What Is Malware And How Can It Be Prevented?
No computer system is safe from malware Attacks, And Familiarity With The Types Of Malware, Mechanisms, And Ways To Deal With them is a requirement these days.
Fans of series like Mr. Robot and Black Mirror are probably well acquainted with the perilous and terrifying face of malware and the depth of power and hacker influence in the lives of uninformed Internet users.
In the series Mr. Robot, a genius hacker who even has the power to infiltrate the AFBI system designs malware to destroy the debt backup files of 70% of the world’s people owned by the vicious and corrupt E-corp company.
Of course, in the rest of the story, we will see how easily hackers can access online account information, bank accounts, IoT-based systems, and mobile phones, and use this information to control people and extort money.

If you decided to cover your laptop camera with glue and paper after watching the Black Mirror series, you are probably not alone in this decision. Hackers are waiting in ambush at any moment to enter your device through the smallest security hole and infect it with all kinds of malware.
The evolution of malware, which reportedly began with the advent of the Brain virus on floppy disks, has introduced a vast array of trojans, worms, vipers, ransomware, and other malware into the tech world that in many cases virtually cripples the lives of individuals and organizations.
The malware that troubled Internet users in the 1990s, such as those that erased data, destroyed the device’s hard drive, or harassed users by displaying ridiculous messages or playing audio, can now be viewed in a safe environment on the Malware Museum website.
Some of this malware may now seem simple, but do not forget that the early malware laid the foundation for more advanced and dangerous versions.
In this article, we will examine the different types of malware and their mechanisms, and at the end, we will introduce the methods of protection against them.
What is malware?
Malware, abbreviated to “malicious software,” is designed by cyber attackers to access or damage a computer or an Internet network. In most cases, the attacker is unaware of malware on their system. When malware enters a computer, hackers can access information, devices, and systems without permission.
The malware was initially designed as a cyber-sabotage to corrupt the computer, change the background image, or access personal information. But over time, it has become a tool for cybercriminals to make money by stealing valuable information to extort money from businesses, hacking passwords to access bank accounts, or stealing identities.
Over the years, malware has come in many forms, and here is a brief history of the first computer virus.
The first computer virus and worm
According to some, the first computer virus was Creeper, which showed up in the early 1970s, ten years before American computer scientist Leonard Adleman called the malware a “computer virus.”
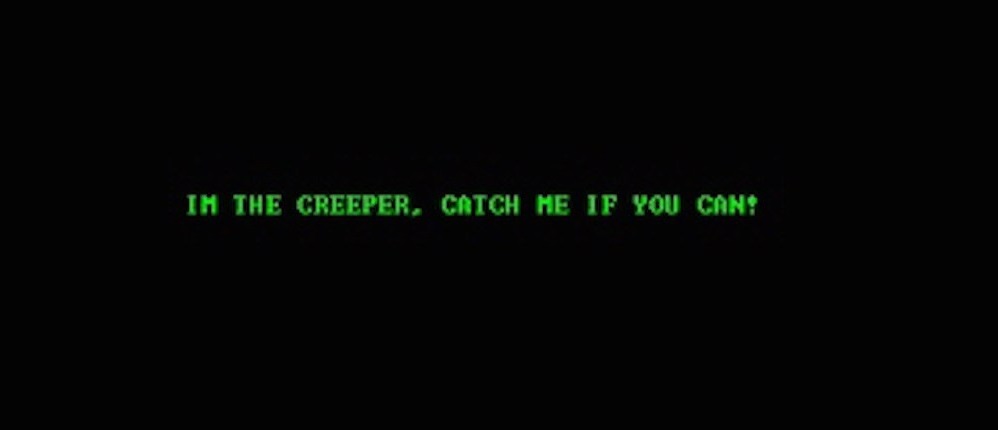
The message displayed by the cripple virus on infected systems: “I cripple: if you can catch me!”
Creeper virus in the operating system Tenex and pre-conversion ( ARPANET ) to the global Internet appeared to transfer from one system to another, and the message appeared: “I Kryprm: if you can get me to throw!” The virus was removed from the previous system when it found a new device to infect; it could not infect multiple devices simultaneously.
Creeper was designed solely for harassment and had no other function, but it was the first software to behave similarly to malware. Shortly afterward, another software program, Reaper, was designed to eliminate disabled people.
On the other hand, some believe that Brain should be named the first computer virus. Unlike Creeper, it could be reproduced without having to delete itself from the previous system.
Much malware today is self-replicating.
But the first computer worm to get media attention was the Morris worm, which in 1988 was able to infect thousands of computers in the very early hours of the Internet, which was then in the hands of academics and engineers, and a large portion of the Internet. The financial estimate of lost productivity due to the Morris worm attack was around $100,000 to $10 million.
Of course, the Morris worm, like the Brain and Creeper viruses, does not exactly qualify as malware. The experiment was out of the developer’s control, and the damage it caused was not intentional.

