What Is Credential Stuffing And How Can Information Be Protected Against It?
With The Increasing Digitalization Of Human Life And The Integration Of The Internet With Daily Activities, The Methods And Methods Used By Profiteers To Steal Information And Gain Access To The Privacy Of Others Have Advanced Along With Technology, And This Is Undeniable Issue.
Credential Stuffing, If you follow the news about infiltrating online services and stealing users’ information, and then selling them to earn money or achieve other goals and objectives, you will find that this has become almost commonplace. Sooner or later, User information is stolen from a service or website that has not paid a reasonable price to maintain the security of their subscribers’ information, including the latest available cases can be stolen approximately 500 thousand accounts of Zoom software. He mentioned that they were sold in Darkoob at very low or sometimes free prices.
Although the theft of user information is done in various ways, one of the things that we want to get acquainted with within this article is “Credential Stuffing.”
Although this type of cyber attack has a unique technical title, the hidden solution behind the scenes is straightforward. It can be easily prevented by users being careful and observing tips.
But how?

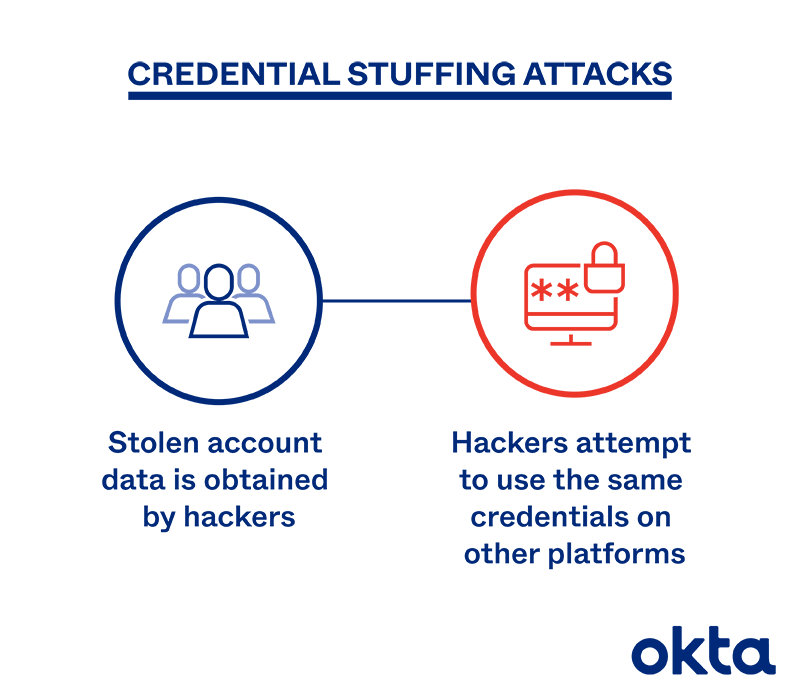
Credential Stuffing Cyber attack is generally the use of information about leaked databases to hack into the accounts of individuals on other services and Internet sites.
Various attacks on online services are common. Profiteers and criminals often identify and exploit security holes in various systems and exploit them to steal databases and databases of personal information, including usernames, passwords, emails, etc., to enter people’s accounts on websites, And various online services are used.
Stolen databases are usually sold anonymously on the Dark Web / Darknet, and buying and selling operations are often performed by cryptocurrencies, or in other words, digital currencies such as Bitcoin, to avoid revealing identity.
In response, it should be said that hacking into people’s user accounts on other websites and online services, regardless of the level of the security system of the services provided, is largely due to the individual’s own negligence!
In the previous paragraph, it was mentioned that stolen databases often contain the information needed to log in to user accounts, including username (username), password, email, etc.
Accordingly, since most people refuse to change their personal information and use the same username and password to register for other online services and websites, it is sufficient for one person to access the disclosed database to It can be used to log in to all your accounts on other websites and steal information.
