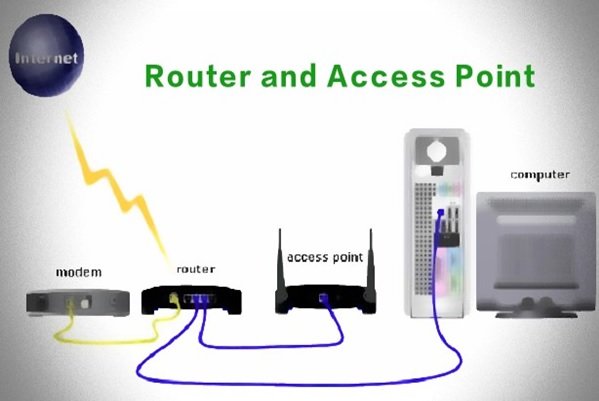
How to Increase the Security of Router Firmware
A firmware update for the router is just as important as updating the firmware on other devices. Performing Middleware Updates Will Give You New Features, Security Enhancements / and Fixes. If your router is a…