What Is VMware NSX And What Are Its Features?
Vmware NSX is one of the Virtual Networking Software Family Products that Vmware markets and allows users to implement a powerful network virtualization platform on the server.
The software-driven networks implemented by NSX fall under the Software-Driven Data Center (SDDC) suite, which provides access to cloud computing on VMware virtualization technologies. The purpose of the NSX release is to prepare virtual network environments so that the advantages of physical servers can be used best.
Based on the definition provided, we must say that NSX is a network virtualization infrastructure that can define software-oriented networks and is one of the critical components of software-oriented data center architecture. Network virtualization abstracts network operations from the underlying hardware on a distributed virtualization layer that takes a similar approach to server virtualization.
NSX virtualizes layers 4 through 7 of the Open Systems Interconnection model. In this case, the network fabric virtualizes layer two and layer 3.
NSX virtualizes logical firewalls, switches, routers, ports, and other network elements to users. For this purpose, the hypervisor is installed on the server and manages hardware and network elements.
Essential features and components of VMware NSX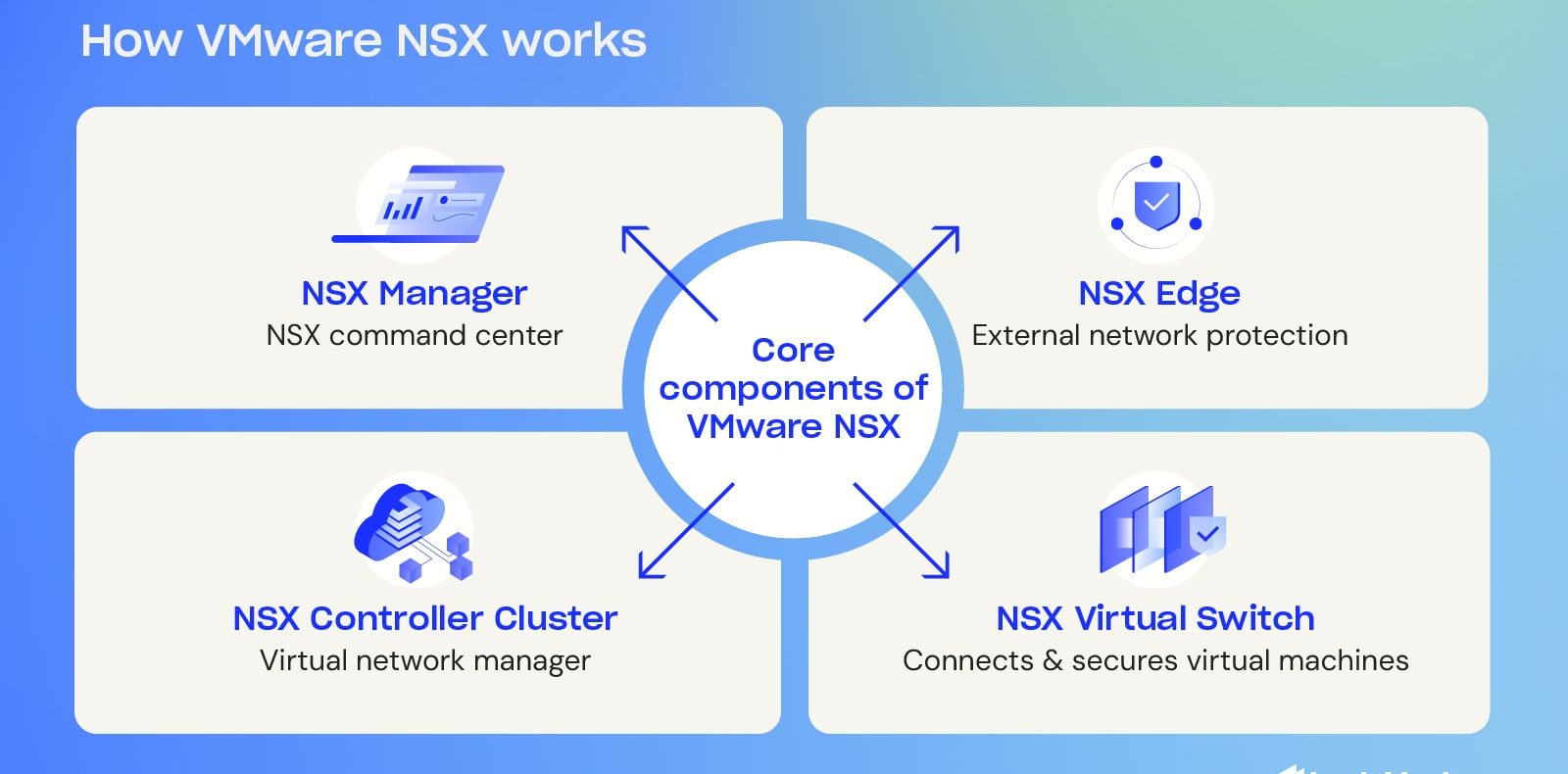
NSX has a wide range of functional features and components, the most important of which are the following:
Switching: NSX virtual switches use unique Virtual Extensible Local Area Network (VXLAN) identities to provide a logically scalable infrastructure for Layer 2 networking. This expanded feature can logically add applications and tenant virtual machines (VMs).
