What is Cisco FabricPath and how does it help network experts?
With The Ever-Increasing Expansion Of Cloud Services And The Need For Mobility, the Spanning Tree Protocol (STP) Cannot Meet The Needs Of Today’s Data Centers.
To solve this problem, network experts developed a transparent interconnection standard based on lots of TRILL links called Transparent Interconnection of Lots of Links, which has a lot of convergence with Cisco’s innovative technology, FabricPath, and can improve the performance of computer networks. Still, Cisco FabricPath has appeared more successful in this regard.
What is Cisco FabricPath?
- Cisco FabricPath is Cisco’s innovative technology to overcome the limitations of the spanning tree protocol, providing significant capabilities for scalability, convergence, and congestion-related problems in the network.
- Cisco FabricPath is based on the IS-IS pattern. It is implemented in the control plane, which is why it is called layer two routings.
As you might have guessed, FabricPath is a solution to overcome the Spanning Tree Protocol problems and is considered an alternative. An important point to note in this context is that Spanning Tree Protocol at layer 2 prevents the formation of loops, while the Cisco routing protocols at layer 3 seek to eliminate loops in the network.
Typically, routing protocols are smart enough to handle traffic loading correctly, that is, not to overload a communication channel, but Spanning Tree Protocol is not intelligent enough in this regard. It cannot actively-actively Manage the process of transferring information packets. For this reason, to implement the active-active pattern and build a loop-free topology in layers 2 and 3, Cisco FabricPath technology was invented.
FabricPath is Cisco’s exclusive technology and has similar functionality to TRILL, an IETF standard. The significant advantage that FabricPath has is that it offers the highest level of flexibility without the loop problem. A feature that the spanning tree protocol is unable to provide. The same issue led data centers to use Cisco FabricPath technology instead of Spanning Tree Protocol.
The critical point is that the Intermediate System protocol or IS-IS layer 2 differs from the IS-IS layer three protocol. The layer two intermediate system protocol provides a specific view of the unified topology in the network that is based on FabricPath. Also, it is responsible for balancing traffic load using ECMP. The layer two intermediate system protocol does not require configuration, and you only need to enable FabricPath to run the above protocol in the background automatically.
How does FabricPath work?
As mentioned, Cisco’s FabricPath technology has performed very well in high-scale traffic routing and data center networks. This technology combines the functions of layer two and layer three so that networked devices can route intelligently without worrying about the formation of loops. It plays a vital role in sharing and properly dividing the traffic load.
On the other hand, Spanning Tree Protocol works only as Plug & Play and lacks layer three intelligence. FabricPathIt is equipped with a layer three routing protocol and intelligent algorithms that work behind the scenes so that the above technology can provide an active-active architecture while preventing loop formation. The above pattern is also known as IS-IS layer two architecture and is independent of IS-IS layer 3.
An important point to note in this context is that FabricPath, similar to Spanning Tree Protocol, incorporates Ethernet as the underlying protocol. This issue has made ECMP offer simplicity, flexibility, and good expandability and several paths with equal cost called Equal Cost Multi-pathing. It should be explained that FabricPath technology is also known as MAC-in-MAC routing, forwarding, encapsulation, and tunneling protocol because it can frame
Route encapsulated MAC-in-MAC for the destination FabricPath switch. When using FabricPath technology, be careful that each device in a FabricPath domain has a switch ID assigned manually or dynamically through the Dynamic Resource Allocation Protocol (DRAP). A 12-bit identifier is often used in the Fabricpath header.
What benefits does FabricPath offer?
While FabricPath offers the highest level of reliability, it also has other significant benefits, the most important of which are the following:
It significantly simplifies the network configuration process. In this case, network experts should only consider configuring the necessary things, such as distinguishing the central switches’ ports responsible for connecting the buttons, the edge ports that the end devices link to, and so on. Here, you don’t need to think about setting a parameter to achieve the optimal configuration because the addresses of the switches are assigned automatically. In this case, the operational costs of establishing networks will be significantly reduced.
It provides a single control protocol for sending unicast, multicast, and pruning messages over a virtual local area network. This protocol requires less hybrid configuration than a network based on spanning tree protocol. Hence, it is easier to manage.
Static network designs make assumptions about traffic patterns and the location of servers and services that, if these assumptions turn out to be wrong, which is the case in most cases, force network experts to rethink the network. FabricPath’s fabric replacement mechanism allows network experts to make changes based on a non-disruptive endpoint solution.
