What Is Crypto Theft And How Can We Prevent It?
Stealing Passwords Or Passwords Is One Of The Latest Tricks Of Hackers To Earn Money Through Users’ Equipment. In This Attack, The User Goes To A Site And The Site Uses The Power Of The CPU Or Graphics To Extract The Passwords.
Sometimes sites install malware or malicious scripts on the victim’s computer without notice so that whenever the malware is connected to the Internet, it uses the CPU power to extract the passwords.
Another way of abusing users’ equipment is anonymous software, especially free crackers. In the above method, hackers provide users with filter breakers for free to connect to the Internet.
While filtering software is running on the victim system, it uses two to five percent of the GPU power to do so.
This is not enough to make the user aware of the suspicion, but when the above value increases or the environment inside the case heats up and the graphics card fans start automatically, the user wonders why the fans have started working.
The above are clear signs of misuse of hardware without the user’s knowledge.
What is Crypto theft?
Crypto theft is an attack in which cryptocurrency extracting software is installed and executed on a user’s device without permission. The software runs continuously without the user’s knowledge and uses a CPU or GPU to extract the passwords.
At the end of the month, the user notices that a large amount of electricity bill has been sent to him, and when he checks the house meter, he wonders why the electricity consumption has suddenly increased.
Bitcoin is one of the most well-known types of cryptocurrencies, but cryptocurrency theft attacks are not unique to Bitcoin, and other digital currencies may fall victim to this pattern of attacks.
Monero, for example, has a special reputation in this field because it is designed in such a way that people can extract cryptocurrencies using ordinary computers and not very powerful equipment.
Monroe has a lot of potential for anonymity, which means that it is difficult to intercept an attacker who installs Monroe extraction software on the victim’s system. Monroe is an altcoin (all cryptocurrencies except bitcoin are called altcoin).
Crystal extraction involves the execution of complex mathematical equations that require a large amount of CPU power.
In a normal crypto theft attack, the extractor software utilizes the CPU to the fullest extent possible.
In this case, the performance of the system is suddenly reduced, because the CPU can not respond to normal requests and generates a lot of heat.
And In this situation, you may notice that the fan is running at a higher speed to cool the system.
If the system is a laptop, its battery will be discharged in a short time, in connection with desktop computers, excessive power consumption slows down the process of calculating the amount of consumption, which ultimately leads to heavy fines.
Since the process of extracting cryptocurrencies with personal computers is not very profitable for hackers, they prefer to use users’ hardware to steal cryptocurrencies to earn a net profit in terms of power consumption without paying extra.
What devices are vulnerable to Crypto theft?
Any device that can run application software can be exploited to extract cryptocurrencies. All you have to do is install the cryptocurrency extractor software on the victim device. Crystal theft attacks can be executed on devices that can run browsers such as Windows, Mac, Linux, Chromebox, Android devices, iPhone, and iPod.
Crypto theft attacks are not always carried out in the form of covert software installation on the victim device, sometimes extracting scripts are installed on the site so that as soon as the site is opened by the user, the malicious script starts using the CPU and when the user leaves the site, the rate Return CPU usage to its original state. Sometimes users install software similar to hackers on their computers.
Some of these software’s start abusing hardware resources by providing free service to users without notice.
This group of software uses the user’s GPU instead of the CPU to do so, and generally uses about 5% of the GPU’s power so that the user does not notice. Another group of cryptographic software has similar functionality to malware.
If a hacker manages to detect a security hole or trick the user into installing malware on their system, it will be able to run the cryptocurrency extractor script in the background of the user’s system and make the most of his system.
Another group of cryptocurrency extractors are designed to be installed on users’ phones and specifically for Android devices.
Stealing passwords in the browser
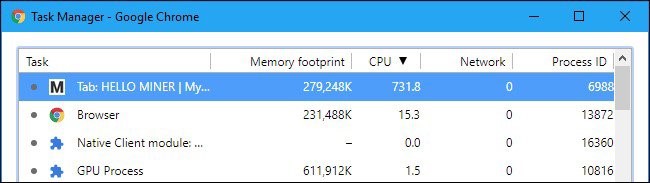
Security experts have recently identified a new type of encryption theft attack that uses JavaScript code and can be executed in web browsers. As long as the web page is open, the JavaScript code can extract the ciphers into the browser and use the CPU power.
The extraction process stops when the corresponding tab in the browser is closed or the user goes to another tab. This model of attack is called encryption theft. CoinHive was the first cryptocurrency extraction script to be noticed by the media and security experts only when it merged with the Pirate Bay online store.
However, many scripts have been designed and integrated into websites that can do just that. In more advanced examples, hackers attack reputable and high-traffic websites, and instead of harming the website, they only add the password mining code to the site.
Of course, some website owners also add cryptocurrency extraction scripts to their websites for profit.
Browser-based cryptocurrency extraction scripts are more dangerous than other examples because they can be run on any type of system, it is enough for the user to open the relevant website by a browser to start the process of abusing the processing power of the user’s device.
Even if the web page is opened via Safari browser on iPhone or Chrome on an Android phone, the scripts can still be executed, unless the user has completely blocked the script from running in the browser, in which case some sites will not open on browsers.
Browser-based cryptocurrency extraction scripts are more dangerous than other examples because they can be run on any type of system, it is enough for the user to open the relevant website by a browser to start the process of abusing the processing power of the user’s device.
Even if the web page is opened via Safari browser on iPhone or Chrome on an Android phone, the scripts can still be executed, unless the user has completely blocked the script from running in the browser, in which case some sites will not open on browsers.
