A Guide To Iot Security And Smart Equipment
In the new age of personal computers, smartphones, thermostats, smart meters, automakers, and even digital voice assistants like Google Ok can connect to the Internet and interact with consumers, but the shadow of security threats looms over these smart devices…
Security breaches in any of the smart devices may pave the way for hackers to access infrastructure and communications networks. The Internet of Things has promised to improve living conditions, but to fulfill this promise, security vulnerabilities around IoT equipment need to be properly identified and addressed.
IT experts define every object connected to the network as an IoT gadget and believe that an IoT gadget is still an IoT gadget, even if it is not connected to the Internet and only interacts with the local network.
Smart TVs, cars, wireless routers, smart cameras, smart locks connected to the network via Bluetooth or Arafid labels, medical equipment, smart voice assistants, smart lights, fitness equipment, and the like are all classified in the IoT equipment group.
By definition, any home or business device that has the ability to connect to the Internet is an IoT tool.
Consumers and manufacturers have welcomed smart equipment.
Consumers tend to buy smart tools because of their many and varied capabilities.
Manufacturers are also pleased with the production of these gadgets, as it allows them to gather information about customers’ consumption patterns and use this information to build more accurate equipment.
Information that is normally difficult to access is now readily available and helps companies advance their business strategies.
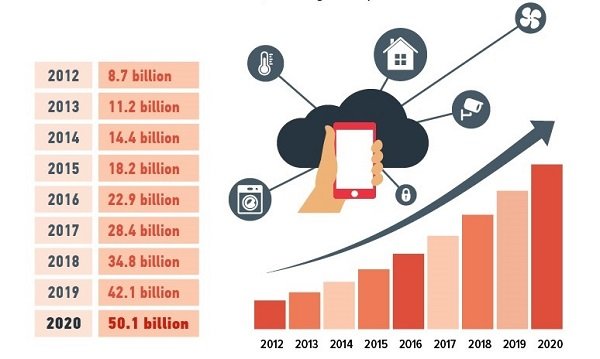
Statistics show that the number of IoT gadgets is increasing every year and it is expected that this year (2020) this number will reach 50 billion smart devices (Figure 1).
Why is IoT security important?
In 2016, the Mirai botnet launched one of the largest distributed denials of service (DDoS) attacks. The attack, which was more than 1 terabyte per second, affected the Dine Infrastructure Network, the core provider of Domain Name System (DNS) services, and sites such as Reddit and Airbnb.
The factor that made this attack special and to the attention of security experts was the use of IoT tools. In this attack, nearly 150,000 smart cameras, routers, and various devices that were part of a botnet network, all of which were connected to the Internet, simultaneously attacked a centralized target.
Figure 2 shows the Batten Mirai thermal map (the US only), which records the severity of the attack and shows how the distribution denial attack made access to important sites impossible for several hours.
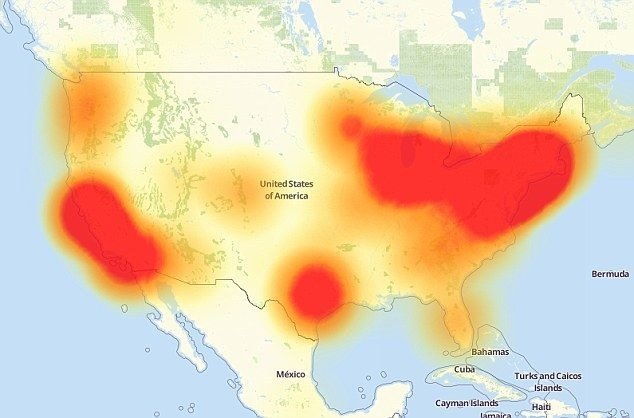
At a time when IoT equipment was not yet ubiquitous, the Mirai botnet managed to launch a 1TB attack.
More specifically, only 22.9 billion Internet-connected devices were active in 2016, while by 2020 more than 50 billion devices are expected to be connected to local area networks and the Internet.
If hackers detect only a small breach in IoT equipment, they will have the ability to launch attacks of at least 2 terabits per second against large organizations and critical infrastructure.
The Mirai Button at the time consisted of millions of IoT devices, all connected to the Internet. The factor that makes network-connected equipment easily fall victim to is the use of identical passwords and usernames by manufacturers.
In other words, when manufacturers of routers, WiFi developers, access points, smart cameras, and similar devices are marketed with the same password, the majority of users use the same username and password to interact with the device.
As a result, hackers can detect a breach in a manufacturer’s equipment with little effort and then gain access to hundreds of thousands of devices.
Hackers only need a few minutes to hack a networked device that works based on default information.
IoT bones are not the only threat to cyberspace. Security experts have repeatedly shown that any software-based device that contains firmware may be vulnerable to hackers.
Cars are one of the biggest concerns of security experts, who have identified and exploited various types of vulnerabilities hidden in their engines, controls, lights, and accelerator pedals in the laboratory.
Now, if such a vulnerability is exploited in the real world, full control of the machine is given to the hacker.
IoT vulnerabilities
Simplicity and ease of use play an important role in the information technology, e-commerce, and e-commerce industries. In the real world, software and devices are designed so that users can use them without much complexity.
Ease of use means increasing the number of users who use software or device. Unfortunately, this perspective often causes us to become overwhelmed when it comes to security.