Source code for Morris cream on a floppy disk at the Museum of Computer History in California
The software tried to estimate the size of the emerging Internet by performing a series of scans. Still, errors in the code led to the unintentional execution of DoS attacks, slowing down some computers to the point where they became virtually unusable.
After the Morris Worm attack, the integrated Internet connection was cut off for several days to prevent it from spreading and clearing the entire network.
Types of malware
| Types of malware | |
|---|---|
| Computer Virus | Worm |
| Trojan | Spyware |
| Ransomware | Wiper |
| Adware | Botnet |
| Cryptocurrency Extraction Malware | Rootkit |
| Fileless Malware | Windows malware |
| Mac malware | Android malware |
| iPhone malware | IoT malware |
Computer Virus

Most Internet and media users use the word “virus” to refer to any malware reported in the news; Fortunately, most malware is not a virus. The computer virus modifies the host’s legally valid files so that the virus can run with it whenever the infected file is executed.
Pure computer viruses are no longer common and comprise only 10% of all available malware. This is a good thing because the virus is the only malware that infects the rest of the files; it is difficult and almost impossible to remove it alone.
Even the best antivirus software cannot separate the virus from other files, and in most cases, it will quarantine or delete the infected files altogether.
Worm

Worms have a more extended history of presence in computer systems than viruses, dating back to the era of big computers. Computer worms emerged with the advent of email in the late 1990s, and for almost ten years, computer security experts were surrounded by malicious worms sent as email attachments.
It was enough for the user to open the email infected with the worm to quickly infect the whole company.
A computer worm’s distinctive feature is its self-replicating ability. For example, the popular Iloveyou worm targets almost all email users worldwide, filling their phone systems with fake messages, shutting down TV networks, and even interrupting newspapers in some places.
Worms such as SQL Slammer and MS Blaster also solidified the worm in the history of computer security.
Worms are more destructive and troublesome than viruses because they can reproduce without user action. Viruses need a user to activate them to run along with the infected program, but the worm uses files and other programs to perform its evil deeds.
The SQL Slammer worm, for example, used a security hole fixed in Microsoft SQL to overflow the buffer of almost all unpatched SQL servers connected to the Internet in 10 minutes; A record that has not been broken to date.
Trojan

One of the most common types of malware is a Trojan, which often disguises itself as a valid and valuable tool to force the user to install. Trojans are older than viruses, but more than any other malware, they have damaged current computers.
The malware’s name is derived from the story of the Trojan horse, in which the ancient Greeks hid inside a giant wooden horse given as a gift to the city of Troy. When the horse entered the city, the Greeks captured it.
Malware has a similar function; In this way, it enters the system secretly and in the form of a helpful tool, such as updating or downloading Flash, and as soon as it enters, it launches the attack.
The user must run the Trojan to access system information.
This malware is often transmitted to the system via email or by visiting infected websites. The most common type of malware ironically manifests as an antivirus program, claiming in a pop-up message that your computer is infected with a virus and that you must install this “software” to remove it. Users are also deceived and by installing malware, they invite the Trojan to their computer like a vampire who needs to be asked to enter the victim’s house.
The most common type of malware in the form of an antivirus program forces the user to download
Depending on its capabilities, the Trojan can access all the information on the system, including account login and password information, screenshots, system information, bank account details, and more.. Once accessed, the Trojan collects this information and sends it to the hacker. Sometimes, malware lets hackers modify the information or shut down a system’s anti-malware program.
Trojans are challenging to deal with for two reasons:
1. Writing a Trojan is easy; millions of copies are made monthly.
2- The Trojan spreads by deceiving the user; Therefore, it can not be prevented with security packages, firewalls, or traditional methods.
Spyware

