The Best way to Protect your computer from Viruses (and laptop)
If your computer slows down, the screen is full of annoying ads, your browser settings are constantly changing, or the system Internet is suddenly down. Malware or malware may be installed on your system. . Do not worry about this. The good news is that in this article, you will learn how to remove all types of malware for free through the simple instructions that you follow step by step.
What is Protect your computer from Viruses?
Malware or “malware” is an umbrella or cover that describes any malicious program or code that damages the system. Hackers use malware for various reasons, such as extracting personal information or passwords, stealing money, or preventing owners from accessing their devices.
Malware includes computer viruses, ransomware, worms, Trojan horses, rootkits, keyloggers, dialers, spyware, adware, malicious BHOs, rogue security software, and other malware; Active malware usually uses worms or trojans instead of viruses.
The following is a definition of the most common types of malware:
1- Trojan Horse
A Trojan horse is malware that pretends to be useful, interesting, and entertaining when it damages the system or steals data. Trojans often silently download other malware (spyware, adware, ransomware) onto an infected device.
2- Worm
A computer worm is a type of trojan that can spread or reproduce itself from one system to another and does so in various ways. Unlike viruses, worms do not need a host file to operate. When a computer worm targets a system to run and log in, it damages it. It can remove malicious tasks such as uninstalling other malware, copying itself to physical devices connected to the affected system, and deleting Files and bandwidth consumption.
3- Spyware / spyware
Spyware is a type of malware that is difficult to detect. Spyware collects information about your searches, browsing history, or personal information (such as a credit card number). It often uses the Internet to transfer that information to someone without your knowledge. Keylogger is a type of spyware that monitors your every click.
4. Ransomware
Ransom or Ransomware malware is a threat that prevents users from accessing their system or personal files and requires a fee to be paid to re-enable access.
5- Rootkits
The term “rootkit” comes from the word “rootkit,” which means the package with the most value in the system. A rootkit is defined as software that secretly allows unauthorized operations on the system. A rootkit is changeable and eliminates the usual environmental modules (operating systems or rootkits).
6- Adware
Adware includes an annoying short advertising tool that is supported for software advertising, which is considered the forerunner of PUP software (software that is inadvertently installed on your system). Adware is usually a standalone application that displays ads to the user in various formats: internally or through pop-ups or pop-ups, slider ads, browser pop-ups, banner ads, or web content. Site changed. Advertising revenue shows that these advertising programs are all looking to make money and provide the service or tool they want for free.
Does my pc have malware?
It is not easy today to accurately state whether your computer has crashed or not due to the increasing number of cybercriminals and the use of advanced methods to hide the code and performance of your system’s corrupted programs.
It is impossible to make a clear list of symptoms for a virus system, as they may indicate a hardware or software malfunction. The following are examples of these symptoms that indicate that Your system is infected:
- View Internet Explorer message could not display the page when opening a site
- Locked, hung, or unresponsive by system browsers (such as Internet Explorer, Firefox, Google Chrome)
- Change the browser’s default homepage
- Loss of access to security websites
- Move to other sites instead of your intended site
- See too many pop-ups in the browser
- A new or anonymous toolbar appears at the top of the browser
- Slowing down the computer speed
- The computer locks, hang or does not respond
- New and anonymous icons appear on the desktop
- Spontaneous reset of the computer (except for resets performed for updates)
- View unusual error messages (including messages that indicate a file is missing or corrupted)
- Lack of access to Control Panel, Task Manager, Registry Editor or
How to remove malware from Windows (Virus removal guide)
Windows users can perform this operation using the following instructions, but we have also developed methods for Android and Mac users.
The solution presented in this article may seem confusing to you due to the many steps and programs used. Our efforts in writing this article have been based on simplicity, transparency, expression of all the details, and easy understanding of malware removal instructions.
Please follow all the steps exactly. If you have a vague question or point, you can share it with us.
To remove all viruses, trojans, and other Windows malware, follow these steps:
- 1: Start the system in Safe Mode with Networking.
- 2: Remove viruses, trojans, and other malware using Malwarebytes software.
- 3: Scan the system with HitmanPro software to detect malware and cyber thieves.
- 4: Use AdwCleaner software to remove malicious browser policies and Adware.
- 5: Scan your system again with the Emsisoft Emergency Kit software to make sure that the malicious files and programs are completely removed.
- 6: Clear browser redirects and pop-ups.
Step 1: Set up your system in Safe Mode with Networking
In the first step, to prevent malicious services and drivers from popping up in Windows startup, you must set up the system in Safe Mode with Networking. Using this mode causes Windows to boot in a rudimentary mode with a limited number of files and drivers. You can implement this operation on your operating system through the following instructions.
Instructions for Windows 7, 10 and 11
Before setting up Safe Mode, you must first enter the Windows Recovery Environment (winRE). To do this, follow these steps:
1. Hold down the Windows key, and I open Settings. If these shortcuts do not work, right-click the Start button and select Settings—click Recovery in the right part of this window.
