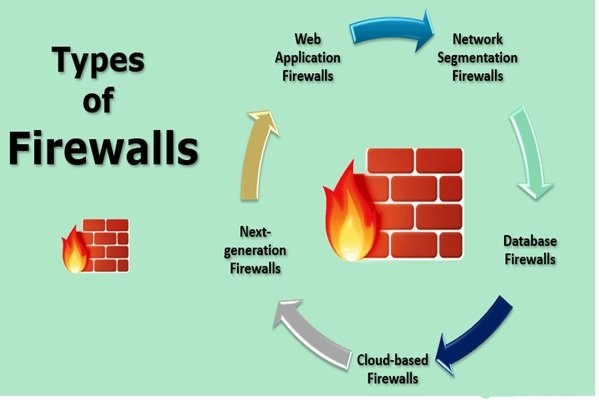
What Is Dynamic Programming — And Why Learning It Is Extremely Valuable
When we think of a dynamic programming problem, we must understand the subproblems and how they relate to one another. In this article, we will review dynamic programming. Algorithms and data structures are integral components…