SSH Meaning| SSH Protocol Definition
Secure Shell
Secure Shell, or SSH for short (in English: SSH), is an Internet protocol that enables the exchange of information using a secure channel between two devices connected to the network. This protocol’s two main versions are SSH1 or SSH-1 and SSH2 or SSH-2.
As a very simple definition, SSH can be expressed in such a way that SSH is a powerful and widely used method and, of course, software designed to achieve network security; Every time data is sent from the computer to the network, SSH automatically encrypts it. When the data reaches its destination, it is automatically decrypted. The result will be invisible coding. In this way, the end users will not be involved in the coding and decoding process and can use their secure communication well. The security of the SSH encryption system is ensured by using complex and modern algorithms as far as this system is used in critical and very sensitive systems today. Usually, SSH products consist of two parts: client and server (client/server). The user connects using the settings of the corresponding operator, and the operator is responsible for verifying the identity and accepting or rejecting the connection.
The similarity of Secure Shell with environments such as Bourne Shell or C Shell does not indicate that SSH is also an environment responsible for interpreting commands for the operating system.
Although SSH will not solve all problems, it can be a good solution in many cases. Some of these are:
- A secure user/operator protocol for encoding and transmitting data over a network.
- Determining user identity by password, host, public key or using Kerberos, PGP, or PAM
- The ability to secure insecure network programs such as Telnet, FTP, and all programs based on the TCP/IP protocol.
- It is implemented without any changes in the end user’s use (End User) and can be implemented on most operating systems. (Wikipedia)
Web hosts and SSH access
SSH is an indispensable tool in web hosting, although you may need technical knowledge to take advantage of all the command line interface’s capabilities. You can use it to securely create backups, transfer files, and perform file operations like copying, pasting, or moving files on the server. With the proper permissions, users can execute different commands on a remote host, including shell and bash scripts. SSH gives users the tools to manage servers effectively through a secure, remote connection.
Secure File Transfer Protocol (SFTP) uses an SSH connection with FTP to transfer files securely. This extra layer of security keeps all data moves private and encrypted.
How to use SSH?
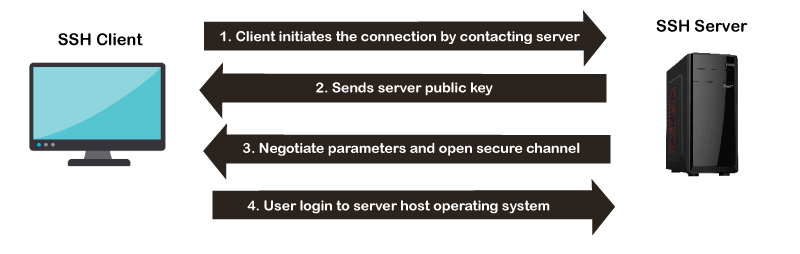
SSH starts with an SSH client like PuTTY (Windows) or OpenSSH (Linux systems) communicating with the server. Next, users enter the remote machine’s IP address, hostname, port number, and user credentials such as username, password, or public key. The remote server runs a daemon that monitors a specific port for incoming client connection requests. Finally, a new SSH session is established if the user’s credentials are correct.
Using a command line-based client like OpenSSH, users run SSH and request the connection using their username and the remote computer’s IP address and port:
ssh username@ip_address -p 22

The client and server exchange identifying information and prompt for the password or public key. After entering the password, the SSH session starts if the user’s credentials are correct.
how ssh works
When to use SSH?
SSH is a valuable tool for managing files and servers remotely, but its usefulness doesn’t stop there. With SSH access and the correct permissions, you can control the remote host’s Operating System (OS) with commands and scripts running through the remote shell. For example, you can view and monitor server and application load, use it to make bulk changes to files or use any other shell command the same way you would on a local machine.
SSH access also presents the perfect opportunity to install the WordPress Command Line Interface (WP CLI). This tool allows you to work with WordPress without a web browser or the familiar WordPress dashboard. Using SSH, you can pass user credentials along with any WP CLI command on a remote server.
Getting started with WP CLI is simple, with just a few lines in the terminal to install it. Once connected through SSH to the WP CLI, you have fast, secure access to all files and directories in a WordPress installation.
It provides an efficient way to perform or even automate specific tasks, such as:
- Core updates
- Managing plugins and themes
- Create XML and database backups
- Find and replace across multiple files or databases
- Change permissions for users, files, directories, etc.
Moderate comments - WP Cron jobs
WP CLI is also a powerful tool for working with WooCommerce. You can create bulk products or lists of orders and customers, manage WooCommerce memberships, and more. Use it to complete any task you typically use the WordPress dashboard for, and take advantage of this helpful tool’s time-saving, simplified interface.
(((Should I use the line?
No, many excellent programs with graphical interfaces exist, such as WinSCP for Windows and Cyberduck for Mac OS X. Please refer to Easy Access for your operating system (Windows, Mac OSX, and Linux) for more information.
Why did you choose Research Data Services SSH?
SSH enables us to provide a service with encrypted access for most operating systems (Windows XP-10, Max OS X, and Max OS X). This will be possible if we provide Windows network drives (which use the SMB/CIFS communication protocol). SSH is trusted and secure, which is why it is used in the high-performance computing community.)))
