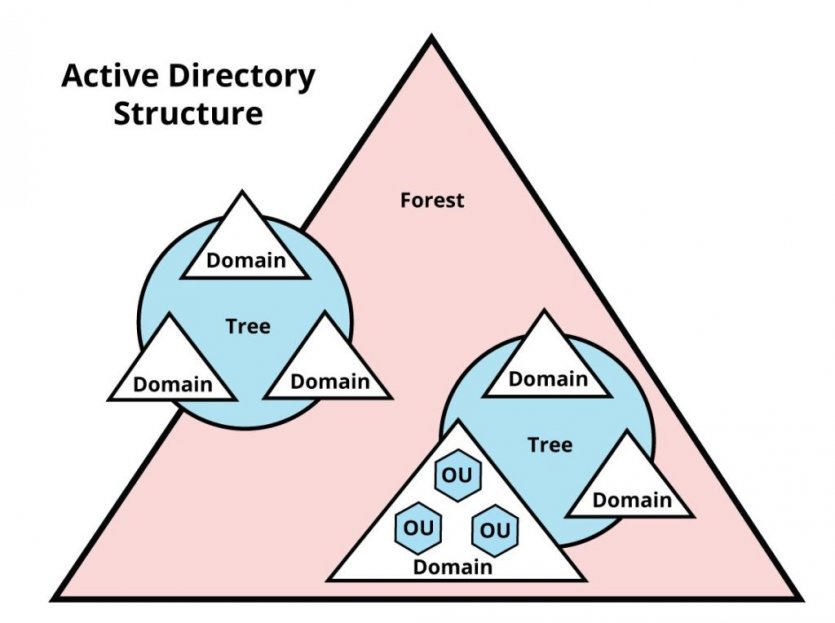
figure 2
Active Directory objects
A grouping of information forms the active directory structure called an object. Each object represents a unique network entity, such as a user or computer, and a set of properties describes that.
For example, attributes such as name, ID, address, phone, and more can identify a user object. Objects are divided into two categories: resources and security priorities. Objects within the resource category can include printers, computers, or other shared devices. The Objects within the security priority category also include users, passwords, groups, or any object that needs authentication.
AD assigns a unique security identifier (SID) to each security priority. A SID allows or denies object access to domain resources (Figure 3).
Objects that Active Directory supports by default include:
- Users: Objects are dedicated to people who need to access domain resources. An account has a username and a password. These include objects.
- Computers: Indicates a workstation or server in the domain.
- Contacts: Contains information about third parties. This object does not have a SID, so it does not belong to the domain.
- Groups: Groups indicate a set of user accounts, computers, or contacts and exist in two types: security and distribution. They make managing objects easier.
- A shared folder refers to a shared server used to share files across the network.
- Printer: This object belongs to a printer shared on the domain.
- Organizational Unit (OU): This group object can include other objects such as users, computers, or groups within the same domain. An organizational unit is used to store similar objects and facilitate their management.
Figure 3
Domains
Domains are the central structural unit of an Active Directory. They are a collection of objects that a database forms using object ID information. An AD domain can have several subdomains called child domains. A domain uses the client-server connection model.
This model provides security because you can assign permissions from the domain (server) to different users or groups (clients). A domain controller uses security services that authenticate and authorize specific resources (Figure 4).
Figure 4
When you first configure an Active Directory, you must create a root domain name. An example of an Active Directory domain name could be ad-internal.company.com, where ad-internal is the name you use for the internal AD domain, and company.com refers to external sources.
Functional levels
Active Directory performance levels determine which domain services can be used on a domain. The above level can also specify the Windows Server operating system version that runs on the domain controllers.
For example, an ideal solution when implementing Active Directory Domain Services criteria is to set the domain performance levels to the maximum value to enable the latest and most significant features available in Active Directory (Figure 5).
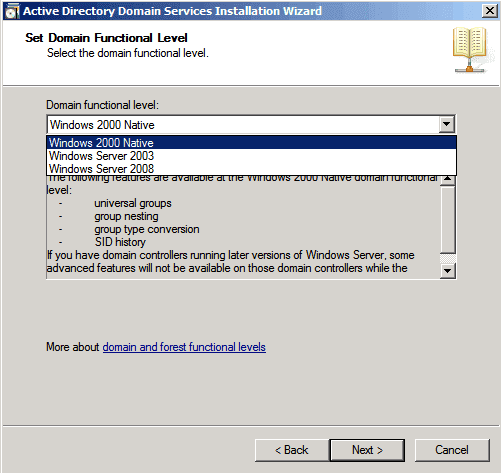
Figure 5
Active Directory Security
Kerberos
Kerberos is an authentication protocol that uses encryption algorithms to ensure the security of client/server communication applications. It uses Kerberos to create authentication mechanisms between the server and the client. This will validate user authentication and grant access to a domain.
