What is DDOS?
In this article, we will introduce you to DDOS attacks, but first, we need to know what DOS is. DOS or denial of service is a type of denial of service attack in which the attack method is such that an Internet address (website) or a computer or server, etc., is sent to it by sending a very high volume of traffic. The bombardment is placed. These attacks are so damaging that they can disable even a web server. Now you want to know what DDoS is.
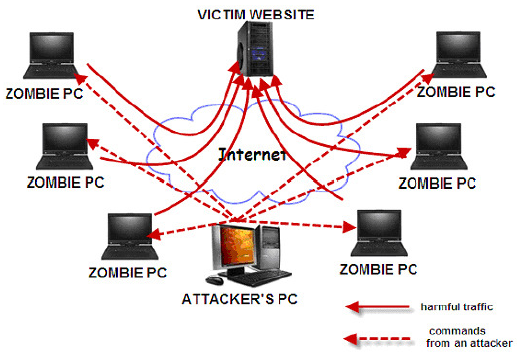
DDOS or distributed denial of service is a type of DOS attack, with the difference that in this type of attack, the hacker directs a very high request or traffic through several different sources by a central controller to the desired server or target, and this It continues to work until all its resources, including bandwidth, CPU, etc., is exhausted and finally become unavailable.
The factors indicating that a server is under attack can be as follows:
- Severe drop in server speed and sites on that server
- Failure to connect to the database of the site
- Sudden excessive consumption of resources such as bandwidth, RAM, CPU, etc.
- Disruption of email service
- And….
In DDOS attacks, because the attack takes place from different sources and places, the ability to fight back will be taken away from the victim; therefore, dealing with this type of attack is much more difficult than preventing these attacks from happening. The main victims of these attacks are web hosting servers, banks, DNS Root Servers, etc., whose goal is not to access user information but only to disable the target.
The following are the main goals of these attacks:
- Severe drop in service speed and quality
- Unavailability of the desired server or site to stop service operations and cause damage
- Complete access interruption to all sites on the target server by attacking the name servers
- Severe disruption in the email service by sending a large amount of spam to the said server
- And …
The following types of DDOS attacks can be mentioned:
- Ping Flood:
This method disables the target server by sending a high ping to the server.
- SYN Flood:
This method creates half-open requests on the server by sending TCP/SYN packets and will lead to the server being occupied and eventually the server will fail.
- Teardrop Attack:
This method overloads the target server by sending strings containing large, unordered packets.
- Application Attack:
This method is used to attack DNS, HTTP, etc. services and by sending a high volume of traffic, it will lead to the failure of the services and finally the server.
Measures that can be taken to deal with or prevent these attacks:
- Timely detection of attacks through continuous monitoring of bandwidth consumption and used resources
- High bandwidth to have more time when the attack takes place
- Use of diagnostic systems
- Use an updated operating system
- Use strong and updated security tools
- Using DDOS Detection and DDOS Mitigation equipment
- Using a strong firewall to block attacking IPs
- Using the right switch and router in networks
- And …
Unfortunately, there is no specific and reliable method to deal with these attacks, but you can prevent serious damage to your server or site by using the above methods. Today, using these attacks using tools like Rasskill and LowOrbit Ion Cannon, most people can execute these attacks without having any special knowledge. But note that this type of malicious attacks is considered a crime in any situation and the wrongdoer should be dealt with . legally is done, get in touch with the hosting company and ask the server manager to identify the IP of the attacking server and block the IP of the attacking server, doing this can solve the problem to a large extent. Also, activating the Cloud Flare system on the site’s domain and hiding the IP server can definitely prevent ddos attacks, which you can use the following tutorial to activate the Cloud Flare system on the site