These logical broadcast domains enable greater flexibility and faster deployment while seamlessly extending the parts of a virtual local area network (VLAN). To be more precise, building layer 2 and 3 logical switches can isolate workloads and separate the IP address space between logical networks.
One of the powerful capabilities of NSX is the ability of this technology to create logical broadcast domains in the virtual space; in this case, it is not necessary to make any logical network on physical switches. The above feature is valuable because it does not limit you to 4096 physical broadcast domains (VLANs).
Routing: Performs routing with logically distributed routers that create routes between virtual networks in the hypervisor core. For this purpose, physical routers are used for scalable routing with the ability to overcome failure (failover) in an active and active form. The issue that has made network experts welcome NSX is the technology’s ability to build multiple virtual broadcast domains (logical networks).
When multiple virtual machines are members of these domains, it is essential to be able to route traffic from one logical switch to another. In this case, logical routing is required. Logical routing allows you to better manage traffic routing between logical switches and forward traffic between a logical switch and public networks. Logical routing can be used for east-west routing to eliminate unnecessary hops and improve network performance.
East-to-west traffic is traffic between virtual machines located in a data center. North-south traffic is traffic that enters or exits the data center. More precisely, any traffic entering or leaving the data center is north-south. Here, traffic flows between logical switches in an environment based on a VMware solution.
Logical routers provide access to workloads in physical networks while establishing north-south communication and significantly reduce packet loss rate, ultimately improving network efficiency.
Distributed Firewall: NSX Distributed Firewall is built into the hypervisor core that runs on VMware ESXi. The network administrator can create custom firewall policies at the virtual network interface card level to enable stateful firewall services to run on virtual machines and provide better visibility and control over virtual networks and workloads.
More precisely, the above feature allows network administrators to use a distributed logical firewall or edge firewall within a software-centric network architecture. A distributed logical firewall will enable you to define attribute-based rules based on IP addresses, VLANs, and the names of virtual machines and vCenter objects.
Load balancing: This technology’s load balancer works at layers 4 and 7 to intercept, translate, and modify network traffic to improve the availability and scalability of enterprise applications. The NSX load balancer handles various things, such as the secure sockets layer, to assess the server’s health and pass data packets through it.
After manipulation, a layer four load balancer provides packet-based load balancing that forwards the parcel to a specific server. A layer seven load balancer provides socket-based services that establish client-facing and server-facing connections for a request.
Extensibility: Third-party solutions provided by VMware partners can be directly integrated with the NSX infrastructure to give vendors more choices in delivering multiple services. VMware has many partners that offer solutions such as network traffic monitoring, intrusion detection systems, and security services such as firewalls that can be directly integrated with NSX.
The above approach improves user experience and management, allowing network administrators to perform day-to-day activities through an efficient management system.
Virtual Private Network: NSX includes capabilities to build site-to-site virtual private networks, remote access, and unmanaged virtual private networks for cloud gateway services.