Default insecure input information
In some products, manufacturers place password and username change options deep in the UI settings that are not easy for consumers to find. This is why most users use the device’s default password and username. If IoT devices have a random username and password, the likelihood of a Mirai-like attack is minimized.
Since manufacturers are in fierce competition with each other to gain more profit and market share, they use the simplest security mechanisms to authenticate consumers.
Poor software updates
Most IoT equipment manufacturers do not release security updates or patches for their product software. Today, the equipment used by consumers is contaminated with software vulnerabilities that can only be patched with the help of product manufacturers and updates. When a manufacturer does not support its product, users have little chance of securing their devices.
Communications that are not encrypted
Some IoT devices communicate with the central server and exchange information without the use of cryptographic algorithms. As a result, the chances of successfully implementing a middle-aged attack increase. Unfortunately, for some IoT equipment, the product is designed to require too much permission from the user.
In a thought-provoking example, several Amazon Echo users, after viewing a TV interlude on their TV screen, saw the phrase Alexa ordered me a dollhouse and found that Alexa had requested it without their knowledge.
Has given a dollhouse. In this example, Amazon Echo could order products based on the license is received from the user. Any additional authorization that an IoT tool receives means a double vulnerability that hackers may exploit.
Insecure user interface
The user interface of the equipment is the first component that hackers turn to because front-end developers sometimes make mistakes when coding due to little experience.
For example, a hacker may manipulate the “I forgot my password” option to reset my password or find my username or email. A device that has a correct user interface does not allow the user to repeat the wrong data entry process after several unsuccessful attempts.
In most cases, hackers try to find the passwords and usernames of devices based on dictionary attacks or pervasive searches.
In some cases, the password is sent in the form of a simple text from the consumer device to the central server and there is no news of cryptographic algorithms. As a result, any user with little technical knowledge can extract this information.
Protect privacy as weakly as possible
Devices connected to the Internet are constantly sending and receiving data, but IoT sensors send and receive information more than other well-known devices under the network.
The less information the equipment has about the user, the less information it provides to hackers when it is hacked. It is best to look at the type of data the device stores about you and monitor the process of sending and receiving information.
For example, in some cases, devices such as smart lights or coffee makers request the user’s location information, in which case you should contact the device manufacturer or the relevant authorities to see why such devices need your location information.
The most common attacks on IoT equipment
Smart devices are exposed to a variety of vulnerabilities and attacks. The most common of these attacks are:
Exploitation of vulnerabilities
Each software has its own vulnerability. It is impossible to patch some vulnerabilities because most of them are backdoors that developers have put in place to make changes to software, but have been discovered by hackers. However, in some cases, the vulnerabilities are a clear indication of poor coding, which causes the following problems.
Buffer overflow: This problem occurs when software tries to place too much data in a temporary storage (buffer) space. In this case, the extra data is stored in another part of the memory and transcribed.
If a hacker can find this vulnerability, he will create malware that will hide inside this part of the memory and rewrite its code into the software.
Code Injection:
Another vulnerability that allows hackers to exploit IoT equipment is code injection attacks. The code injection technique allows hackers to manage some of the key and important tasks of the device, such as shutting down or controlling the device.
Script injection through the site: In this method, hackers infect the site associated with the device with malicious code so that whenever the device is connected to the site and receives an update, malicious code is installed inside the device.
Figure 3 shows how to collect information from the user and send it to the hacker server.

