Browse Bitcoin Security Concepts At 4 Levels From Beginner To Professional
To succeed, Bitcoin needs to attract the attention of all its users. But it is very difficult to build an ecosystem that can meet the needs of everyone equally.
However, this goal becomes easier with collaboration. In general, users are divided into 4 levels in terms of the degree of security in Bitcoin.
To meet the needs of each of these levels, we must have a proper definition of them. Each of these levels is based on another level. Paying attention to these levels can help to form an ecosystem model based on the concepts of security, usability and privacy.
The need to teach the security concepts of Bitcoin
Today, bitcoin has a lower entry threshold. In fact, anyone with a little knowledge of the world of cryptocurrencies can now have complete control over their currency without any conditions. This is a crucial moment in today’s society that may face resistance. Decades of using the Fiat currency economy and speculation have kept the less financially literate part of society away from amassing wealth. Thus, power is in the hands of only a few wealthy people.
Unfortunately, teaching basic financial concepts is not part of the school curriculum. This is why a generation of people is emerging who are suffering a lot due to mismanagement of their finances. But instead of continuing this traditional trend, Bitcoin users can unite to promote a more functional and accessible currency.
Training is the key to using Bitcoin. But to educate everyone, it must be used in a simple and understandable way for all people. New users need simple statements to get acquainted with this world. First of all, they need to know the basics of trading and how to back up their wallets. The rest can be taught in later stages.
Learning the basics of bitcoin has become a must
Are Hackers the Only Danger in Bitcoin?
Before examining the different classes and levels of users in digital currencies, we should note that in this area, the theft of digital currencies is not necessarily specific to hackers . Theoretical models of bitcoin or the SHA-256 cryptographic algorithm responsible for securing it are often interesting but irrelevant.
A person who holds bitcoin keys can be the biggest risk for it. That’s why it’s important to know what information you provide when talking to people on the Internet or in everyday life. Operational security is a term used to describe a conscious approach to determining the type of information you share with others. By following this approach, you will become less of a target for hacking.
Basic Security Concepts in Bitcoin
If you have memorized all or part of your retrieval phrase, be careful not to mention it in your conversations. This may be obvious, but the next security step is also important: never even mention having digital currency. They will ask you more questions as soon as others find out. You have questions like how many coins, when did you make the purchase or how did you save it? The answer to each of these can be used as a tool against you.
Caring for bitcoin does not require much energy and time. Taking care of coins in the long run means following the best practices and adhering to them.
There are many ways to improve privacy while taking advantage of advanced applications of digital currencies. The most important step in this is to know the methods of caring for the key or the phrase recovery (SID).
Today, security is based on probability. Retrieval statements generated for bitcoin keys are generally considered secure. Because the probability of reproducing the same expression is as unlikely as the probability of removing only one particular atom from the whole universe.
The only way to lose bitcoin is to sue or cheat , both of which can be prevented with proper training. If users are aware of its security requirements from the moment they enter the world of digital currencies, they will always be comfortable thinking about their assets.
First level security concepts
Here’s how sharing Side (the phrase recovery) can jeopardize your entire investment.
The importance of protecting the phrase recovery
Always have physical copies of your retrieval phrase. Because by digitally copying it, you are actually storing a phrase on a digital machine that did not exist before. This can make it easier to identify and misuse.
When you do not have a key, you will not have a coin. By keeping your digital coins in an exchange wallet, you also run the risk of losing them forever. As long as the keys derived from the phrase recovery are in a wallet, you have no control over your coins. So it is possible to lose them at any moment.
The hardware and software used in Bitcoin are mostly secure. A hardware wallet can store your recovery statement without the need for a network connection and set strict rules for its use. Bitcoin itself is currently impenetrable.
The cost of breaking a private key without knowing a part of it is much higher than the amount of all the money in electronic currencies to date. It is true that one day quantum computers will change this practice.
But by then, we will have decades to come, and during this time, the development of cryptocurrencies that are resistant to quantum methods will make great progress.

