How to protect infrastructure against DDoS attack?
One Of The Important Concerns Of Network And Security Experts Is The Lack Of Access Of Users To Commercial Services And Infrastructure.
By implementing a distributed denial of service (DDoS) attack vector, hackers can make normal users unable to use the services of a company or organization without worrying about being tracked and detected.
This issue has made commercial business managers question whether there is a solution to deal with this model of attacks or whether it is possible to use special services or equipment to deal with this model of attacks.
One of the most critical questions for business owners is what DDoS mitigation is.
The reality is that from small networks to large networks, they are all vulnerable to DDoS attacks. Therefore, you should always use the DDoS Mitigation solution to protect against network attacks. This can be done using physical equipment or cloud solutions. Using physical equipment is costly and may not be applicable in all cases, but cloud-based
DDoS Mitigation can offer a higher level of protection. This article will tell you about the DDoS attack vector and what new solutions are available to deal with this attack vector.
What is a DDoS attack?
Distributed Denial of Service attack refers to a set of malicious actions that are carried out to disrupt the regular traffic of a server, service, or network in a targeted manner. Hackers try to disrupt an organization’s infrastructure to disrupt normal company traffic. This is mainly done for two reasons; The first reason is to slow down the speed of the site so that it takes a lot of time to respond to users’ requests, and the second is that the site stops moving entirely, and users do not receive any response from the site. In short, a DDoS attack creates unexpected and heavy traffic to disrupt the normal functioning of websites hosted by servers. In general, we should say that a DDoS attack’s like unexpected traffic entering a highway and blocking it, preventing regular traffic from reaching its destination.
Today, DDoS attacks are used to gain access to corporate data, knock out competitors’ online businesses, disrupt operating systems, and more. Typically, DDoS attacks are launched through a wide range of IP addresses that hackers have previously infected. This issue makes it difficult or even impossible to identify the person or persons who implemented this attack. Hackers can execute DDoS attacks by using different types of devices and even IoT equipment. This is done by infecting equipment connected to the network with malicious scripts and controlling them remotely. These infected devices are called “zombies,” and a network of these infected devices is called a “botnet.”
After building a network of bots, hackers can send malicious instructions to infected computers to attack their intended targets. When bots target a target server or network, each bot sends requests to the target IP address. Submissions will continue to be shipped until the server or network can no longer perform routine operations. Since each bot is an Internet device with a valid IP address, it is difficult for most network administrators to separate malicious traffic from regular traffic.
How to detect a distributed denial of service attack?
When a distributed denial of service attack occurs, it shows tangible signs, the most obvious of which is a sudden slowdown of the site or Internet services. However, because most DOS attacks are very similar to Internet disruptions, network experts must do more to identify the attack. For this purpose, traffic analysis tools should be used. Among the clear signs of distributed denial of service attacks, the following should be mentioned:
- Increasing traffic associated with a specific IP address or range of addresses.
- Abnormal increase in the traffic of users who have a specific consumption pattern. To be more precise, the request is sent from a particular device, geographic location, etc.
- A sudden increase in requests to refer to a particular page or site.
- Abnormal traffic patterns, such as visiting a specific page at unpredictable hours.
By considering the above, it is possible to prevent the successful implementation of cyber attacks to some extent. Of course, you need more analysis to determine if a distributed denial of service attack has occurred.