Attack using malware
The most common attacks on IoT equipment are login pages and fields. However, other malware has entered the world of IoT equipment, of which ransomware is an example.
Linux-based operating systems pose a serious threat because hackers can target the devices with a series of minor modifications. Smart TVs are one of the most common devices that may fall victim to hackers.
For example, smart TV users who try to illegally watch movies and TV series over the Internet are exposed to a variety of attacks, such as locking the TV due to ransomware infection. Figure 4 shows the most common malware used to infect IoT equipment.

Password attacks
Password attacks, such as dictionary or search queries, directly target login information and are repeated until the username and password are found. Statistics show that most people use relatively simple passwords, which increases the chances of hackers breaking them, and unfortunately, 60% of them use the same password for different devices.
As a result, if a hacker manages to crack the password of one account, he will gain access to other accounts. Figure 5 shows password attacks around IoT equipment.

Eavesdropping attacks mediated by human intervention
In this mechanism, the hacker attack tries to put himself in the middle of the internet traffic coming out of a smart device, stop it or eavesdrop on it.
In most cases, the main purpose of the router is Wi-Fi, because the router exchanges all the traffic data of a network, and hacking it is like controlling the devices connected to the network. Figure 6 shows the eavesdropping around IoT equipment.

Spoofing attacks
Appearance attacks, or more commonly cyber-forgeries, are carried out in such a way that device A is hidden in a way that looks like device B. In the above scenario, if device B has access to the wireless network, device A commands it (device B) to connect the router to the network.
In this case, device A can communicate with the router and inject malware into the network. The malware then enters other equipment under the network and spreads the infection.
Figure 7 shows the different types of ICT attacks around IoT equipment.

Join Button Network
IoT tools are the first victims of botanical attacks because they are easily hacked and difficult to detect. Whenever IoT equipment becomes infected with hackers, hackers can use it to carry out various types of cyberattacks, including sending spam, making fake clicks, implementing distributed denial of service attacks, and extracting bitcoins.
Figure 8 shows the pattern of IoT equipment contamination intending to join the botnet network.

Access and remote control
At first glance, remote control of an IoT gadget is not a bad idea and maybe useful, but when a hacker can poison a user by hacking a coffee maker, then remote control becomes a serious problem.
On a larger scale, controlling a car is a very serious threat and unfortunately not a hypothetical scenario, because in the real world hackers have managed to hack into various parts of a car such as a car’s braking and acceleration system, and take control of it.
Today, in some companies and homes, people use smart locks, however, all locks use software to control the hardware.
At last year’s DefCon conference, researchers tested 16 smart locks and found that many of them use plain text passwords. Other smart locks were also vulnerable to counterfeiting and relay attacks.

Leakage of information about IoT equipment
Smart devices are constantly processing users’ personal information such as medical information, location, patterns used, search records, financial information, and the like. This allows hackers to steal various information through IoT devices.
Researchers at the Dafkan Security Conference showed that a smart audio speaker could be hacked, data received from its sensors, and analyzed to find out if people were at home.
An approach that allows hackers to safely move into vacant homes. Hackers can steal various personal information by infiltrating IoT equipment and continuing to use technical techniques. Figure 10 shows the information that attackers can gain by infiltrating IoT equipment.

Why hasn’t an effective security solution been developed so far to filter traffic?
One effective way to limit the damage done by IoT equipment is to filter out suspicious traffic. Theoretically, Internet service providers can detect and filter malicious traffic on their networks.
However, the error rate and the probability of false-positive feedback are high. Another way is to filter traffic at the user level. Tools such as the Luma Wi-Fi System and the Bitdefender Box are capable of blocking malicious traffic to a large extent by providing intelligent hardware filters, but they are not affordable for home users due to their high cost.
Solutions to improve the security of IoT equipment
There are several ways to secure IoT equipment, the most important of which are:
Change the device’s default password and username: We recommend that you use a password of at least 10 characters, including uppercase, lowercase, numbers, and special characters. It is better than the passwords of different devices are different from each other.
Install software updates: Reputable IoT manufacturers release updates. Updates are often published to patch security vulnerabilities. As a general rule, look at the product update cycle before buying a product. Figure 11 shows the standard update release cycle.

Enable login lock settings:
Specific passwords and usernames are also vulnerable to pervasive search and dictionary attacks.
These attacks continuously enter various information into the input fields to eventually crack the passwords.
In some products, after 10 unsuccessful attempts, the device lock is activated and prevents unauthorized continuous attempts.
Two-step authentication: In this area, IoT devices lag behind other devices, but efforts have been made. For example, Nest has announced a two-step authentication mechanism for its two thermostats and smart camera products.
Physical weaknesses are hidden in IoT equipment
Sometimes infecting a personal computer requires only a flash drive, and as soon as it connects to the system, Windows automatically runs and opens it to infect the malware hidden in the flash drive. The same approach applies to IoT equipment.
If the IoT equipment is equipped with a USB port, all a hacker has to do is connect a memory containing malware to the device to infect the device middleware.
Cryptography
Most IoT devices connect to a central server, the Internet, a local network, or a smartphone to perform their activities. Unfortunately, in most cases, the information exchanged between these media and IoT equipment is not properly encrypted, as manufacturers try to ignore some security features to simplify and in some cases reduce costs.
For this reason, we suggest that if there is an encryption option on the device, be sure to enable it so that information can be exchanged securely.
Implement a separate network for IoT equipment
A safe way to use IoT equipment with other important devices is to implement a separate network. If the gadget does not need to connect to the Internet, use a separate local network.
If it needs Internet access, use a second network so that if hackers succeed in hacking it, they can not easily access other devices within the network.
The problem with this method is that if IoT devices are to be controlled with a smartphone, you have to switch between Wi-Fi networks. There is a solution to this problem, automating tasks or using ZWave switches are acceptable solutions.
Secure WiFi
Use a good firewall to protect WiFi. While firewalls are available to users in software form, some routers come with such a feature by default that they must be enabled.
Guest networks are used with the idea that they restrict access to the main network, but some routers insecurely create a guest network and allow hackers to use the guest network to infiltrate the main network.

