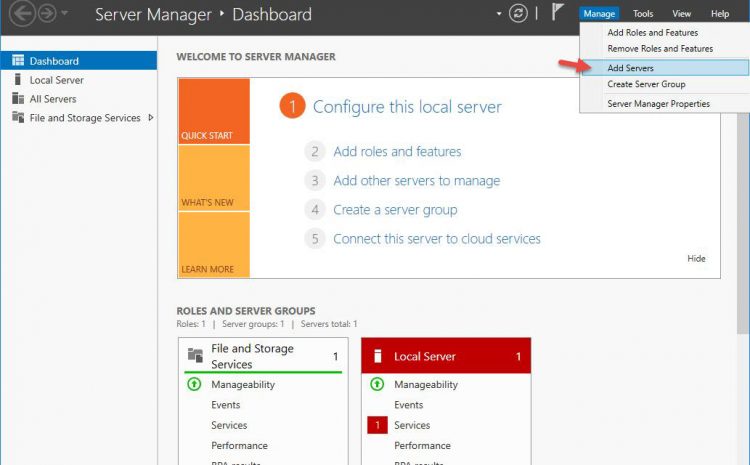
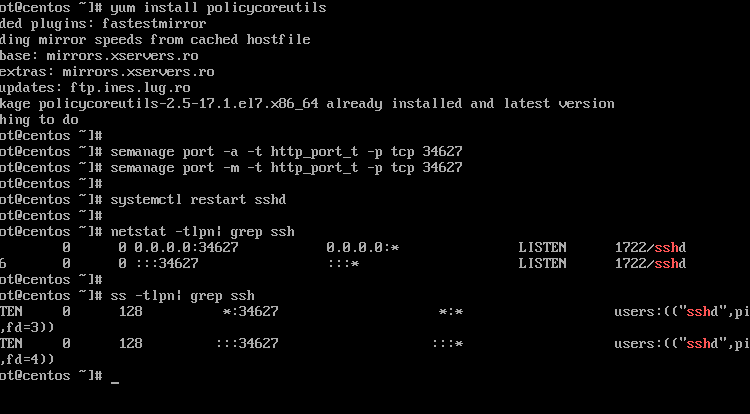
How to Connect to the server remotely with these Applications?
The best mobile apps to connect to the server Today, with the advancement of computer technology, not only has this technology become a big part of our human lives, but with its increasing growth, its…