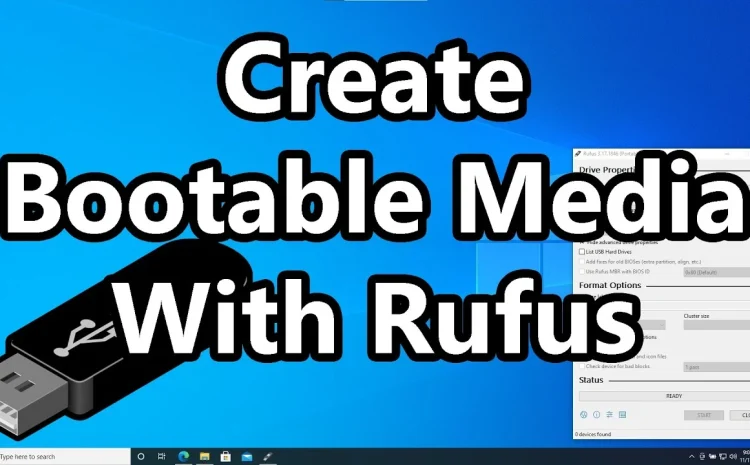
How to Create a Bootable USB Drive with Rufus — Step-by-Step Guide
Creating a bootable USB flash drive using Rufus is straightforward. It allows you to install or run operating systems (e.g., Windows, Linux, or DOS) or perform system recovery tasks on a computer. Rufus is a…