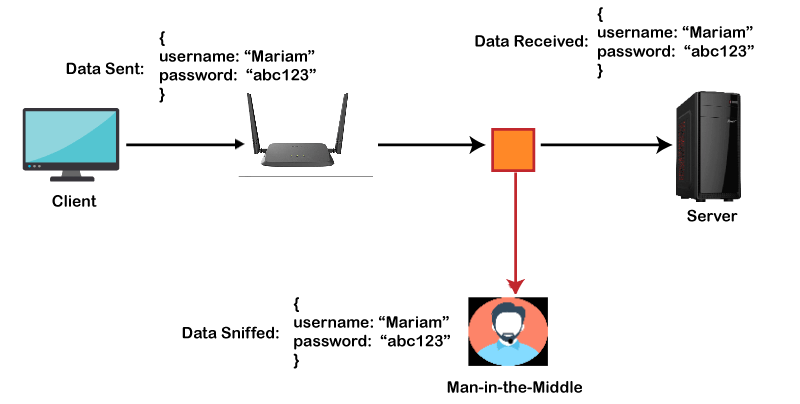
Before SSH:
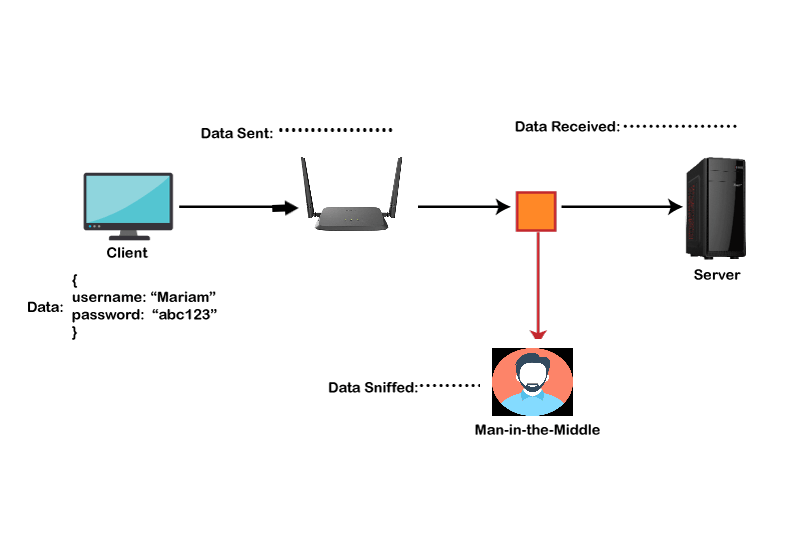
After SSH:
History of the SSH protocol
There are three versions of SSH, as listed below:
- Version 1. x: The first version of SSH was launched in 1995 and was designed by Tatu Ylönen, a researcher at the Helsinki University of Technology in Finland. It was known as SSH-1. There were several problems in this version, and hence it was deprecated.
- Version 2.x: The second version is SSH-2, the current SSH protocol version. 2006 the Internet Engineering Task Force (IETF) selected it as the standard track specification. This version is not compatible with the SSH-1 protocol. Compared to SSH-1, it has better security features.
Version 1.99: Version 1.99 is marked as the initial version of 2.1. This is not the basic version but a way to identify backward compatibility.
SSH protocol architecture
The SSH architecture consists of three well-separated layers. These layers are:
Transport layer
User authentication layer
Connection layer
SSH protocol architecture is an open architecture. Hence it provides a lot of flexibility and allows SSH to be used for purposes other than just a secure shell. The transport layer is similar to Transport Layer Security (TLS) in architecture. The User-Authentication layer can be used with custom authentication methods, and the Connection layer allows the multiplexing of different secondary sessions into a single SSH connection.
Transport layer
The transport layer is the upper layer of the TCP/IP protocol suite. For SSH-2, this layer is responsible for direct key exchange, server authentication, encryption setup, compression, and integrity verification. It acts as an interface for sending and receiving plain text packets of sizes up to 32,768 bytes.
User authentication layer
As the name suggests, the user authentication layer is responsible for client authentication and provides various authentication methods. Authentication is done on the client side. Hence when a prompt for a password occurs, it is usually to an SSH client rather than a server, and the server responds to this authentication.
This layer includes different authentication methods. These methods include:
Password:
Password authentication is a simple way to authenticate. It includes the ability to change the password for easy access. But not all programs use it.
Public key:
The public key is a general authentication method that supports DSA, ECDSA, or RSA key pairs.
Keyboard-Interactive
One of the versatile methods is authentication. In this case, the server sends a prompt to enter information, and the client sends it back with responses keyed by the user and uses to provide a one-time password or OTP authentication.
GSSAPI:
In this method, authentication is performed by external processes such as Kerberos 5 or NTLM, which provides single sign-on for SSH sessions.
Connection layer
The connection layer defines the various channels through which SSH services are provided. It represents the concept of channels, channel requests, and global requests. An SSH connection can host multiple channels simultaneously and transmit data in both directions simultaneously. Channel requests are used at the connection layer to transfer out-of-band channel-specific data, for example, the changed size of a terminal window or the exit code of a server-side process.
Types of standard connection layer channels are:
Shell: Used for terminal shots, SFTP, and exec requests.
direct-tcpip: used for connections sent from the client to the server. forwarded-tcpip: used for links forwarded from the server to the client.
What can be transferred with the SSH protocol?
The SSH protocol can transmit the following:
- data
- Text
- orders
- Files
Files are transferred using SFTP (Secure File Transfer Protocol), an encrypted version of FTP that provides security to prevent any threats.