Browser-based cryptocurrency extraction scripts are more dangerous than other examples because they can be run on any type of system, it is enough for the user to open the relevant website by a browser to start the process of abusing the processing power of the user’s device.
Even if the web page is opened via Safari browser on iPhone or Chrome on an Android phone, the scripts can still be executed, unless the user has completely blocked the script from running in the browser, in which case some sites will not open on browsers.
How to prevent password theft attacks in the browser?
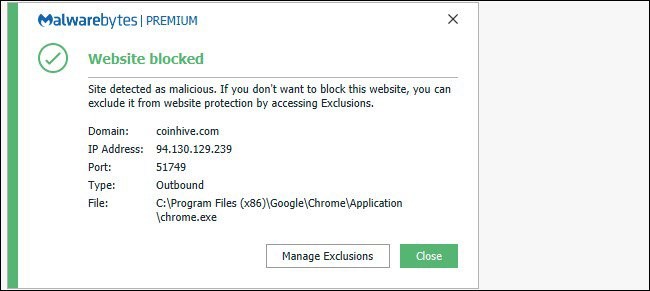
The most effective way to combat crypto theft attacks is to use security software that automatically blocks cryptocurrencies in browsers. For example, Malwarebytes automatically blocks CoinHive and other cryptographic mining scripts and prevents them from running in the browser.
Note that DeanFeder Antivirus for Windows 10 cannot detect and block all browser-extracting malware, and has limited performance.
Some security companies have designed special software or plugins to block the activity of cryptocurrency-extracting scripts for browsers. The above plugins allow users to create a blacklist of cryptocurrency extracting scripts.
Fortunately on mobile devices (Android phones and tablets, iPhones and iPods) when the user leaves a web page using cryptographic extraction scripts (opens a new tab), the operating system does not allow malicious tabs to continue in the background. Consume CPU.
However, if you do not have a security package that does not block the activity of cryptocurrency extractors, there is still cause for concern.
Crypto stealing malware
Crypto theft malware has become strangely common. The ransomware extorts money from users by logging in to the victim system, locking files, and asking for ransomware in the form of cryptocurrencies, but cryptocurrency malware does not behave in this way, hiding in the background of the victim’s systems and silently exploiting victims’ systems.
Whenever the extraction is successful, the result is sent to the hacker. Users only notice the presence of cryptographic mining malware on their system when the system slows down or processes 70 to 90 percent of the CPU workflow. Cryptographic mining malware, like other malware, uses a vulnerability or tricks the user into installing malicious software on their system.
At present, offering to install a free cracker for free access to the Internet is the most common tactic used by hackers.
Stealing cryptocurrencies is a new and less troublesome mechanism than other attack vectors, because hackers infect the victims’ system, but do not do anything illegal, and it is the users who inadvertently and unintentionally install malware on the system, which can cause serious damage Enter the system.
Some programmers try to embed cryptocurrency extractors into legal software so that they can be uploaded to reputable software stores without any problems. Google removes Android apps that hide cryptocurrencies in the background code from the Play Store, and Apple has a similar policy, removing any Mac app with such features from the App Store.
Some programmers try to embed cryptocurrency extractors into legal software so that they can be uploaded to reputable software stores without any problems.
Google removes Android apps that hide cryptocurrencies in the background code from the Play Store, and Apple has a similar policy, removing any Mac app with such features from the App Store.
Some programmers try to embed cryptocurrency extractors into legal software so that they can be uploaded to reputable software stores without any problems. Google removes Android apps that hide cryptocurrencies in the background code from the Play Store, and Apple has a similar policy, removing any Mac app with such features from the App Store.
How to prevent the theft of cryptographic malware?
Cryptographic theft malware has a similar function to other malware. For this reason, we suggest that you pay attention to the following points:
- To protect your device from such attacks, you need to make sure you have the latest security updates installed.
- Software must be obtained from reputable and reputable sources.
- Windows operating system users should use software similar to Malwarebytes to block the activity of cryptocurrencies. A special version of the Mac OS is available for users to block the activity of cryptocurrencies. If you have to download and install software outside the Mac Store, it is best to install Malwarebytes on your system. Fortunately, it is possible to use Malwarebytes with common antivirus software.
- On Android devices, it is better to download the required software only from Google Play Store or Bazaar Cafe. If the software is downloaded from unreliable sources, the chances of being infected with malware are doubled. If the software is downloaded outside of the Google Play Store, Google will not be able to help you much. And If the encryption software is uploaded to the Google Store and users download and install it, Google will be able to uninstall the malware installed on the users’ device if necessary after identifying the program.
The final word
- If you look at Windows Task Manager or Mac Activity Monitor software, you can easily identify troublesome processes whenever you encounter a slow or overheating system. These tools show the name of the processor and the location of the file stored on the hard disk.
- If you find an unfamiliar process that uses too much CPU, google the process name to see if a legitimate process is running or if malware has been successfully installed on the system. Sometimes operating system processes take up a lot of CPU power, but the state is super-transient and after a certain period of time everything returns to normal. While most malware extractors are greedy and consume all CPU power, others use the throttling technique.
- For example, they may use only 50 percent of the CPU power instead of 100 percent so that the victim system does not have a particular problem and the software can run longer without detection. So if in some cases the CPU usage is not at 100%, the cryptocurrency extraction scripts may still be active on a web page and use the system CPU













