What is steganography?
Undoubtedly, you all know that today we are facing an extremely high volume of data and it is added to this data every second. Despite the creation and transmission of this data on the Internet,
the existence of numerous threats to this data is not surprising at all, but in contrast, there are always different methods that can be used to somehow secure the data against security threats.
One of these methods, which is now rapidly evolving, is steganography or cryptography.
What is steganography?
Steganography is basically a method of cryptography. This trick is actually the art and science of embedding a secret message within another message, so that no one but the intended sender and receiver suspects the existence of a secret message. To better understand this, take a look at the diagram below.
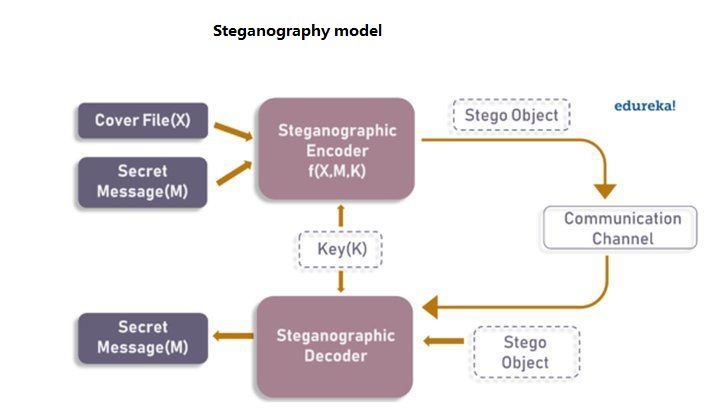
As you can see in the image, a cover message called CoverFile and a secret message called Secret Message are given to the steganographic encryption function. The output of this function is Stego Object, which is very similar to a cover message but has changes that are not easily understood.
On the other hand, to get the hidden message, this Stego Object is given to the steganographic decoding function so that the receiver can get the hidden message from the heart of the obvious message.
Going back, steganography means exposing the hidden message behind a common message and was first used by the ancient Greeks in 440 BC.
In fact,
these people wrote the secret message on a stick and then covered it with wax. The Romanians also used secret inks to transmit the secret text, and the other side used light or heating to see the messages.
Now, however, steganography and its techniques have grown significantly, and we have tools and techniques through this method that greatly help to hide data.
In the meantime, many people consider the two concepts of steganography and cryptography as one, but these two concepts are different.
The difference between steganography and cryptography
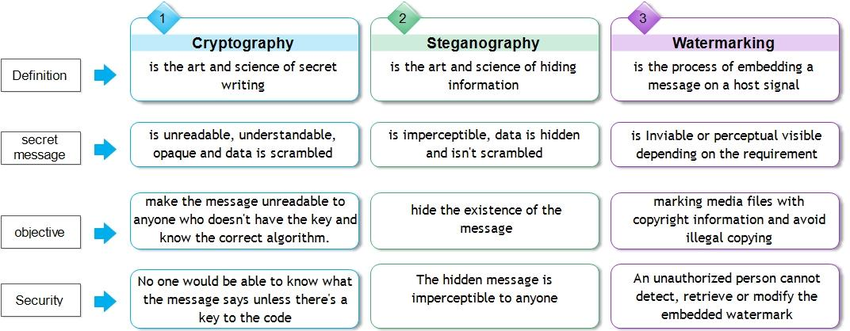
Although both the concepts of steganography and cryptography pursue a single goal, namely the protection of messages and information from third parties, each has a different mechanism than the other.
In fact, in cryptography, your simple information (Plain Text) is converted into encrypted information (Cipher Text) that can not be decrypted without having a key.
Steganography, on the other hand, does not change the data format and only hides it in another message. To better understand this issue, take a look at the table below.
Steganography techniques
According to the same object that covers the hidden message, the types of steganography are determined, which are:
Text steganography:
In this method, information will be hidden inside a text file. This method includes changes to the existing text format,
changes in text words, creating random characters or using text-independent grammars, or creating readable texts.
Image Steganography:
In this method, data will be hidden in an image. In digital steganography,
images are widely used because images have a large number of bits and there are many ways to hide data within the image.
Among the methods of hiding data in an image, we can mention the injection of at least enough bits,
mask and filtering, added pattern encryption, and so on.
Voice steganography:
In this method, the message is hidden inside the audio signals. This method,
like the image steganography method,
is more complex than other methods and includes spectrum expansion, cryptography of least important bits, balance cryptography, and so on.
In this method,
the data is inserted into AU, MP3 and WAV audio files.
Video steganography:
The advantage of this method is the ability to hide large amounts of data within the film. In fact,
the film is a combination of images and sounds that give you practically two steganographies of sound and image.
This method is divided into two techniques: inserting data into the raw film and compressing it in the next steps,
as well as inserting the data in the zip file at the beginning.
Network steganography:
In this method, data is placed inside network control protocols, such as TCP, UDP, ICMP, etc. For example,
you can hide this data in the TCP / IP packet header (in fields, some of which are even optional).