Switches unable to support FabricPath technology can be redundantly connected to FabricPath without using the Spanning Tree Protocol.
FabricPath’s troubleshooting capabilities are a step up from IP-based tools. Tools such as ping and traceroute, which work at layer 2, delay performing calculations as they test a particular route among several equal-cost routes to reach a destination.
FabricPath indeed provides an out-of-the-box user interface. However, its control protocol is implemented based on the IS-IS intermediate routing protocol, which offers high convergence and speed. For this reason, it is a protocol that can be used in large-scale environments.
Cisco FabricPath frames have a timing field (TTL) similar to the IP protocols. They prevent and reduce loops in the data plane, ensuring that packets reach their destination correctly. In addition, reverse route forwarding (RPF) checking is also applied to them. Hardware that uses FabricPath technology supports can implement 16-way equal-cost multipathing (ECMP), which, when combined with 16 10-Gigabit ports, provides multi-Tigabit switching capacity between switches. Due to the use of ECMP in the data plane, the network can optimally use all available links between both devices. Additionally, frames are sent to the destination via the shortest available path. The mentioned feature significantly reduces the time exchanging information packets between endpoints compared to the spanning tree protocol.
Given that FabricPath only needs to obtain the information it needs about a subset of MAC addresses at the edge of the fabric, it allows for massive scalability of the switched domain.
FabricPath headers
The FabricPath header contains the following fields:
- OMAC: external MAC address.
- OSA: external source address.
- ODA: foreign destination address.
- Switch ID (Source ID): Used for source and destination switches.
- Ether Type: It has a function similar to classic Ethernet.
- TTL: It has the same position as traditional Ethernet.
- FTag (Forwarding Tag): Used to transfer traffic in the FabricPath domain.
ODA is used for known unicast messages, while FTag is used for unknown unicast, multicast, and broadcast packets. As you may have guessed from the above header, the outer MAC address of the FabricPath header and the inner MAC address of the title is classic Ethernet. This issue has made the MAC-in-MAC routing process more accurate.
The exact opposite of the above architecture is the spanning tree protocol, which is a control plane protocol with no headers. In contrast, FabricPath works on the control and data planes and has the same header as Ethernet. Figure 1 shows the FabricPath title.
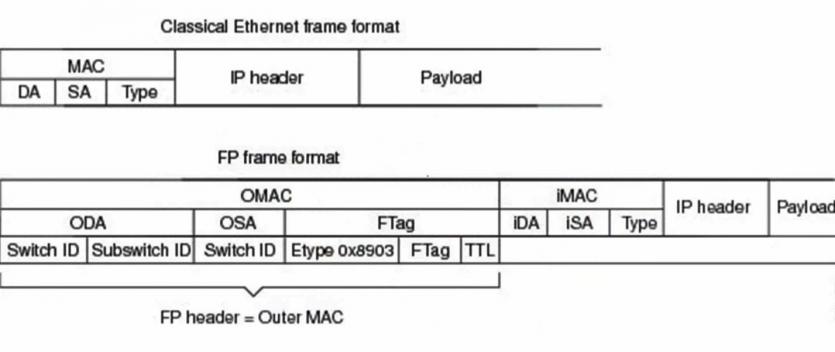
figure 1
FabricPath operations
FabricPath is generally used for layer two multipath networking and is naturally equipped with loop-prevention mechanisms. As a result, it removes the dependency on the spanning tree protocol. For a FabricPath-based network, the FabricPath header is attached to the input interface and removed from the scope of the output interface.
The Core/Aggregation/Access network topology in modern data centers is implemented as a leaf spine. Some leaf switches form the access layer, which is fully connected to the spine switches. FabricPathIt is mainly implemented on centralized and centralized switches. To be more precise, network experts do not implement it on access switches. This issue allows classic Ethernet switches in the access layer to work seamlessly with the FabricPath domain in the distribution and aggregation layers. It is necessary to explain that the FabricPath switch can be an edge or a central switch. A switch can have one port as an edge port and another as a hub port to connect to classic Ethernet and FabricPath networks. In this case, we call the above switch an edge switch. A switch with all main FabricPath ports is called a core switch.