Spyware’s work comes from its name: spying on other people’s computers and devices. Spyware can access your browser history, the applications you use, or the messages you send. It can be downloaded and installed on a device using trojans or other methods.
For example, the toolbar you download for your browser may contain spyware that monitors your Internet activities. Malicious advertisements may secretly transfer spyware code to your computer through an unwanted download.
The presence of spyware in the alarm system is a warning of more serious threats in the future.
In some cases, spyware is sold to parents as software designed to control a child’s Internet use and is intended to be ignored by security and antivirus software. On the other hand, some companies use spyware to monitor their employees covertly.
Spyware is often easily removed because, unlike other malware, it has no malicious intent. To remove spyware, find the spyware executable file and prevent it from running.
Spyware is not as harmful as other malware, including remote access trojans, but it uses the same login method. As a result, the presence of spyware in the system is an alarm for the user whose system is weak and must be fixed before facing more serious threats.
Ransomware

Most malware prefers to be hidden from the user as much as possible so that they can steal more information out of sight, but ransomware, by its very nature, usually does the opposite.
Ransomware often enters the system through an attachment or a link in phishing emails, infects the system, and extorts money from the user by encrypting or removing it from the system.
To regain access to the system or their locked information, the ransomware requires the user to deposit money into the hacker’s account via Bitcoin or other cryptocurrencies.
This method may seem simple, and you can tell yourself that no one will be fooled. But it is really effective and has often caused serious problems for companies, hospitals, police stations, and even the whole city.
In 2016 alone, cybercriminals pocketed more than $ 1 billion through ransomware attacks.
Europol said ransomware attacks overshadowed many of the world’s cyber threats in 2017.
Most ransomware, like trojans, is spread through some form of social engineering and psychological manipulation of the user. Once executed, it often finds and encrypts user files within the first few minutes; however, some may use the wait-and-see technique and, after a few hours of watching, estimate how much it can extort from the user or, if there is a backup of the files, delete or encrypt them.
A quarter of ransomware victims pay a hacker a ransom, and 30% never have access to their files.
Like any other malware, ransomware attacks can be prevented, but once executed, if there is no good backup of files, the system’s damage will be difficult to repair.
According to studies, about a quarter of the victims pay the ransom to the hacker, and 30% of them can not access their encrypted files even after paying the ransom. Unlocking encrypted files, if possible, requires special tools and much good luck.
The best advice is to back up all your critical files offline to protect yourself from a ransomware attack. Of course, if a genius like Elliott Alderson from the series Mr. Robot wants to organize this attack, there is almost no hope that your backup files will be safe.
Wiper

Viper malware has a simple purpose: to erase all information on the computer or network. Attackers may delete data from the system after it has been extracted and moved to another location, or they may do it solely to destroy all data without any backup.
Examples of Viper malware are those used to attack oil and energy companies, steal information, and then delete it from the system.
Some of these wipers do not just erase the data and encrypt the entire hard drive containing this information, making it unusable.
One of Viper’s most famous attacks was the Petya ransomware, which targeted central banks, international airports, and nuclear power plants worldwide.
At first, it was thought that Patia intended to pay a ransom. Still, investigators found that the victims had no way of gaining access to their information by paying a ransom, and that Petya’s goal from the beginning was to destroy without returning information.
Adware

Most cybercriminals’ ultimate goal is to make money; for some, using advertising software is a good and painless way to do so. Advertising software does exactly what its name implies: It is designed to impose ads on the user.
Sometimes, the only way to get rid of these annoying ads is to click on them, and each click generates revenue for the cybercriminal.
In most cases, the adware has nothing to do with the victim’s information and does not harm the device; it is incredibly annoying and forces the user to click on pop-up windows to close them constantly.
However, if this happens on a mobile phone, it will quickly reduce the battery charge or make it virtually impossible to use the phone by occupying the entire screen.
Botnet
In a robot attack, cybercriminals use malware to secretly take control of a network of Internet-connected devices and launch coordinated attacks by ordering infected and controlled computers (like a bunch of zombies!). On a large scale, such as DDoS attacks, a lot of traffic is directed to the victim’s website or service, causing it to go offline.
Other common attacks involving botnets include large-scale spam, financial data theft, and specific targets on a smaller scale, including the university’s Internet network and offline servers.
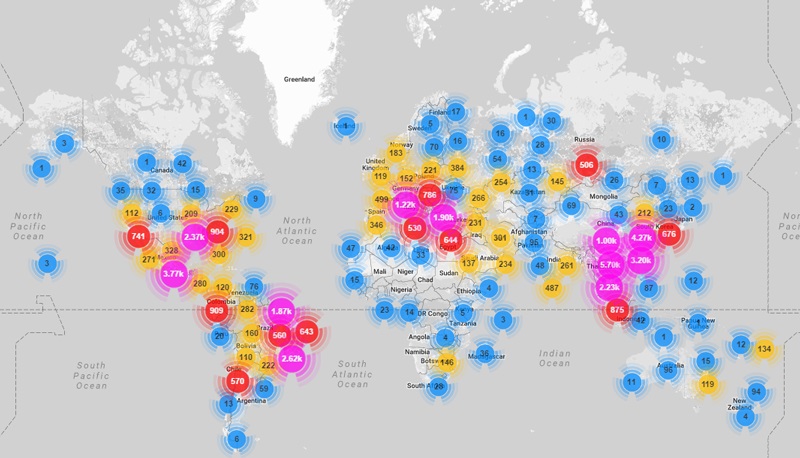
IP of devices infected with the Damping Baton was observed in 164 countries.
Buttons are designed so that the user is entirely unaware of their activity and control of their device. The more devices connected to the Internet, the more botnets attack victims. The popular Mirai botnet, which drastically slowed down Internet services in the United States in late 2016, was partly dependent on IoT-based devices that, due to low security and a lack of tools to remove malware, easily connected to the network controlled by this botnet. Were.
Cryptocurrency Extraction Malware