Types of distributed denial of service attacks
To have a detailed understanding of different types of distributed denial of service attacks, it is necessary to have basic knowledge of networks and communication channels. Distributed denial of service attacks is of different types, each targeting various devices and components connected to networks. Computer networks are composed of other parts and layers, and each layer serves another purpose. The OSI model shown in Figure 1 is a conceptual framework that describes the function of each of these seven distinct layers. In general, distributed denial of service attacks are divided into the following three main groups:
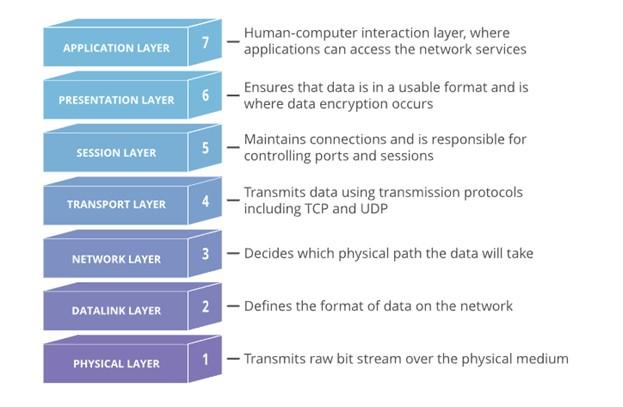
figure 1
Application layer attacks
This attack is sometimes known as a layer seven distributed denial of service attack, which refers to the application layer in the OSI reference model. This group of attacks targets the layer where websites are defined on the server and deliver packets of information in response to HTTP requests. This attack aims to consume the target’s infrastructure resources quickly. So, no freedom source is available to respond to users’ requests,t
Implementing and executing a simple HTTP request costs nothing on the client side, but the response the server sends does; Because, in most cases, the server needs to load some files and execute database queries to create a web page. Because it is difficult to distinguish malicious from legitimate traffic, it is also difficult to defend against Layer 7 distributed denial of service attacks. Figure 2 shows an example of an application layer attack.
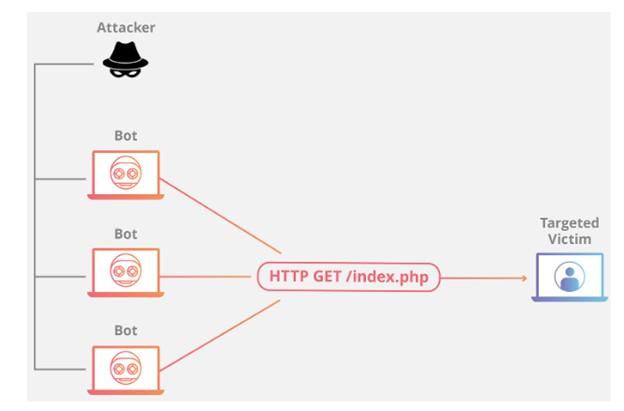
figure 2
HTTP Flood
This attack is made by sending massive HTTP requests to the server. This attack can be classified into two types: simple and complex. Simple attacks on a server or network are made through an IP address. While in sophisticated attacks, random URLs are used.
Protocol attacks
Protocol attacks exploit weaknesses in Layer 3 and 4 of the protocol stack to make the target unreachable. These attacks are also carried out to consumer resources and essential network equipment and keeping firewall keep so that there is a significant disruption in the functioning of services. Figure 3 shows an example of how to implement the above episode.
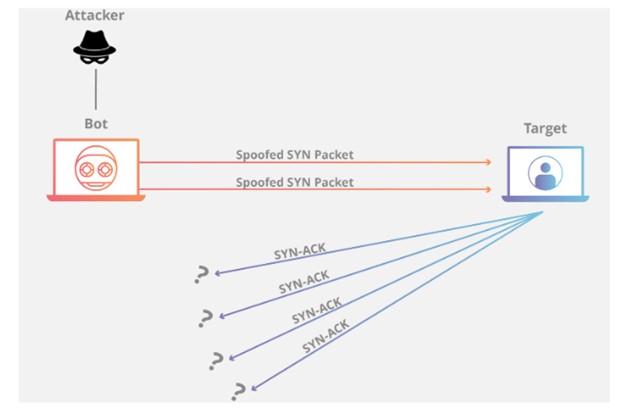
Figure 3
SYN Flood
This attack is used by sending many TCP requests (initial connection requests) through fake IP addresses to avoid accessing the TCP protocol and causing problems in the server or network.
This attack is similar to someone who is in the warehouse and receives a request from the store department, which is responsible for handling customer requests. After preparing the package and sending it to the store, waits to obtain the final approval from the accounting department. But during this time, he received many other requests. Now, if this process continues, the worker will face a wide range of demands and will no longer be able to perform the assigned tasks; it cannot handle more requests, and, as a result, the recommendations of customers remain unanswered.