Edge Gateway: The NSX Edge Gateway is a virtual machine that is used as a device to provide Layer 3 routing, firewall, site-to-site virtual private network, load balancing, and other capabilities. This feature supports VXLAN-to-VLAN bridging for seamless connectivity to physical loads.
NSX Edge: Dynamic Host Configuration Protocol is an essential feature with the same functionality as traditional examples and can assign IP addresses. The network administrator can allow the DHCP service to manage all the IP addresses in the environment instead of doing it manually. The DHCP service has an indicator feature that can forward requests to an existing DHCP server.
The NSX Edge DHCP service can forward any DHCP request generated by virtual machines to a current virtual or physical DHCP server without any changes.
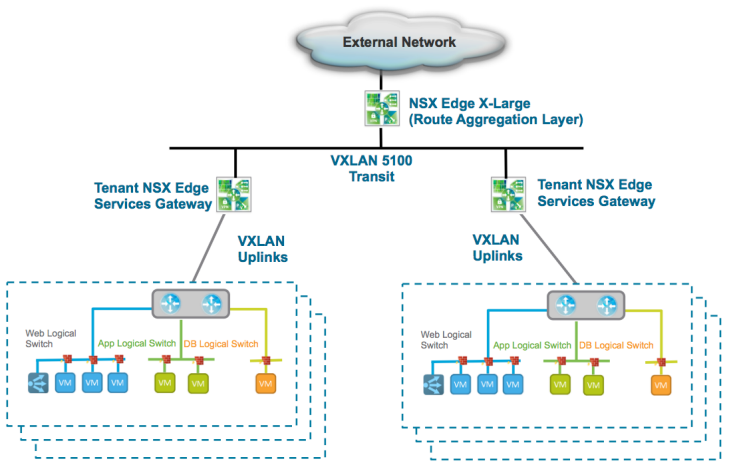
Application programming interface: The NSX programming interface uses an API based on presentational state transitions to simplify third-party product and service integration and NSX integration with cloud management to achieve additional automation capabilities.
Operations: Refers to native operations capabilities, including Central CLI, Switch Port Analyzer, IP Flow Export, Application Rule Manager, Endpoint Monitoring, and integration with VMware vRealize Suite for proactive monitoring, analysis, and troubleshooting.
Dynamic security policy: NSX Service Composer enables the network administrator to provide and assign network and security services to applications. The administrator can also use Service Composer to create emotional security groups with custom filters, such as VMware vCenter objects and tags, operating system type, and Active Directory.
NSX Edge: Domain Name System provides an efficient Domain Name System relay service that can forward any request to an external Domain Name System server.
Cloud management: NSX integrates natively with vRealize Automation and OpenStack for cloud management.
Cross-vCenter Networking and Security: This feature scales NSX vSphere across vCenter and data center boundaries. Network administrators can use this component to address issues such as consolidating capacity across vCenters, streamlining data center migrations, and performing remote vMotions and disaster recovery (DR).
NSX Manager: Once the infrastructure is installed and configured, it can deploy controller clusters and prepare ESXi hosts, which includes the installation of various installation bundles (vSphere) called vSphere Installation Bundles, which have access to network virtualization features such as VXLAN, logical switches, and logical routing.
NSX Manager allows you to deploy and configure essential Edge Gateway and application services. Because NSX Manager is deployed as a single virtual machine, it relies on VMware’s HA capabilities to ensure optimal service availability. An important thing to note about NSX Manager is that if you lose access to NSX Manager, you will no longer have access to the application programming and management interfaces.
However, connecting virtual machines does not face problems. Finally, the NSX Manager configuration user interface allows network administrators to collect reports on bundles and NSX configuration details in a detailed manner.
You get a unique UUID when you install NSX Manager via an OVA template. Also, please note that in a multi-infrastructure vCenter environment, each NSX Manager virtual machine must have its UUID.
Log management: Log management integrates with vRealize Log Insight, which receives log entries from ESXi hosts, uses content packs to process the information each log entry contains, and identifies problems in NSX deployments.
NSX gateway services: Edge gateway services allow network administrators to connect physical and logical networks. A virtual machine connected to a logical network can directly relate to the physical network through a gateway and receive or send traffic.