The remarkable success of Bitcoin has put cryptocurrencies in the public spotlight. In many cases, these cryptocurrencies are not purchased, but users extract them by providing part of the processing power to a part of their computer network or website.
Meanwhile, cybercriminals have also exploited the extraction of cryptocurrencies. Of course, extracting cryptocurrencies is not an illegal activity. However, some cyber-attackers use malware to secretly control other users’ computers and attach them to the botnet to get the most out of them without the computer owner being aware.
One of the largest networks of cybercriminals is the Smominru botnet, which is said to consist of 500,000 systems. Its operators have pocketed at least $3.6 million.
The cryptocurrency extractor usually enters malicious code into the victim device to use the device’s processing power to perform the extraction operations in the background. This process slows down the user’s system until it finally stops, and the user thinks the problem is unreasonable.
PCs and Windows servers are commonly used to extract passwords. However, cybercriminals have recently also become interested in IoT-based devices due to their lack of security and the nature of their connection.
According to the analysis of the Cisco Talos cybersecurity team, an infected system can extract 0.28 units of Ramzarz Monroe daily. Thus, a network of 2,000 infected systems can generate $568 daily and more than $200,000 annually for hackers.
Rootkit

A rootkit is a malware designed to remotely control a computer without the user or security software being aware of its presence. With the help of a rootkit, cybercriminals can execute files, steal information, manipulate system settings and software, or even install other malware. The rootkit can enter the system by installing and running applications, phishing attacks, and security holes.
A rootkit is one of the most dangerous cyber threats because it can hide its presence, turn off system anti-malware programs, and cause severe damage to installed applications. With the help of a rootkit, hackers can spy, launch DDoS attacks, and steal valuable data.
A rootkit is one of the most dangerous cyber threats because it can hide its presence.
To prevent and detect a rootkit attack, do not click on suspicious links that are usually sent to your system via email, use specialized programs to scan your computer, keep your system up to date, and monitor your Internet traffic.
Finding and removing rootkits after they have been installed on the system is very difficult. This is why cybersecurity experts emphasize that prevention is better than a cure in this case than in all other cases.
Fileless Malware

Fileless malware does not fall into a separate category of malware but describes how it works. Older malware infects files on target devices. However, fileless malware accounts for more than 50% of all malware today and does not use the file or file system directly.
Instead, it is played only in the device memory or uses registry keys, application programming interface (APIs), or scheduled ” lifeless tasks.”
This malware model emerged after the success of antivirus programs and anti-malware systems in detecting and resolving cyberattacks and increasing users’ caution and awareness when dealing with strange and unexpected emails and attachments.
Since users are reluctant to open infected emails and links, and most systems use up-to-date antivirus programs, hackers have been forced to design malware to overcome these two barriers and achieve their intended goals.
By attacking and accessing the system infrastructure, attackers create hidden files, folders, or scripts to infect the system, connect networks, and eventually take control of servers.
The nature of fileless malware makes it very difficult to detect and protect the system against it with antivirus software.
However, fixing security holes, keeping the system up to date, and removing or reducing unnecessary admin access can reduce the risk of such malware being attacked to some extent.
Windows malware