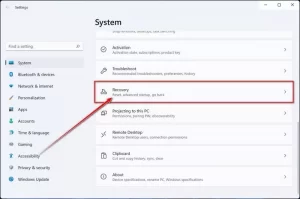
2. In the Advanced startup section, select the Restart now option.
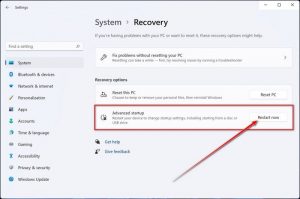
After entering the Windows Recovery Environment, you can start the system in Safe Mode by following these steps:
3. On the Choose an option screen, select the Troubleshoot option.
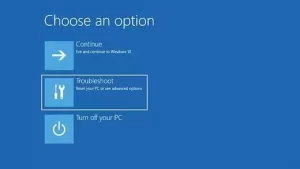
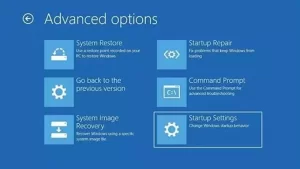
From this page, click the Advanced Options button.
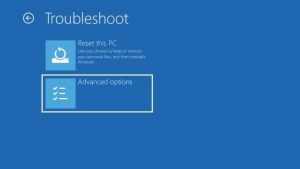
Now click on Startup Settings from the Advanced Options page.
Select the Restart option from this page.
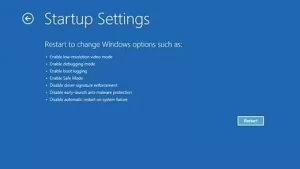
5. After the system resets, different options are displayed. You can now enter Safe Mode with Networking by selecting option number 5 or hitting the F5 key.

6- After the system comes up in Safe Mode with Networking, it is time to download, install and run a scan using Malwarebytes software, explained in the second step.
Step 2: How Malwarebytes software works against trojans, viruses, and other malware
In this step, we will scan the computer after installing Malwarebytes software and examine how this program deals with trojans, viruses, and other software.
The free version of this software is one of the most popular and widely used anti-malware used in Windows, and the reason for this is quite clear. This software can eliminate various types of Windows malware that much similar software can not detect, and you do not pay for this process. The free Malwarebytes program is a great tool for cleaning a system infected with malware, and we recommend that you use it to combat malware.
1- Download Malwarebytes Free software.
Launch your system in Safe Mode with Networking and download the Malwarebytes software. (From here or any other site)
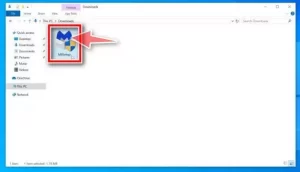
2. Double-click the Malwarebytes stop file.
Once the software download is complete, double-click the MBSetup file to complete the installation process. The downloaded file is usually located in the Downloads folder.
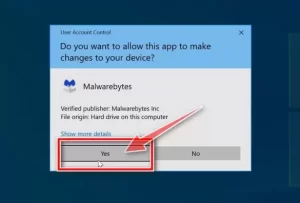
A User Account Control window then opens, asking if you allow Malwarebytes to make changes to your system. Select Yes to continue the software installation process if you see this window.
3- To continue the installation process, proceed according to the given messages.
When you start installing Malwarebytes software, a window called Malwarebytes setup wizard will be displayed, which will guide you in installing this software. The first question you will be asked is about the type of computer you want to install the software, which you must choose from the options Personal Computer or Work Computer.
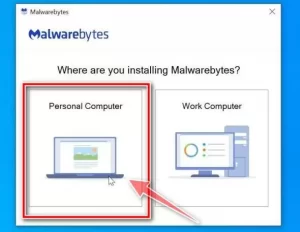
Selecting the Install option will start installing Malwarebytes on your system on the next screen.
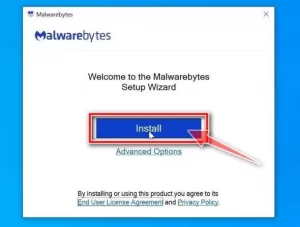
After completing the software installation process, the program’s welcome page is displayed on the Welcome to Malwarebytes screen. Click the Get started button.
4. Click on Scan
Click the Scan button to start the scanning process with Malewarebytes software. The software automatically updates your database and then scans your computer.
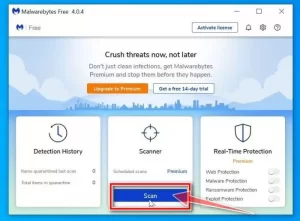
5. Wait for the scanning process to complete
Malwarebytes scans your computer for malware and other malware. This process takes a few minutes, so it is better to spend your time doing something else and, from time to time, look at the software and control the scanning process.
6. Click on the Quarantine option
After the system scan is completed, a window will open displaying malware detected by the software. To delete malicious files, click the Quarantine button.
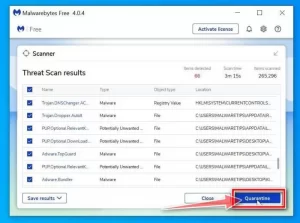
7- Reset the system
Malwarebytes software now removes all malicious files and registry keys. Also The software asks you to reset your system to complete the cleanup process.
Start the system normally at the end of the cleanup process (or you can exit Safe Mode with a simple reset) and follow the instructions. Because the cleanup process was done in Safe Mode, we recommend that you scan your system again to ensure that all the malware has been removed from your computer.
