What Is the Role of Scanners in Computer Networks — Functions & Why They Matter
Network experts need a tool, a scanner, to assess the network’s state and ensure that packets are correctly transmitted.
A scanner, which in Persian means scanner, is a computer program or piece of hardware that can intercept and record the flow of information in a network or part of a network.
The scanner monitors the flow of packets across the network and, if necessary, decodes the packets’ raw information, displays the details of the various parts of the packet, and analyzes them according to its own map or other design specifications.
What is package recording?
Scanners capture network traffic, but what is packet recording? Packet Capture is the act of recording data packets on a computer network.
Deep Packet Capture records packets at high network speeds and captures the entire packet (header and body) on high-traffic networks.
Once a packet has been recorded and stored in short-term or long-term memory, software tools perform deep packet inspection to review packet data, conduct legal analysis to determine the root cause of network problems, identify Security threats, and ensure compliance with communications requirements.
Enforce packages and network usage with specified policies. In-depth inspection operations can accompany some deep, closed recording operations.
As a result, all network traffic can be managed, reviewed, and analyzed in real time, while a historical archive of all network traffic can be maintained for future analysis.
Partial packet recording can record packet headers without their data.
This reduces the storage space required and prevents legal problems. However, it still has enough data to reveal the information needed to diagnose the problem.
What are the capabilities of scanners?
On wired networks, depending on the network structure (e.g., a switch), traffic can be received on all or only parts of the network via a machine on the network. However, switches can prevent network traffic from being accessed by other systems.
It may be appropriate to monitor all data packets on a LAN using a network switch called a monitoring port for network monitoring. The purpose of the monitoring port is to reflect all packets passing through all switch ports when systems (computers) are connected to a switch port. For this purpose, a network tap is more suitable than port monitoring.
Taps are less likely to drop packets during high traffic. On wireless LANs, a person can capture traffic on a specific channel or multiple channels using multiple adapters.
Unicast traffic is sent to a machine running Sniffer software on wired and wireless LANs to record it.
Multicast traffic is sent to a multicast group to which a machine listens.
For broadcast traffic, a network adapter must be placed in promiscuous mode to record it. Some snipers support this, and some do not.
On wireless LANs, even if the adapter is in promiscuous mode, packets are usually ignored, not for the service suite but for the adapter to be configured. The adapter must be monitored to see its packages.
The recorded digital data is decrypted into a human-readable format so that users of the protocol analyzer can easily review the information exchanged.
Protocol analyzers modify their capabilities to display data in multiple views, automatically detect errors, determine root errors, generate timelines, recreate TCP and UDP data streams, and more. Some protocol analyzers can also generate traffic and act as a reference.
These can act as protocol testers.
Testers generate the correct protocol traffic for the test and may also detect test errors. Protocol analyzers can also be hardware-based, either in probe format or combined with a disk array.
These devices record packets to the disk array, allowing them to be analyzed without recreating errors.
What are scanners used for?
Internal pointed out. One of the most essential tools used today is TCP dumping.
How do scanners serve network experts?
Since scanners record packets, they provide accurate information to network experts. Among the essential services that scanners offer are the following:
Identify Security vulnerabilities
Analysis of historical data recorded by Deep Closed Recording (DPC) helps determine the sources of unauthorized entry. The DPC can record traffic accessing specific servers and other systems to verify that traffic flows belong to authorized employees. However, this technique can not work as an intrusion prevention system.
Data leak detection
The DPC’s analysis of historical data also helps review content, identify data leaks, and determine their sources. DPC data analysis can also reveal which files have been sent offline.
Network troubleshooting
If an adverse event is detected on the network, the cause or source can be more reliably identified if the network administrator can access complete historical data. The DPC can record all packets continuously on essential network connections.
When an event occurs, the network administrator can accurately access the circumstances surrounding it, take corrective action, and ensure that no more problems occur. This helps to reduce the average repair time.
Legal prevention
Packet recording can be used to fulfill an obligation issued by the LEA law enforcement agency to provide all of the individual’s network traffic. In some countries, Internet Service Providers (ISPs) and voice-over-Internet-Protocol providers must comply with the rules. The DPC records all network activity.
By recording and storing packets, telecommunications agents can provide the legally required Security, separate access to target network traffic, and use a standard device for internal network Security.
DPC detectors can record loss-free traffic without compromising network performance.
However, DPC devices may not provide a document review chain or satisfactory Security for use in this application.
Diagnose data loss
Suppose unauthorized entry causes information to be stolen (such as credit card numbers, social Security numbers, medical information, etc.).
In that case, the network administrator can determine precisely which data has been stolen and which remains secure.
This can be useful for litigation when a credit card company receives a fraudulent request for an unauthorized purchase.
Review Security solutions
Once the DPC detects unauthorized extraction or entry, the system administrator may respond to the attack to prevent it. This helps the manager know if his solution has worked.
Legal issues
Closed recordings for forensic investigations can also be quickly made using open-source tools and systems. Examples of these tools are FreeBSD and dumpcap.
Comparative performance
If performance suddenly drops, historical data can help the administrator view a specific time window and identify the cause of the issue.
FAQ
What do network scanners do in a network?
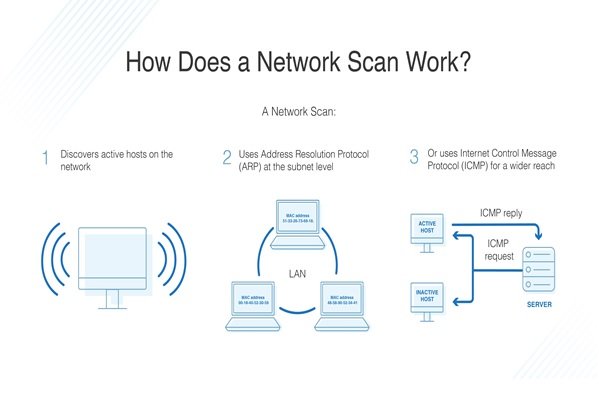
Network scanners detect active devices, open ports, running services, IP addresses and operating systems — building a map of the network and its components.
Why are scanners important for network security?
They identify potential vulnerabilities — such as open ports, outdated services, or misconfigurations — before attackers exploit them, enabling proactive defense and compliance with security standards.
Can scanners help with network management and maintenance?
Yes — by giving a clear inventory of all devices, highlighting unauthorized or rogue devices, aiding in resource allocation, performance monitoring, and helping diagnose network problems efficiently.