Volumetric attacks
In the above attack, a large amount of data is created using an amplification pattern to create significant traffic and send it to the target. This attack vector consumes all the available bandwidth between the target and the user, causing the congestion problem. Usually, a bot network is used in this model of attacks. Figure 4 shows how to implement the above episode.
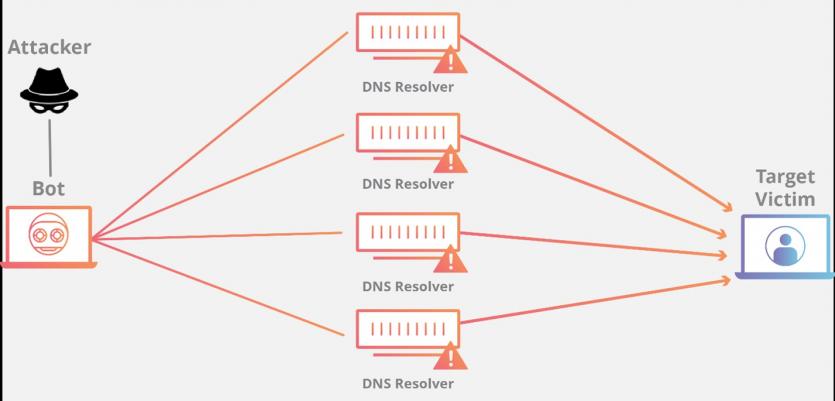
Figure 4
DNS Amplification
The above attack is based on sending a request from the available domain name system server and a fake IP address (the victim’s IP) to disrupt the operation of the target server and network. The above attack achieves a significant result with only minimal effort. The above episode is similar to someone calling a restaurant and saying I want one of all the dishes you have, please get in touch with me to tell each item of my order, and the phone number they give is the target phone number. Isn’t it interesting?
Preventing the implementation of distributed denial of service attacks
The main concern in preventing distributed denial of service attacks is to detect and separate malicious traffic from regular traffic. As we mentioned, the distributed denial of service attack is implemented in different forms (complex, adaptive, simple). It is necessary to explain that the more complex the attack, the more difficult it is to separate the attack traffic from regular traffic. For this reason, unique solutions and methods to prevent distributed denial of service attacks are available to security experts.
The attacker or attackers aim to create complex and unsolvable conditions for the server, network, or site. Hackers always try to use hidden breaches in the server and network to implement this attack model. Network experts can prevent the formation of the above attacks through continuous and detailed investigations. Among the essential solutions to deal with DDoS attacks, the following should be mentioned:
Blackhole Routing
Network administrators mainly use this method. The above process creates a black hole path, and traffic is directed toward this path. To be more precise, the black hole has a function similar to a filter; It pulls in malicious traffic and keeps it away from the network. In the mentioned method, the site’s traffic is sent to the black hole, and it is unavailable after some time. Indeed, the above solution is not ideal, but it protects the network from malicious traffic.
Rate Limiting
The above method limits the number of requests the server accepts at a specific time. It should be explained that the above procedure is mainly used to prevent content theft and is inefficient in dealing with distributed denial of service attacks.
Web Application Firewall
The WAF method is one of the practical solutions to deal with distributed denial of service attacks based on layer 7. You can place a WAF between the Internet and the origin server to act like a firewall. In this case, the web application firewall can deal with different types of malicious traffic.
Anycast Network Diffusion
In the above method, a unicast network is used to disperse the malicious traffic that intends to enter the network. The above solution works almost as if it defines separate channels for directing traffic, which can run malicious traffic to different channels to reduce their severity.
DDoS Mitigation, a powerful solution to deal with DDoS attacks
One of the most effective solutions available to security experts to deal with distributed denial of service attacks is DDoS Mitigation. A method by which a server or network is protected against distributed denial of service attacks. DDoS Mitigation can be done using dedicated network equipment or cloud-based protection services. The DDoS Mitigation architecture deals with this attack model based on a four-step approach, in which a cloud server is deployed in the center of the architecture.