The three main elements in the Kerberos system are:
- Key Distribution Center (KDC): The KDC service is the core of the Kerberos server, which handles all tickets. This service runs on all Active Directory domain controllers. When the Active Directory client is authenticated with KDC, the protocol issues a TGT.
- Licensing Ticket (TGT): An authentication file with the user’s IP, a validation period, and a TGT session key. The TGT is encrypted during the Kerberos authentication process.
- Licensing Service (TGS): This service provides TGTs and other system ticketing (Figure 6).
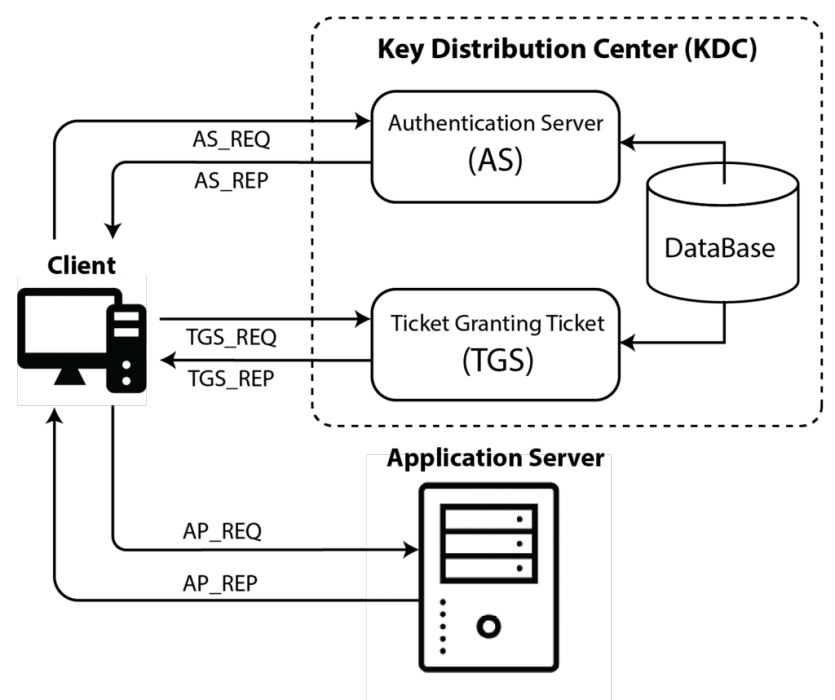
Figure 6
The main letters of the service
Service Primary Name (SPN) The SPN is a unique identifier used in the Kerberos authentication process. It connects a network controller service instance to a login account and can authenticate services to a client application when no service or user account is used.
Active Directory Management Consoles
Its Management Consoles can be used to maintain and use it daily. Some of these consoles are Microsoft-specific, and others are third-party solutions that offer various management capabilities such as automation, reporting, integration with other services, and more.
MMC Snap-ins
Microsoft has integrated many management programs and tools into desktop and server operating systems into a Microsoft Management Console tool (MMC).
MMC creates and opens consoles to help manage all the vital and functional components within a Windows-based network. MMC is responsible for hosting snap-ins, which are management tools that can be used within a single interface. Almost all Microsoft management tools can be implemented as MMC snap-ins.
Active Directory (ADUC) Users and Computers
ADUC is the most popular MMC snap-in for managing various objects. The ADUC console (dsa. MSC) is installed by default during the AD DS installation (Figure 7).
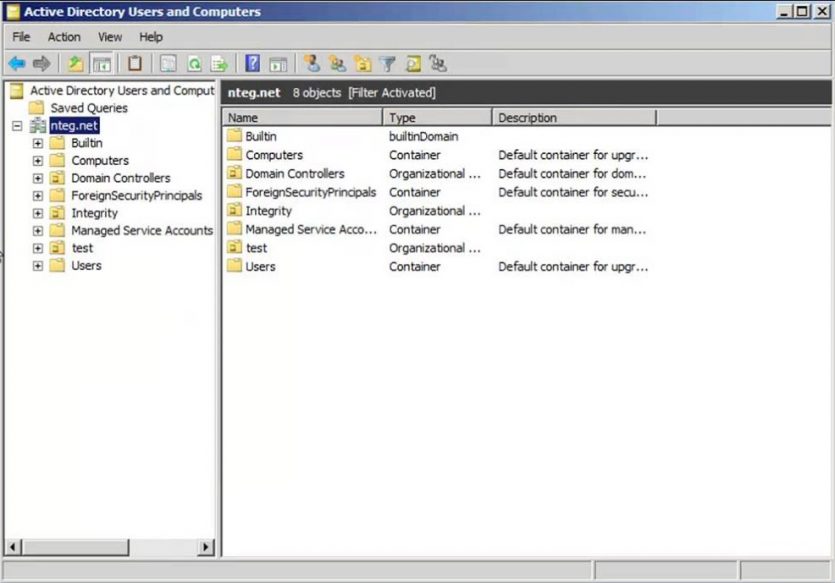
Figure 7
Active Directory Management Center (ADAC)
The ADAC console was introduced with Windows Server 2012. This console can set up and manage user accounts, computers, groups, and more. ADAC has more advanced management capabilities than ADUC, such as Active Directory Recycle Bin, Fine-Grained Password Policy, and Windows PowerShell History Viewer (Figure 8).
