How to Set Passwords on Cisco Devices — Key Points & Best Practices
One Of The Most Important Things To Consider As A Network Expert Is The Issue Of Controlling And Monitoring People Who Have Access To Network Equipment Settings.
Cisco Devices: You need to know how to use Secure Shell SSH in conjunction with Cisco equipment and how to use access control lists to allow or block incoming or outgoing traffic to the network.
Configure equipment passwords
One of the first steps to secure your network equipment is properly configuring passwords on essential devices such as routers and switches. In this section, two types of passwords can be configured. The first password to be set is the password that an administrator enters when switching from user EXEC mode to premium EXEC mode using the Enable command.
The enable password is stored in an encrypted configuration file, and the second enable secret is stored in an encrypted configuration file. If you set both, you must use a secret password to access EXEC privileged mode, as it takes precedence over the other.
Use the enable password command to configure the unencrypted password and the enable secret command to configure the encrypted password (Figure 1).

figure 1
To see the applied configuration, call the ” show running-config command. You will now see that the enable password is not encrypted, and the enable secret is stored encrypted in the configuration file (Figure 2).
When working with Cisco equipment, remember that you can usually delete it by adding the word No to the beginning of a command. For example, if you want to delete a secret password, use the no enable personal knowledge, and if you want to delete an active password, use the no enable password command.
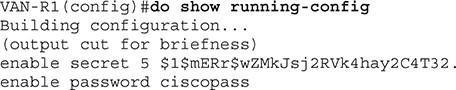
figure 2
Auxiliary Port Security and Auxiliary Port
The following password is the console password, which must be entered whenever a person attempts to connect to the device’s console port. The network administrator must enter the console port password before entering EXEC privileged mode. If the password is secret, you must use a personal password to access EXEC select mode. To configure the console password, use the syntax shown in Figure 3:
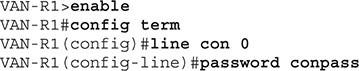
Figure 3
Once you set up your password, you need to do something meaningful. By executing the previous commands, if you connect to the console port of your device, you will notice that you will not be asked for the password. After setting the password, you must use the login command to show the Cisco device that it is necessary to access the authentication port and enter the password. To do this, you must call the following command:
VAN-R1 (config-line) #login
Typically, some Cisco routers have an auxiliary port (AUX) next to the console port. The additional port is used as a backup line, where a modem is connected so that you can access the router remotely and make management changes.
Usually, you communicate with the router remotely using the router’s IP address and the SSH protocol. Still, if something goes wrong and you fail to communicate with the router, you have the chance to connect a modem to the router’s auxiliary port. Then dial. The point to note in this section is that you need to set a password for the port; if you do not do this, there is a possibility that someone can connect to it.
To configure the password on the auxiliary port, enter global configuration mode, then AUX Line mode, and set the password with the commands shown in Figure 4. It is necessary to explain that, as before, you still have to use the login command. If you do not run this command, the configured password will have no effect, as the device will not perform any authentication for this port (Figure 4).
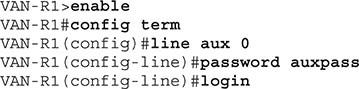
Figure 4
Securing VTY ports
To manage the device remotely with telnet or SSH, you must configure a password on the VTY terminal ports. To configure the password on VTY ports, we need to go to VTY mode and set the password. As before, use the login command to force the device to authenticate by prompting for a password when connecting to ports (Figure 5).
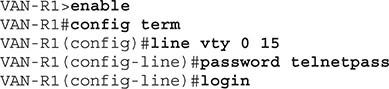
Figure 5
The critical thing to note is that you should use SSH instead of telnet because telnet creates a simple communication channel that sends all the exchanged messages in clear text to the devices. It is also true for authentication traffic, so anyone can view this information, including the username and password you entered to access a device. In contrast, SSH encrypts all exchanged data.
User configuration
When setting up security mechanisms for console ports, auxiliary ports, or VTY ports, it is best to use a combination of username and password instead of a single password to improve the device’s security. Of course, you need to know how to manage the list of users on the Cisco device and assign access levels.
Create user accounts
Network professionals create a list of usernames and passwords stored locally on your Cisco device. To do this, you need to call the username command and enter the username and password parameters as shown in Figure 6:

Figure 6
Next, you need to call the local login command for each port that will use this list for authentication. In the local login command, the word login means mandatory authentication, while local means using a local database of usernames and passwords for authentication. For example, the controls below the console port are configured to enter a username and password whenever a person wants to access the device locally (Figure 7).
![]()
Figure 7
Privilege Levels
Cisco equipment supports various scoring levels. To be more precise, there are 16 scoring levels in Cisco devices that can be adjusted from 0 to 15. 0 is the lowest, and 15 is the highest. When you are in EXEC mode, you have a rating level of 1, which is why you can not make changes to the device. When you enter the premium EXEC mode, your score level is raised to 15, indicating full managerial access. It would help if you switched to the premium EXEC mode to make changes to Cisco devices.
One of the exciting features of the scoring discussion is that you can assign a score level to a user and then link that score level to a command so that the user can execute a command. We must use the privilege parameter and the username command to give the user a story. The syntactic composition of this work is as follows:
VAN-R1 (config) #username adminguy privilege three password adminpass
If you want a user to be able to execute a particular command, you must change the score level for the command for the user. To do this, we use the following syntax:
VAN-R1 (config) #privilege exec level 3 show running-config
In this example, I assigned the show running-config command to level 3 so that the user has the minimum score level to execute that command. If you do not know the status of your privileges, call the show privilege command (Figure 8).

Figure 8
In this case, when it is in EXEC user mode, it has a score level of 1, but when it goes to the excellent EXEC mode, it receives a score of 15.
Encrypt passwords
Now that we have some exciting information on configuring passwords on Cisco equipment, it’s time to learn how to store them in startup-config and encrypt them. To view the configuration file’s contents, call the show startup-config command. In this case, we see information similar to Figure 9.
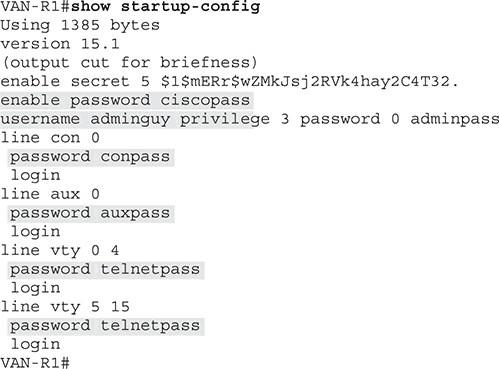
Figure 9
In the configuration file, you will see that all passwords, except the secret password, are stored in plain text. If a person can physically access the router, they can view the configuration file and passwords. It is enough to use a simple command to encrypt all passwords in Cisco configuration files (Figure 10).

Figure 10
When the command is executed, plain text passwords are encrypted in the configuration file. Now, if a person accesses the router, they will not be able to see the passwords.
SSH configuration
Another essential security feature to set up on Cisco devices is configuring the device to use SSH instead of telnet. SSH uses TCP port 22 and encrypts all information exchanged over the communication channel, including usernames and passwords sent by administrators and users to Cisco equipment. Telnet uses TCP port 23 and does not encrypt communications. SSH configuration is done in three steps:
- If the hostname does not already exist, it must be configured on the router.
- In this step, you must create a username and password that administrators can use to authenticate when connecting to the device via SSH.
- In the third step, you have to configure the domain name on the device, as this name is used to generate the encryption key.
The commands you need to run to configure SSH are shown in Figure 11.

Figure 11
The nice thing to note is that the Cisco device you want to configure SSH must use an iOS version that supports encryption. After completing the steps above, call the crypto key to generate the RSA command to create the encryption key (Figure 12).
Note that the key name is created based on the hostname and domain name that you have configured. In Figure 12, when asked about the number of bits used for this purpose, accept the default value of 512. 512-bit encryption is very secure, and hackers can not easily break it.

Figure 12

Figure 13
Now that you have the encryption key ready, you can configure the VTY ports to accept connections only via SSH. In the example shown in Figure 13, note that we configure authentication using local usernames on the device, then run the SSH input transport command so that the device uses only the SSH protocol on the configured ports.
At this point, Cisco will no longer accept Telnet-based communications for remote management. However, if you want to improve the level of security, use access control lists to restrict IP addresses that can communicate with the device through the SSH protocol.
FAQ
How do I secure privileged access on a Cisco device?
Use the “enable secret ” command — it stores the password encrypted and protects privileged EXEC mode.
How do I secure console or remote login to a Cisco switch or router?
Under global config, use “line console 0” or “line vty 0 15”, then set “password ” and “login” to require login for console or remote access.
Why is password encryption important on Cisco devices?
Because plain‑text passwords in config files can be exposed if the config is accessed; encrypted/hashed passwords reduce risk of unauthorized access.
