Who Is a Network Operations Specialist — Roles & Core Responsibilities
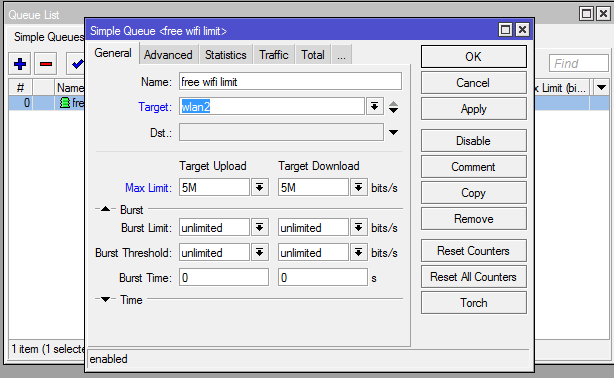
A Network Operations Specialist (or Network Operations Expert) is an Information Technology professional who monitors network performance through a Network Operations Center (NOC). Typically, NOCs are implemented within data centers or large organizations. These specialists…