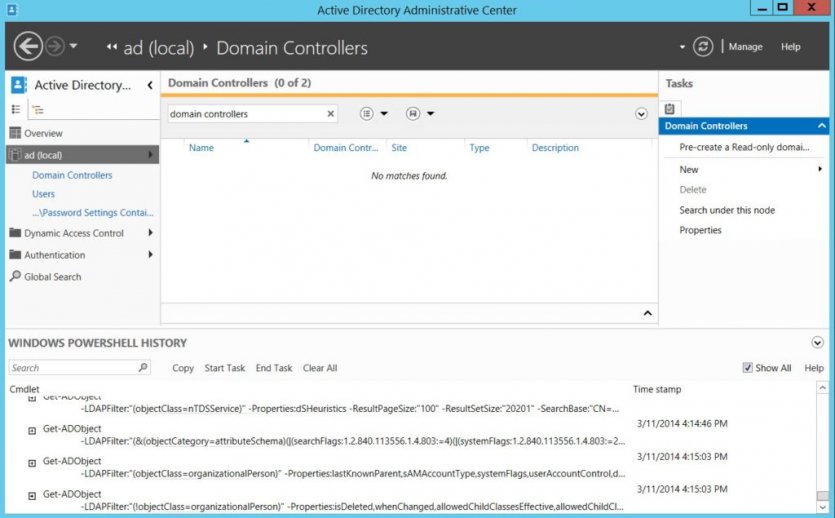
Figure 8
Third-party software for monitoring and troubleshooting Active Directory performance
Third-party software allows you to extend its capabilities and functionality. With tools like SolarWinds Server & Application Monitor, you cannot only monitor Active Directory performance and troubleshoot it, but also all applications, servers, and operating systems within your IT infrastructure.
Figure 9 shows how Solarvins (SAM) analytics tools can provide comprehensive oversight to identify and troubleshoot Active Directory performance. SAM helps you monitor the status of each domain controller and identify problems between sites and domain controllers.
Essential features of SAM include the following:
- View site details
- View Windows logs and events
- Track the status of domain controllers
- Review FSMO criteria
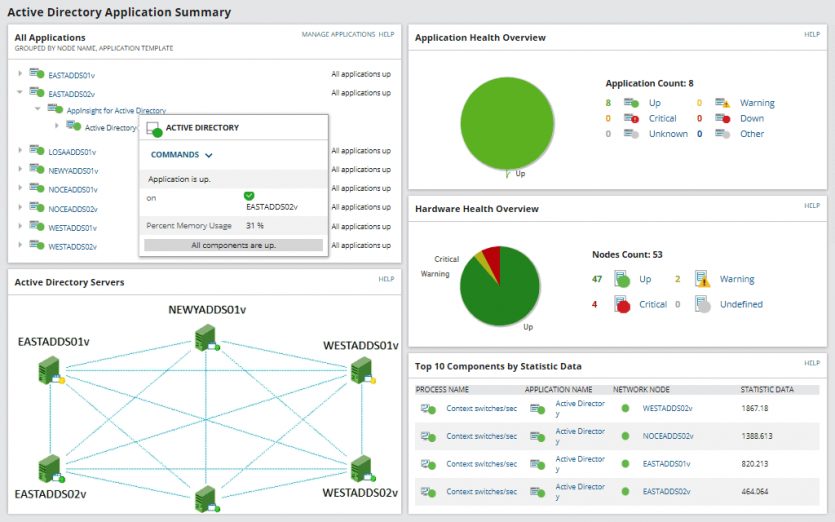
Figure 9
In addition, SAM has related functionalities. These features include a user-friendly dashboard, a reporting and alert system, and task automation scripts.
SolarWinds also offers a compact free software called the Free Admin Bundle for AD, which helps identify and delete inactive users and computers, and add new users to the Active Directory.
FAQ
What is an Active Directory domain?
A domain is a logical group of network resources (users, computers) managed under a single security policy.
What’s the difference between a forest and a tree?
A tree is a collection of domains in a contiguous namespace; a forest is a collection of one or more trees sharing a schema and global catalog.
What is an Organizational Unit (OU)?
An OU is a container within a domain used to organize and manage resources like users and computers logically.