What Is Hash And Hash Rate And What Are Their Uses? What Is A Hash Function And What Are Its Uses?
What is a Hash?
A hash is a function that converts input from letters and numbers into a fixed-length encrypted output.
Hash functions are used all over the Internet to securely store passwords, find duplicate records, quickly save and retrieve information, and so on.
Hash using an algorithm is created to manage block China in Kryptvkarnsyha space is essential, and indeed the foundation of China’s network is blocked.
Hashing has been instrumental in creating China’s blockchain technology. If you want to understand how China’s Blockchain technology works, you definitely need to understand the concept of hashing.
But what does hashing mean?
In simple terms, hashing converts a value to another using a mathematical function. Hashing is one way to provide security when sending a message (when we want the message to be recognizable only to a specific recipient). To better understand this, imagine the following simple example:
Suppose you want to send an important message to someone and that message must reach that person in the same format. So how do you do that? One way is to send that message several times to make sure its contents are not tampered with. But what if the content of the message is too long?
Verifying each word by doing so is impractical and utterly tedious. It is at this time that “hashing” plays a very important role. Using a hashing algorithm, the data is compressed to a constant size.
For example, if we convert the phrase “crows have a long life” to a hash by the algorithm, we will reach 6e04f289. This value as a hash is known. Hashes play a key role when you want to identify and compare files or data. For computers, it is much easier to compare data as hash values than their original form.
Who uses hashing?

Daily, most users use the hashing process for their passwords. For example, when you try to create an email address and password, the email provider site may not store your password in the same way. Instead, it executes your password through a hashing algorithm and then saves your password hash.
Each time you try to log in to your email, the site converts the password you enter into a hash and compares it to the hash it stores, and you are only allowed to access it if the two hashes match. You are your email.
Hashing on digital currencies

In the Bitcoin blockchain, the ” mining ” process is performed primarily by performing a series of SHA-256 hashing functions. In today’s digital currency blockchain, the hashing process is used to write new transactions, schedule them, and finally add them to the previous block.
When a block of transactions is added to the China block and a consensus is reached between the operators of the various nodes, it will then be almost impossible to reverse the transaction process due to the one-sided nature of hashing. Hashing is therefore crucial to maintaining the integrity of the Chinese bloc.
What is the difference between hashing and cryptography?

Hashing is used to authenticate content and encrypt to maintain the security and confidentiality of data. In the encryption process, a private key is required to access the original and plain text. In general, encryption is a two-way function that includes encryption and decryption, while hashing is a one-way function that confines a simple text to hashes.
The person converts and this process will be irreversible. Hashing and encryption processes are different but have similarities; Both play a very important role in controlling data, messages, and information in computing systems, and both convert or modify data in another form.
How does the hashing process work?
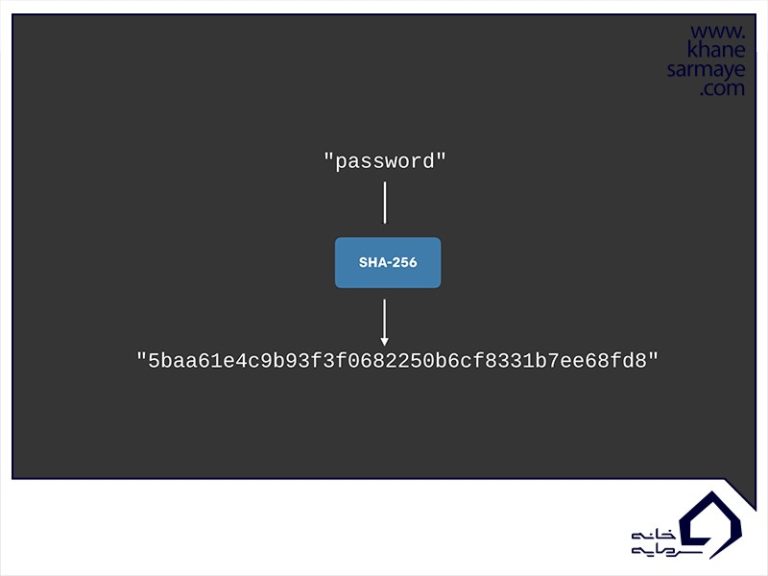
In Bitcoin digital currency, transactions are received as input and converted into a fixed-length output through the hashing algorithm (which Bitcoin uses the SHA-256 algorithm). To better understand this, we use the same SHA-256 algorithm in our example :
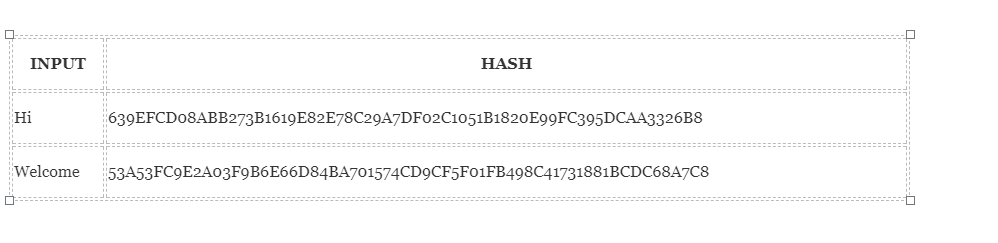
As you can see, for the SHA-256 algorithm, no matter how big or small your input is, the output will always always have a fixed length of 256 bits. This is important when dealing with large amounts of data and transactions. So basically, instead of remembering input data that can be very large, you can just memorize the hash value and track it.
Before explaining more about this, it is best to first look at the features of hashing functions and how to implement them in the Chinese blockchain.
Encrypted functions