For the terms leaf and spine, a leaf switch is an edge switch, while a spine switch is a central switch.FabricPath is as follows:
- Known Unicast
- Unknown Unicast
- Multicast
- Broadcast
For known unicast traffic, the ODA field is used. Still, for unknown unicast, multicast, and broadcast, the process of transferring information packets and traffic in FabricPath is based on the FTag field, which is responsible for directing and managing multi-destination traffic. This is done by two FTag trees supported by IS-IS in a FabricPath network are made and are called multipurpose trees.
The two multi-destination ring-free trees constructed through the intermediate system protocol are FTag1 and FTag2. In this case, one tree is used for unicast, multicast, and unknown broadcast traffic, while the second is for multicast traffic only.
Multicast traffic can be Multicast Plane Control or Data Plane traffic, which is why both FTag trees receive it. In this case, FTag 1 is used for multicast page control traffic, and FTag 2 is used for multicast data page traffic.
FTag trees have logical topologies that IS-IS automatically constructs. Figure 2 shows this. In this case, each tree has its root node, which is selected based on root priority, where the node with the highest priority is chosen as the root switch of the FTag tree.
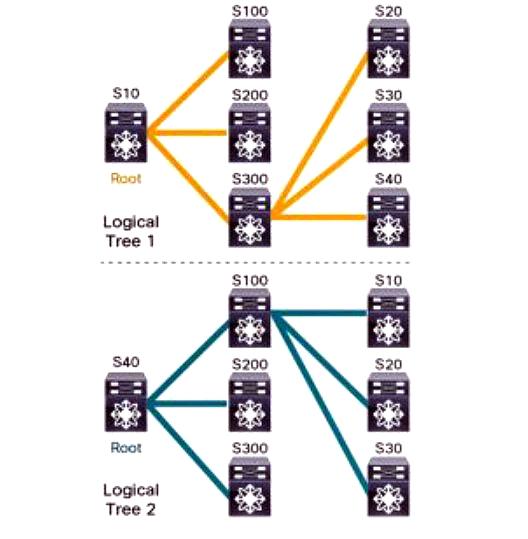
figure 2
In short, known unicast traffic is sent based on the destination switch ID using ECMP, and no FTag tree is used. However, in the case of sending unicast, multicast, and broadcast messages, this process is performed after the FTag trees are evaluated. It is necessary to explain that the texture path in Cisco Nexus switches is supported only in F-series modules and not in M-Series (L3) modules.
FabricPath Virtual LANs
Switches have classic Ethernet virtual LANs by default. In the case of FabricPath, you need to configure FabricPath VLANs and change the port mode to FabricPath. One thing to note in this context is that only FabricPath virtual LANs can use FabricPath ports. FabricPath mode in virtual LANs is only locally relevant to the VDC named Virtual Device Context.
FabricPath is based on a virtual LAN, and only virtual LANs enabled for FabricPath mode can use the FabricPath infrastructure. Hence, you can define specific virtual LANs as FabricPathDefine VLAN and the rest as classic Ethernet virtual LANs. Each VDC has a switch ID in the FabricPath.
Conversational MAC Learning
Traffic switching in FabricPath is based on the Conversational MAC Learning component. Before we examine the functionality of Conversational MAC Learning, an important point to note is that traditional MAC Learning is resource-based learning. Switches build their CAM tables by learning source MAC addresses to redirect traffic.
In contrast, Conversational MAC Learning works by learning only the MAC addresses of hosts. The advantage of the above method is that a FabricPath switch needs to know fewer MAC addresses, and the size of the CAM table is significantly reduced. Hence it requires less memory, and the scalability process is done more efficiently.
Classic Ethernet works based on the default traditional learning method, but it is possible to configure Conversational Learning for any virtual LAN. Conversational Learning architecture is based on a “Three-Way Handshake” because learning MAC addresses is done after the completion of three-way communication.
In addition, you should know that central switches in a FabricPath domain perform packet-forwarding operations based on switch IDs. To be more precise, they don’t need to learn MAC addresses. Hence, the FabricPath core does not have a MAC address, just like the BGP-less cores in MPLS.
last word
FabricPath is an efficient Cisco technology that provides ease of deployment, high reliability, and scalability for Layer 3 routing. Using this technology, you can build scalable layer two multipath networks without depending on spanning tree protocol. FabricPath is suitable for virtualization-based networks, private clouds, and high-performance computing environments.

