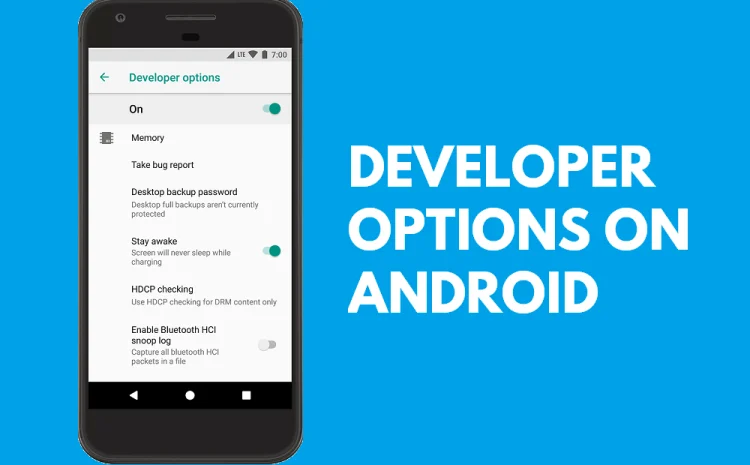
Understanding Android Developer Options: Guide for Users and Developers
Android’s Developer Options is a hidden menu in the Android operating system that unlocks advanced settings for developers, power users, and enthusiasts. We’ll expand on the original content with detailed explanations, practical use cases, and…