The encrypted function is a special class of hash functions that has various properties suitable for the encrypted space. To secure such spaces, an encrypted function must have certain properties. Here are some of the most important ones:
- Feature # 1: Certainty
This means that it does not matter how many times you convert a particular input to a hash through a hash function, because you will always get the same result. This is very important because if you receive a different hash each time, it will be impossible to track its input.
- Feature # 2: Quick Calculations
The hash function must be able to return the input hash quickly. If this process is not done fast enough, the system will not work.
- Feature # 3: Impractical conversion of the obtained hash to input
This feature states that having an output hash, determining the amount of input is impractical. Consider using the word “impractical” instead of the word “impossible”; Because it is not impossible to determine the main input from its hash value. Let us illustrate this with an example:
Suppose you spin a dice and its output is a numeric hash that represents the dice. Now how do you determine what the prime number was? All you have to do is find the hash of all the numbers 1 to 6 and compare them. Since hash functions have certainty, the hash of a particular input will always be constant. So you can easily compare hash values and find the main input. But this is only suitable when the amount of data is very small and when you are dealing with a large amount of data, finding the answer will be very time-consuming and tedious.
-
Feature # 4: Small changes in input change the output hash
Even if you make a small change in your input, the changes that occur in the hash will be very significant. Let us test this example using the SHA-256 algorithm :
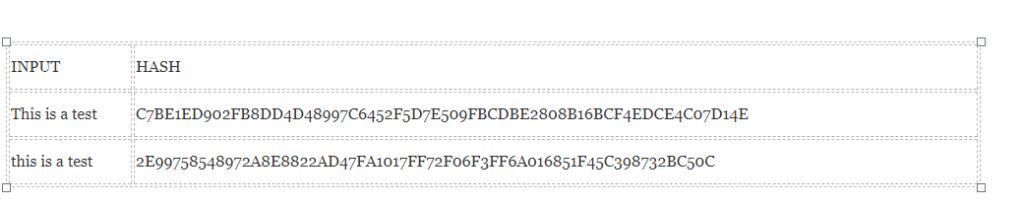
As you can see in the image, even if you only change the first letter of the input, you can see how much this change has affected the output hash. This is a very important feature because it leads to one of the biggest features of the Chinese block, its “immutability”.
- Feature # 5: Hash values will never be equal
Given the two different inputs A and B, it is impractical for hash values A to be equal to hash B. This means that for the most part, each input has its own unique hash. (We remind you again that “impractical” does not mean “impossible” because in reality there are people who do it) .
-
Feature # 6: Regardless of the input, the output will always be the same size
If you convert a single word to a hash, the output will be the same size (for the SHA-256 function, it will be 256 bits). If you convert a book to a hash, the output will still be the same 256 bits. This is another important feature that can save computing time. One of the best examples of this is the use of a hash as a key in a data map. A data map is a simple structure used in computer science to store data.
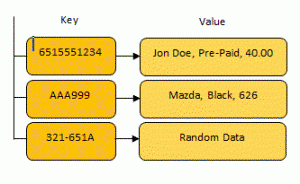
When programs store data in a map, it assigns a key and a specific value to that map. When the program wants to access that value, it can provide the appropriate key to the map and receive the corresponding value. Data maps are very useful because they can find data instantly.
In the map, this key is used as an address where computers can instantly search for target data (instead of spending hours searching for archives in the millions). Because the keys are like addresses, they cannot be too large. If we want to store a book in a data map, we can hash the contents of the book and use it as a key.
What is a Hash Rate?

In simple terms, Hash Rate means how many hashing operations are performed in the bitcoin mining process. In fact, the hash rate indicates the speed of operation of the mining device. When extracting, the higher the hash rate, the better, as this increases the chances of finding the next block and receiving a reward.
What is a hash rate and how is it measured?
The hash rate is measured in seconds (h / s).