Many people once thought that only the Microsoft Windows operating system would be targeted by malware. This was because Windows was once the most common operating system, and hackers designed viruses and malware to fit that operating system.
Windows continues to struggle with malware, and older versions are more vulnerable to cyberattacks than newer ones. However, malware is not limited to the Windows industry, and any device that can connect to the Internet is threatened by malware.
Mac malware
 For years, the Mac operating system was thought to be utterly immune to malware attacks. However, during the 1990s, the malware was designed to target the Windows operating system; it also managed to pollute Mac OS X. Between 1995 and 1998, malware such as Concept and Laroux infected Macs running Microsoft Office applications.
For years, the Mac operating system was thought to be utterly immune to malware attacks. However, during the 1990s, the malware was designed to target the Windows operating system; it also managed to pollute Mac OS X. Between 1995 and 1998, malware such as Concept and Laroux infected Macs running Microsoft Office applications.
Of course, this malware was not malicious. In the case of Concept, only a “1” message was displayed on PC and Mac, and Laroux opened only macro pages of the same name in the user’s Excel project.
In the mid-2000s, hackers began designing malware that targeted the Mac operating system. Although Windows devices continue to bear the brunt of malware attacks, cybercriminals regularly target the Mac OS, including malware downloads and ransomware attacks.
Android malware
Any malware designed to infect computers, including trojans, ransomware, or adware, now has a version for infecting smartphones. The amount of information stored on mobile phones today has made them much more valuable and tempting than computers.
When a smartphone is infected with malware, the hacker can access the positioning, shooting, and eavesdropping capabilities of the phone’s camera and microphone.
Among phones, those based on the Android operating system are more likely to be attacked by malware. The Android open-source ecosystem has made it a tempting target for cybercriminals.
Hackers gain access to a smartphone by encouraging users to download infected applications from stores other than Google Play. In some cases, the malware has taken the form of popular applications such as WhatsApp and has been downloaded more than a million times.
iPhone Malware

The iPhone ecosystem is more secure due to Apple’s stricter policies than Android. iPhone malware is a rare phenomenon, but there have been cases where hackers have found ways to break into these phones and install spyware.
As long as your iOS device is not jailbroken, malware will find it very difficult to infiltrate it. Viruses must interact with system-building programs to spread, but the iPhone operating system greatly limits such interaction.
IOS is designed to run each application in cyberspace separately. As a result, application interaction is limited, and the spread of the virus becomes problematic.
In addition, Apple apps are only downloaded from the App Store, and Apple is conducting a rigorous review of App Store apps. As a result, it is doubtful that malware-infected applications will emerge from the app.
IoT malware
Any device that can connect to the Internet has the potential to be attacked by cybercriminals. The advent of IoT devices has had many benefits for industry, the workplace, and the home, but it has also opened the door to new cybercrime activities.
Some IoT-based devices, from industrial control systems to children’s toys, lack adequate cybersecurity. One of the most common cyberattacks targeting these devices is malware attacks that attach them to a botnet.
Devices such as routers, intelligent lighting systems, video players, and CCTV cameras are easily infected with malware and can be as catastrophic as a Mirai DDoS attack.
The network of Mirai-infected devices was mainly made up of IoT-based products. It was so strong that it could slow down or shut down a large portion of the Internet, making it impossible to access many popular services.
Mirai-infected devices continued to run normally, and there was no problem with the device itself. However, BrickerBot malware crashed the storage space of infected devices and practically disabled them.
Home cameras connected to the Internet, like mobile phones, can become tools for spying on hackers. Some CCTV cameras are so basic in security that malware can easily infect many.
Ways to Protect against Malware

Some basic cybersecurity techniques can help protect your systems and users from malware attacks. For example, ensuring that software and operating systems are up-to-date protects users from many cyber attacks as soon as updates and security packages are released.
The UK Public Health Service was severely damaged by WannaCry ransomware because, weeks after the security packages were released, large parts of the system had not yet been updated.
Updating and installing security packages may be time-consuming, especially for an extensive network of connected systems. Still, this action has been proven to prevent many malware attacks and their sometimes irreversible consequences.
Installing cybersecurity software can help.
Many of these software regularly update the detection mechanism against new malware to be prepared for any potential threat.
Users should also be educated about cybersecurity, secure internet browsing, and the dangers of phishing emails, and be more cautious about clicking and downloading suspicious links. If users raise their cybersecurity awareness, many malware attacks will fail to achieve their goals.