Always have physical copies of your retrieval phrase
Irreversibility of transactions
Transactions are irreversible. If you give your coin to someone else, you no longer own it. There is no way to get back the deals. This is why many scammers deceive newcomers by posing as celebrities and offering to double their capital if they keep it.
Second level security concepts
This is enough for many newcomers to the bitcoin world. For others, this could be the starting point for further training and learning about improving privacy, running nodes, or even developing their own personal blockchain. When a certain security framework is provided to someone, the interesting functions and features of Bitcoin can also be used.
If the first level of being a bitcoin holder means observing security issues such as retaining the phrase recovery, the second level is about respecting privacy issues.
The bitcoin address is actually an unknown sequence of characters. The bottom line is that any data you enter at this address can be used as a tool to identify you as a holder of digital coins.
Hidden identity
Anyone using a bitcoin network can see any address and add the desired bitcoin amount to it. In fact, these bitcoins are transferred to the desired address. Here are some tips to help you get started: Therefore, each user should limit the amount of information they share in this regard.
Of course, this does not apply to any type of private information on the Internet. Without knowing the original owner of each address, the chances of successfully using social engineering methods to attack the capital stored at that address will be very low.
Use of lateral methods
Few people are able to buy bitcoins without providing any identity information. So once you pay for the coins, you will be able to track them. This fact is undeniable for certain reasons. But to protect privacy in these situations, special tools such as mixers and network masks can be used.
Mixers like CoinJoin take coins from different sources and combine them in one trade. They are then sent to the output in such a way that they are not traceable to find out their exact source. Network masks (like the Tor project) make it almost impossible to see IP addresses. So no transaction will be traceable to your computer.
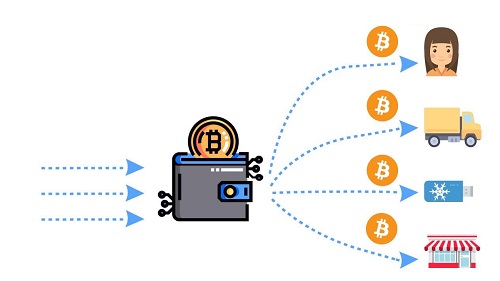
An overview of how bitcoin mixers work
Counting backup
Another feature you should enter at this level is Shamir backup . After learning how to protect the term recovery, or Side, the most important part of becoming known as a Bitcoin user is learning how to use Side while it is divided into different sections. This is known as counting backup. Shamir is a unique standard made by a laboratory called “Satoshi Lip”.
This standard creates a list of words that must be combined to create a wallet. Because the use of this standard increases the complexity, individuals can be assured that losing one or more sids will not result in a loss of their entire capital.
In the past, it was very difficult to move from the first level to the second level. But now the tools introduced in the wallet user interface are included so that you can use them easily.
This way, even users who do not have enough technical knowledge can hide their identities and get support from their own. This advancement owes much to the open source nature of Bitcoin, which allows professionals to develop innovative ways to help secure non-professionals in the Bitcoin world.
Take control of the smallest details in the next levels
So far, we have dealt with the first and second levels of security. At these levels we do not need much technical knowledge to protect our assets. But at levels three and four, we look at the mechanisms that can lead to problems if used improperly. For this reason, we recommend that before using these methods, be sure to do enough research and use advanced tools with awareness.
Third level security concepts
At the third level, the user has already reached a level of awareness and expertise in the areas of privacy and security. But at this level we get to things like lock time, execution and connection to our node, which due to the lack of visual steps may lead to many errors by the user. The most important advantage of this step is to provide a higher level of privacy, which reduces the amount of data shared.
Connecting to the node that is for you will ensure that the transaction data is not leaked. Using locktime, you will achieve similar results. This way you can record the transaction on one device and then broadcast it publicly through different networks.

Locktime is one of the third level security concepts
Level 4 security concepts
At the latest and most advanced bitcoin security level, you may not be able to use some of the features and capabilities. Instead, protect the privacy and security of your property as much as possible. Tools provided for this level include manipulating some sensitive parameters such as return addresses, using multi-signature settings, and complete control over even the smallest details available to the user.
The more we learn about Bitcoin, the more likely we are to build a stronger privacy. The hardware wallet has created an ecosystem that can keep the user safe from day one. With this wallet, you can buy digital currency directly, keep it safe and finally hide any identity information that may lead others to your coins.
With more training, you can reduce the risks in this area and even do the necessary work to ensure the security of your digital capital completely intuitively.
Bitcoin-based service based on user needs
With the help of hardware wallet, novice users who are at the first level of security are completely protected from the risks and malware on the network. So that they can not even easily make simple mistakes like getting caught in a phishing trap . Bitcoin has created a diverse range of users.
In this way, even users who have not yet reached the second and third levels can learn the basic concepts of digital currencies in a safe environment and reach this level if they wish. Manufacturers of not-so-good hardware prefer to have access to your personal information.
But even if you have to access your coins through other tools, you can use methods and tools like CoinJoin to hide the source of your coins and Tor to hide your internet connection point.
Finally, users can take advantage of Bitcoin security benefits such as locktime control, 90 ن routing, by entering the third level. At the fourth level, users have a lot of access even to the available details.
Reaching the fourth level is easier for people like developers with a technical background. However, technical knowledge is not required to use Bitcoin.
This is why even if a person is in the first level of security, he can safely trade and maintain his assets with the help of a hardware wallet.
The importance of open source technology in providing security
Open source technology allows us to focus on solving Bitcoin security problems without worrying about profitability. Satoshi Nakamoto gave Bitcoin to the world for free and now has millions of dollars worth of digital currencies without proving himself. A hardware wallet was created to address issues such as: How to securely store highly sensitive private keys.
The innovation even caught the attention of Bitcoin magazine founder Vitalik Butrin before he created Atrium . Continuous development has led to the re-creation of the product and collaborated with other carbald developers in the Bitcoin community to create an easier ecosystem.

To be part of the bitcoin community, you must follow its security implications
This attachment to the open source world can ensure that anyone entering the cryptographic community has access to a completely secure environment. An environment in which one can learn more about technology and take advantage of benefits that have not been so easily achieved.
For more experienced users, the constant focus on making the tools more powerful and intuitive creates a set of features that allow you to use your money as you wish. Once you have the necessary experience and expertise at all these levels, you may even be able to take a step towards its development.