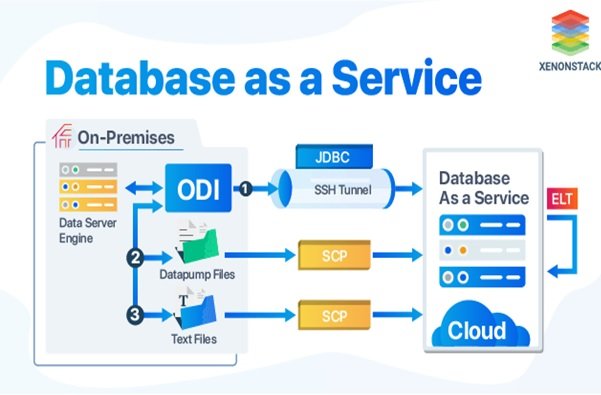
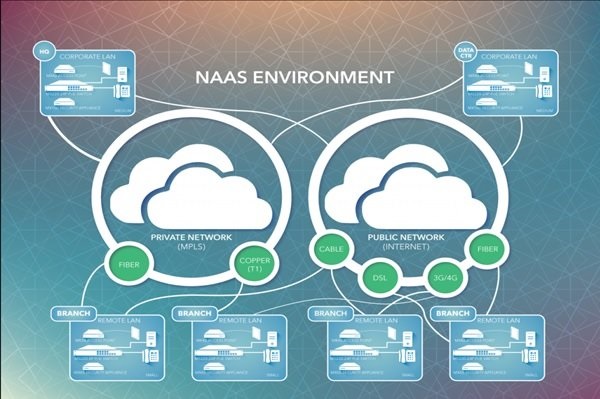
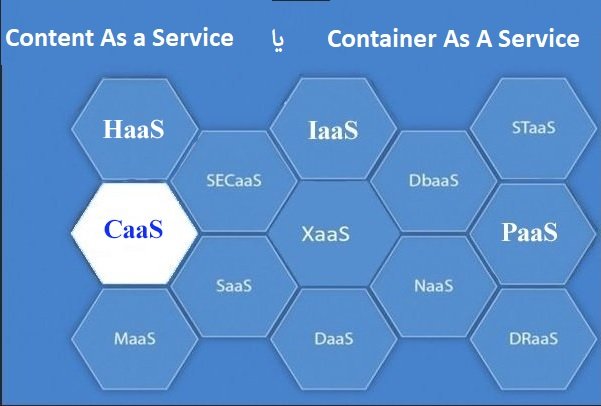
What Is DBaaS (Database-as-a-Service)
Database as a Service (DBaaS) Service. The Term “database as a service,” Which Some Sources Use To Describe The Term “Managed Database,” Was First Introduced By Amazon as a relational database service nearly 12 Years…