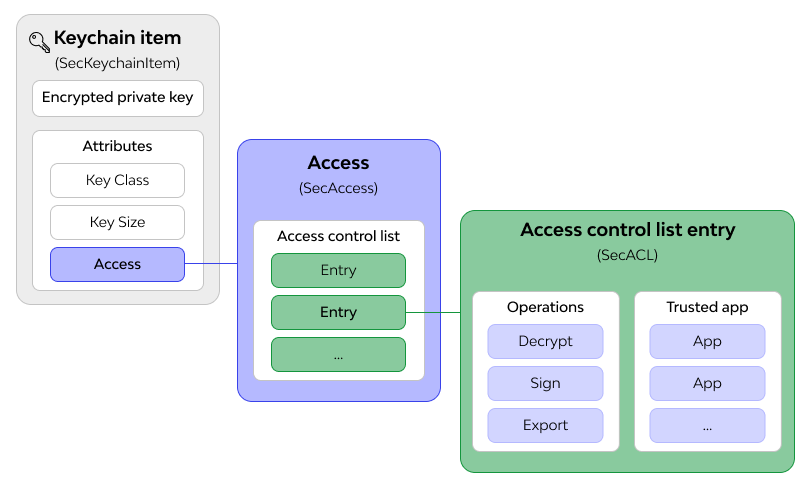
What is an access control list (ACL)?
One way to properly use network equipment is to fully understand it and its other capabilities. This article will examine the different types of access control list and some deployment concepts, including why and when to use them.
What is an access control list?
They are a network filter used by routers and some switches to allow or restrict data flow to network interfaces. When an ACL is configured on an interface, the device analyzes the network data passing through it, compares it to the criteria described in the ACL, and allows or denies data flow. Prevents. Originally, ACLs were the only way to achieve firewall protection. Today, there are many different types of firewalls and alternatives to ACL. However, organizations still use ACLs in technologies such as virtual private networks (VPNs) that specify which traffic should be encrypted and transmitted through a VPN tunnel.
1- Filesystem ACLs:
Use it to filter access to files and/or directories. Filesystem ACLs tell the operating systems that users can use to access the system and limit the amount of access.
2- Networking ACLs:
Network ACLs tell routers and switches which types of traffic can access the network and which activities are allowed.
Access control lists are available in two main categories:
1- Standard ACL:
The access list is created using only the source IP address. Hence, access control lists allow blocking of the entire protocol suite. They do not distinguish between IP traffic such as UDP, TCP, and HTTPS. Generally, they use the numbers 1-99 or 1999-1300 so that the router can recognize the address as a source IP address.
2- Extended ACL:
An extended access list is used to distinguish IP traffic. It generates IP traffic using source and destination IP addresses and port numbers. You can also specify which IP traffic is allowed or denied. The numbers used are 100-199 and 2000-2699.
Why do we use access control lists?
There are several reasons for using ACLs. The main reason is to provide a basic level of network security. ACLs are not as complex as firewalls and do not provide great protection, but they do protect higher-speed interfaces where line speed is important and where firewalls may be limiting. ACLs are also used to restrict updates to routing from network peers and can effectively determine flow control for network traffic.
In general, it can be said that the reasons for using ACLs are:
1- Traffic flow control
2- Limiting network traffic to improve network performance
3—The security level for accessing the network determines whether a user can use the server, network, or service.
4- Monitor the output and input to the system
When do we use the access control list?
As I mentioned earlier, ACLs for routers are not as complex and robust as firewalls, but they offer more significant capabilities. As an IT network or security professional, putting up a defensive wall to protect your network, assets, and data is important and necessary. ACLs should be placed on external routers to filter traffic on known vulnerable networks and protocols.
In this case, one of the most common methods is setting a DMZ or de-militarized buffer zone in the network. This architecture is typically implemented with two separate network devices. An example of this configuration is shown in the figure below.
The outermost router provides access to all external network connections. This router typically has more restrictive ACLs, but access blocks provide additional protection for areas of the global routing table that you want to restrict. This router protects against known protocols that cannot enter or exit your network. Additionally, ACLs must be set here to restrict peer access to the network. They can be used with routing protocols to limit the number of route updates sent or received through network peers.
Most IT professionals place systems that require external access in the DMZ. The most common examples are web servers, DNS servers, and remote access systems or VPNs.
The internal DMZ router includes more restrictive ACLs to protect the internal network from threats. ACLs are often configured with permit and deny statements for specific addresses and protocol services.
What do access control lists contain?
Regardless of which routing platform you use, all these routers have similar specifications for specifying an access control list. More advanced lists have more specific controls, but general guidelines are as follows:
- The name of the access control list (depending on the type of router, their name can be a number or a combination of numbers and words.)
- A sequence of names for each entry
- Description of allowing or denying this entry
- A network protocol and its associated functions or ports: examples include IP, IPX, ICMP, TCP, UDP, NetBIOS, and many others.
- Source or destination targets: These are typically addresses and can be defined as an individual address, a range or subnet, or all addresses.
- Additional flags or identifiers
ACL best practices:
When configuring ACLs, there are a few best practices to follow to ensure security is tight and suspicious traffic is blocked:
1- ACL everywhere:
These ACLs are applied on every interface and security or routing equipment. This is good because you cannot have the same rules for the interfaces and external interfaces that make up your network.
The ACL method on all interfaces is necessary for inbound ACLs, especially rules that decide which addresses can pass data into your network. These are rules that make a significant difference.
2- ACL respectively:
Almost all cases, the ACL booster engine starts at the top and works its way down the list. This has implications for how ACLs work with a particular data stream. One reason organizations use ACLs is that they are less computationally intensive than firewalls and work at high speeds.
3- Work documentation:
Before adding ACLs, determine what you will do and when you will add them.