The function of each of the above components is as follows:
Detection
To prevent a distributed denial of service attack, a website must detect the high volume of regular and authorized traffic generated for various reasons. For example, if a web-based service or application releases new traffic, but the site detects it as an attack. A significant portion of the efforts made to increase traffic will be wasted. Therefore, one of the most critical steps of DDoS Mitigation is the ability to detect authorized traffic correctly. Examining IP addresses, paying attention to the pattern of common attacks, and evaluating previous data are among the solutions that should be used in such situations.
Response
The next step is to respond. You can deal with this attack vector by removing malicious traffic and separating it from regular traffic. The network helps to significantly reduce disruption by using WAF rules to counter application layer attacks or filtering processes to manage lower layers (layers 3 and 4), such as cache enhancement.
Routing
At this stage, with intelligent traffic routing, an effective DDoS mitigation strategy solution, the existing traffic is divided into smaller parts so that the service is not interrupted.
adapt
A well-designed network analyzes incoming traffic to find a specific pattern, such as the offending IP, specific attacks from particular countries, or a unique protocol misused. The above analysis helps to compare incoming traffic with attack patterns. The above solution makes it possible to protect the network against current or future threats significantly.
What are the key features of the DDoS Mitigation service?
Traditionally, DDoS Mitigation solutions were based on purchasing equipment placed on-premises by companies and filtering incoming traffic. However, the above approach involved buying and maintaining expensive equipment. Unfortunately, if the distributed denial-of-service attack were too large, the equipment would be unable to protect the infrastructure against the attacks. To be more precise, the equipment could not do anything special for malicious terabyte traffic. Therefore, special features should be considered when renting a DDoS Mitigation service. These features are as follows:
Network capacity
Network capacity is an ideal way to evaluate a DDoS Mitigation service and shows the above service’s ability to contain a DDoS attack. For example, a network with a capacity of one terabit per second can theoretically handle the same amount of traffic minus the bandwidth required to maintain normal operations. Most cloud-based DDoS Mitigation services offer a capacity of several terabits per second capacity, which is beyond organizations’ needs.
Processing capacity
In addition to network capacity, DDoS Mitigation throughput is another important measure you should pay attention to, called processing capabilities. Typically, DDoS Mitigation services are measured in bits per second. Today, attacks above 50 Mbps are expected, with some occurring at 200-300 Mbps. An attack that exceeds the processing power of security mechanisms can easily disrupt the performance of defense systems. For this reason, it is necessary to carefully evaluate this issue before you hire a DDoS Mitigation service.
Delay
Some DDoS Mitigation services can pass or, more precisely, transfer website or application traffic. If the distributed denial-of-service service is in-house, traffic will be redirected to the DDoS Mitigation service when an attack occurs. If DDoS Mitigation is always on, all incoming network traffic will pass through this service, providing the highest security level. An important point to pay attention to is the connection between the data center and the DDoS Mitigation provider. If the link is stable and high-speed, the end users experience the slightest delay.
Additionally, the geographic location of the DDoS Mitigation server and its proximity to the data center you use matter a lot. For example, imagine a company in Asia considering using a DDoS Mitigation service based in Europe. In such a situation, each user request must first be transferred to the European service provider and then returned to Asia twice. Obviously, in such a situation, we see a significant delay.
Mitigation time
When an attack is detected, the time required to repel the attack should be as minimal as possible. Security experts can defeat most distributed denial-of-service attacks in just a few minutes. For this reason, when renting a Mitigation service, you must be careful about its duration. One of the critical questions about DDoS Mitigation is whether the said service can be used to deal with network layer attacks. Therefore, the answer is yes. Because most of the distributed denial of service attacks are carried out on the network layer, are of a volume nature, and cause a lot of damage to the infrastructure, DDoS Mitigation service providers implement the necessary tools to deal with these attack models.
last word
In this article, we tried to examine the distributed denial of the service attack vector and provide solutions to deal with this attack model. In general, it is recommended to check the status of your server traffic every once in a while to prevent sophisticated distributed denial of service attacks around networks and servers. Finally, pay attention to the fact that if you intend to use cloud-based service providers in this field, you must pay special attention to how companies work based on it. For example, some of them use a null routing mechanism to redirect all traffic to a non-existent IP address, or others hide the IP address of the central server so that hackers cannot perform a directly distributed denial of service attack on the server.











