ICMP: The Network Protocol That Speaks When Things Go Wrong
When information is transmitted over the Internet, computer systems send and receive data using the Transmission Control Protocol/Internet Protocol (TCP/IP) protocol. If there is a connection problem, error, or connection status, messages are sent using ICMP, part of the Internet Protocol.
When a computer connects to another system over the Internet (such as a home computer connecting to a web server to view a website), it may seem like a quick and easy process. While the connection may take a few seconds, there are often many separate connections that must occur for the computers to communicate with each other successfully. If you were to trace the entire process of connecting to the Internet using the traceroute command, you might be surprised that Internet connections are as successful as they are. This is because for each “hop” along the way, the network must be functional and able to accept requests from your computer.
In cases of connection problems, ICMP can send return codes to it. Your system will explain why the connection failed.
These messages may be “Network Unreachable” for a system that is down or “Access Denied” for a secure, password-protected system. ICMP may also provide routing suggestions to help bypass responding systems. While ICMP can send many messages, most of them are never seen by the user. Even if you get an error message, the software you’re using, such as a web browser, has most likely already translated the message into plain (hopefully less technical) language you can understand.
What does ICMP stand for?
Internet Control Message Protocol or “Internet Control Message Protocol.”
What is the application of ICMP?
The main use of ICMP is to send error reports. When two devices are connected to each other through the Internet. If the data of any of these devices does not reach the destination, ICMP sends the desired error report to the source. For example, if the data sent is too large for a router, the router drops the packet and sends an ICMP message about the dropped data to the source.
Another use of ICMP is to diagnose and troubleshoot network problems, which is frequently used in the network support process. Common network tools such as ping and traceroute both use the ICMP protocol. The traceroute tool shows the route of the desired information to the destination and the number of routers on the way, the actual physical route of the connected routers that the request must go through before reaching the destination. This command can determine the reason for the delay of the packet sent to the destination.
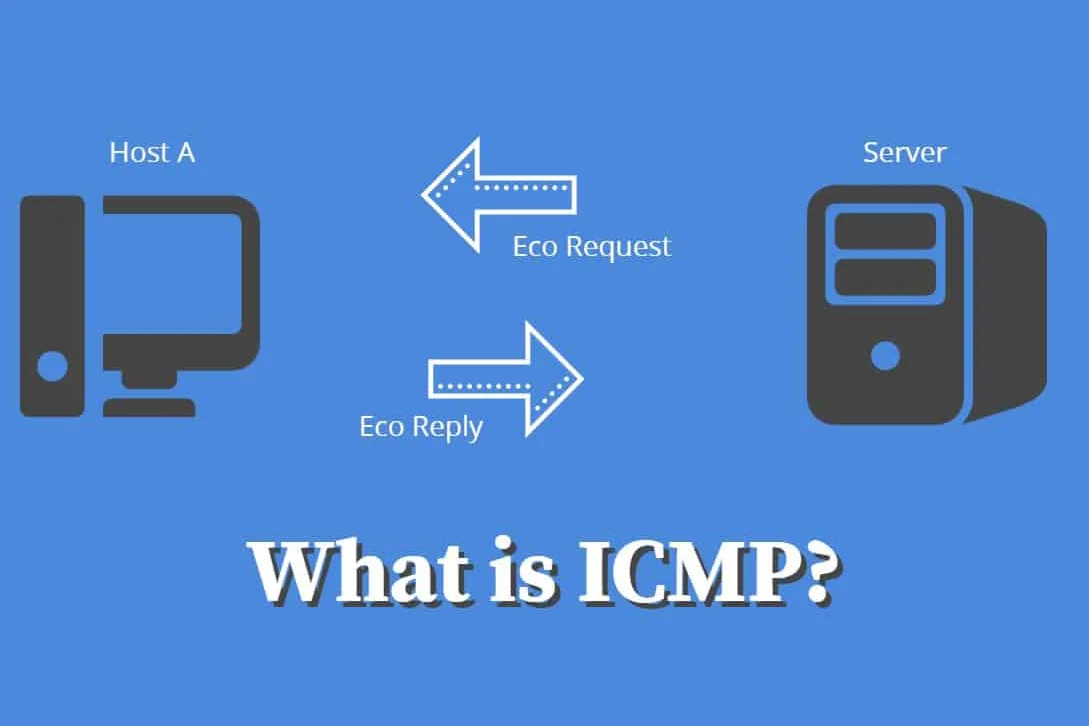
A ping tool is a simplified version of Traceroute. Ping tests the connection speed between two devices and reports how long it takes for the desired information to reach the source and then for the destination to respond to the source. Although Ping provides routing information and doesn’t show the routers between the source and destination, it’s still a very useful metric for measuring latency between two devices. Echo-request and echo-reply are ICMP messages for ping operations.
Unfortunately, network attacks can exploit this process and cause network disruptions, such as ICMP flood attacks and ping death attacks.
How does ICMP work?
Unlike the IP protocol, ICMP is not associated with a transport layer protocol such as TCP or UDP. This makes ICMP a connectionless protocol. In other words, a device does not need to open the sent packet to send a message to the destination. Meanwhile, normal traffic is carried out by the IP protocol using the TCP protocol, so that both devices, before communicating and sending information to each other, must handshake to measure the readiness of both devices to send and receive information. Before sending the main information, they share other information with each other. ICMP also does not target a specific port on a device.
FAQ
What purpose does ICMP serve in networks?
ICMP lets devices send error messages and operational information when IP packets fail to reach their destination.
Which tools use ICMP?
Ping and traceroute use ICMP messages (echo requests and replies, time exceeded) to test connectivity and trace routes.
Can ICMP be exploited or blocked?
Yes — it’s sometimes used in DDoS attacks (e.g. ICMP floods). Many firewalls block or limit ICMP to enhance security.