What Is A Hash Function And What Are Its Uses?
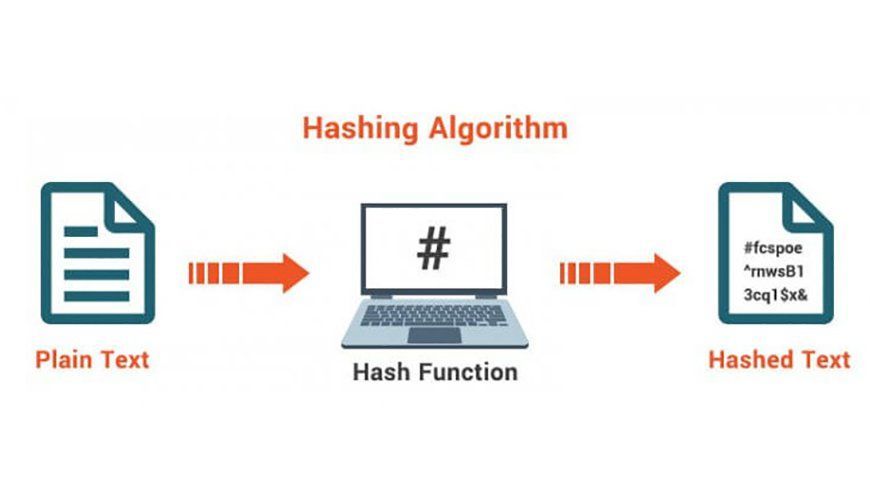
The concatenation function is essentially a mathematical function that compresses the input number into another number. In the field of security and encryption, these functions are one of the most practical and important applications in most security applications.
In the field of security and encryption, the hash function is one of the most useful and practical applications in most security applications. Therefore, in this article, we intend to provide complete information about the hash function. Stay tuned to Visit for this article.
What is a Hash Function?
The concatenation function is essentially a mathematical function (as h (x)) that converts the input number to another compressed number. The important thing about the hash function is that the function input can have any size, but the function output always has a certain size. This output of the hash function is called the message digest or hash value. In the image below, we see a hash function as a black box.
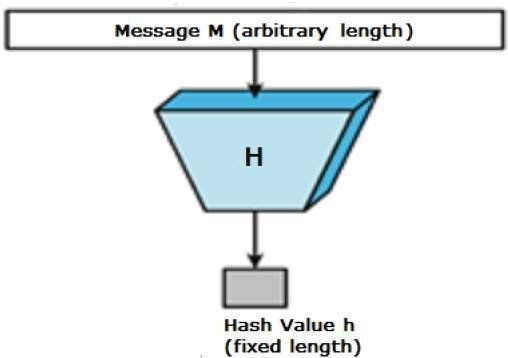
Hash Function Features
The hash function has certain properties, the most important of which is its constant output length. In fact, as mentioned earlier, a data hash function converts any input length to a fixed-length output, and this is what is known as data hashing. Another feature of the hash function is that the output data is generally much smaller than the output data.
This is why the hash function is sometimes referred to as the compression function. It should be noted here that the hash function that has n-bit output is known by the n-bit hash function, which currently has the most popular hash functions of 160 and 512 bits output.
Another feature of the hash function is its high speed. In fact, hash functions of any type with any input length are much faster than symmetric encryption.
What do we expect from the hash function?
For the hash function to function as a powerful encryption tool, it must have the properties and capabilities that we will examine in the following.
1- Pre-Image Resistance
In this feature, we actually expect that it is computationally difficult to reverse the hash function. In other words, we expect that if the output value of the hash function is Z, it will not be practically possible to obtain the X input created by applying the hash function, the Z output.
2- Second Pre-Image Resistance
This feature means that if I have access to input like x and its hash value as h (x), it would be difficult to find a value like y such that h (y) equals h (x). . In fact, for one input and its hash value, it should be difficult to find another input that creates the same hash.
3- Collision Resistance
This feature, also called the collision-free hash function, makes it difficult to find two inputs of any length that generate the same hash.
Since the hash function is actually a compression function that has a fixed-length output, it is almost impossible not to collide. So we can not expect any collision, but we expect it to be difficult to find.
It should be noted that if a hash function is Collision Resistance, it is actually Second Pre-Image Resistance.
The most popular hash functions
MD5
The most popular hash function that has been used for many years is the MD family of functions, which is the most popular among members of this MD5 family. The MD5 function was widely used in software to ensure the integrity of transferred files. But in 2004 it was discovered that a collision attack within 1 hour could compromise the security of this hash function. Therefore, the use of MD5 is no longer recommended.
SHA
This family includes four members SHA-0, SHA-1, SHA-2, and SHA-3. Among the members of this family, SHA-1 is the most used and is even used in SSL. SHA-2, which itself has four members depending on the number of output bits (SHA-224, SHA-256, SHA-384, SHA-512), is a very powerful hash function that has not been successfully attacked to date. Finally, we should mention the SHA-3, which was introduced in 2012, which has a very good performance and excellent resistance to attack.
Applications of the hash function
One of the most important uses of the hash function is to store passwords. In fact, instead of simply storing passwords, the hash value of passwords is often stored. In fact, the password file contains a two-column table that holds the username and password hash value.
Another application of the hash function is to check data integrity. The hash function is actually used to create a checksum on the data file. By doing this, the user can ensure the accuracy of the data. In fact, with this trick, the user will be notified if any changes are made to the main message.