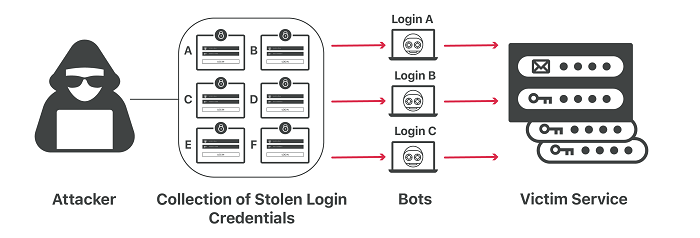
Profiteers and criminals often access databases containing millions of information about individuals’ accounts and then use them to hack into other accounts. You may be wondering how to manually enter the username and password of millions of user accounts in each of the other online services?
In response, it should be said that this operation is not done manually, and writing software or robot to automate this process can be done easily.
One of the reasons that the use of Captcha image codes in login pages and logging in to user accounts of websites is widespread is the disruption of bots to prevent Credential Stuffing cyber-attacks and similar cases, etc. (although Captcha is also a defect related to He himself has suffered and can be circumvented).
When the username and password associated with an account on another website match and the account is logged in, the combination of the relevant username and password is allow listed and then used for other websites and online services.
In this case, if a person has registered using the same username and password on, for example, 10 other websites, hacking, or better to say, logging in, will be done easily.
In this case, the profiteer has not used any unique or complex method to hack into the relevant online service servers or, in other words, hack them; For just a small fee, he bought one of the databases, some of which were leaked several years ago, and committed theft by matching the usernames and passwords on other websites.
Now that we know about Credential Stuffing, how can I protect my accounts against it? Protecting information against the above attack is possible by simply following the small tips that have been repeatedly mentioned.
Do not reuse old passwords.
Using a unique and powerful password for each account individually is very effective in increasing security. In this case, even if the database of a website or online service is leaked on the Internet, the security of your other accounts will not be compromised because the password in the stolen database is different from the password of your other accounts.

Use password management programs.
Remembering a strong password consisting of letters, numbers, and punctuation is a daunting task, and it is almost impossible to do so for multiple accounts. Using password management software easily can be very effective in this regard and relieve you of the burden of remembering passwords and writing them down.
In addition, some software in this field has the ability to generate a password.
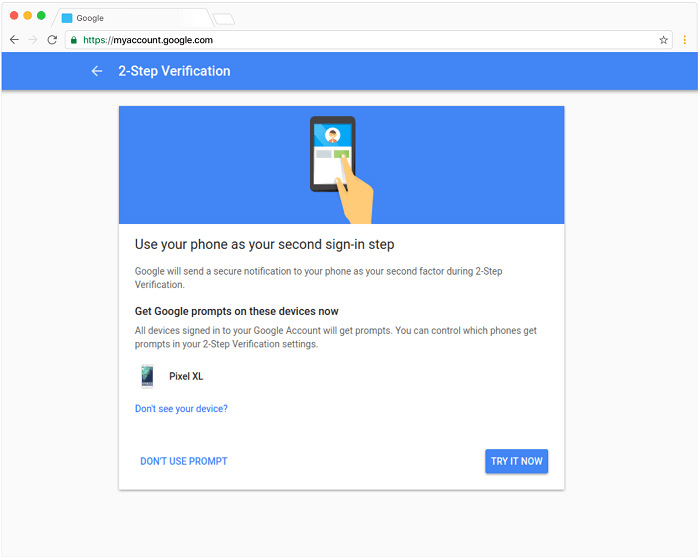
Activation of a two-step authentication system
By activating two-step authentication (Two-Step Authentication or Two-Step Verification), when someone tries to log in to your account, a secondary password is generated by the server and website and sent via SMS to your mobile number and login. The user account is subject to entering it on the login page.
In this case, even if the profiteer has your username and password, his lack of access to the sent code will prevent him from accessing your account.
There is no need for the server to generate and send code automatically. Depending on the system implemented by the website or online server, the user may be left to choose a password in the form of a second password (such as the Telegram social network).
Awareness of leaked databases
With services such as? Have I Been Pwned? You can find out about databases leaked in recent years. If you register, if your account information is identified among them, a notification message will be sent to you by the service…