Security Solutions To Monitor The Performance Of Systems, Servers And Networks
In The Security World, the Bitter Truth is that no system or infrastructure is completely secure. New Exploits Are Discovered Daily, and their details are available on the Internet.
Performance of Systems: You can apply best security practices such as access control lists, permissions, server security, precise patch management, and accurate firewall configuration. Still, if hackers focus enough on the infrastructure, they will eventually find a loophole to infiltrate.
Therefore, as a security expert, it is essential to note that if everything is under control, what should you do if one succeeds in overcoming all security mechanisms? Security experts always consider the worst-case scenarios when implementing security mechanisms and use the side programs they have prepared for when a person succeeds in overcoming all security controls.
What is monitoring?
Monitoring means implementing policies, solutions, and security tools to monitor minor occurrences within networks or equipment. However, the critical point is properly implementing security mechanisms in the infrastructure.
For example, you need to know what tools to use in what part of the network to monitor employees’ and equipment’s activities closely without affecting their performance.
A large part of monitoring activities involves implementing network intrusion detection systems. Typically, security experts have a thorough knowledge of host-based intrusion detection mechanisms and network-based intrusion detection systems.
Important points to note about these two security mechanisms include the following:
- Activities of a system. A HIDS system can detect suspicious activity by viewing reports generated by Windows components.
- Network-based IDS: The Network-Based Intrusion Detection System (NIDS) collects network traffic and analyzes it to identify the nature of the suspicious activity. Network-based intrusion detection systems typically compare traffic to known attack signatures to identify suspects.
Surveillance systems, such as intrusion detection systems, can use various methods to detect suspicious activity. An intrusion detection system uses signatures or anomalies in network traffic to detect suspicious activity.
In contrast, a Signature-based monitoring system records activities and compares them to a database that defines known malicious activity.
A signature-based system produces few false positive alerts because it compares the activities performed on a system with the signatures it already has.
Because these systems seek specific activity, they produce little false alarm.
When a signature-based system is first installed on a system such as a server, it collects information about the server’s various functions and the equipment connected to it.
For example, an IP address sends SYN messages at short intervals to several ports connected to the system. The system collects this information about the IP address and maintains it as a port scan signature.
Then, whenever the address sends different messages, it compares the new information with the old news. If it detects a suspicious item, it sends a report to the network administrator.
Types of monitoring systems
A security expert should have complete information about the different surveillance systems. Standard security tools in this area include signature-based monitoring systems, anomaly-based surveillance, and exploratory analysis.
A signature-based system detects suspicious activity based on the signatures in a file; on the other hand, an anomaly-based system detects normal activities based on a baseline and considers any action outside the baseline abnormal and suspicious.
An exploration-based system detects suspicious activity based on a pre-defined configuration by the device manufacturer and activities that have previously caused security problems.
Exploration-based intrusion detection systems are great for dealing with zero-day exploits because zero-day exploits are still unknown, and a signature-based system does not yet have an exploit signature to deal with exploit-related threats.
An anomaly-based system understands regular activity; anything outside of normal activity is considered suspicious. An anomaly-based monitoring system typically uses a baseline to distinguish normal from abnormal activities.
The advantage of such systems is that they do not need to configure the file to define suspicious activity. Based on user activity, the system learns what is expected and questionable. The problem with anomaly-based systems is that they consider anything out of the regular traffic suspicious and generate a lot of false-positive warnings.
A honeypot is one of the most effective monitoring tools
One of the most important concepts embedded in surveillance systems is the Honeypot. Honeypot is a seemingly formal and straightforward system that aims to attract the attention of attackers in a system or network that will install.
Typically, honeypot systems are securely configured to force hackers to do more to gain access. While hackers break into the system, all their activities are recorded and audited to track the attacker.
Typically, security experts insert a fake file with an attractive title referring to an organization’s financial statements into the Honeypot to attract hackers.
This file is called Honey. For example, you can put a file called password.txt on the system desktop to view and open this file when an attacker enters the system. In this case, you can implement the audit on this text file to know when, by what IP address, and what tools it opens.
Monitoring tools
Intrusion detection or prevention systems perform very well and can detect many suspicious cases. However, sometimes circumstances require you to do some activities manually to see more accurate information in less time. Fortunately, it is possible to use operating system tools and peripherals with manual intrusion detection systems to monitor a design manually. You need to be familiar with proper operating system commands to do this.
Windows operating system commands
The Windows operating system provides network administrators with interesting application commands for monitoring system activity. The following are some of the most widely used and essential orders in this field:
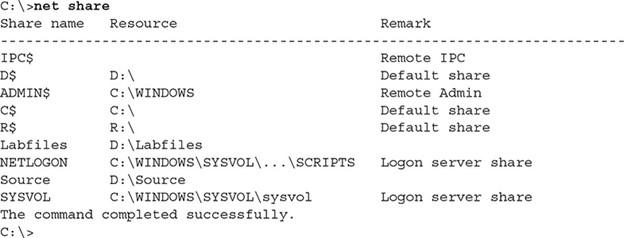
- Netstat: The first command you should be familiar with is Netstat. The netstat command is used to display comprehensive information about connections and protocols. For example, you can use the netstat -n command to view TCP connections to a system. In this case, the IP addresses and their protocols are displayed understandably. The netstat -na -o command is used to view a list of all listening ports on the system. The -o switch indicates the process ID in the above command to know what port programs it has opened.
- Net session: Network administrators use the net session command to view computers connected to a system through a file-sharing mechanism. The above command shows the list of sessions, the client’s IP address associated with the design, and their username for authentication. Figure 1 shows that the two computers (10.0.0.2 and 10.0.0.3) are connected to the same system and are authenticated through the administrator account.
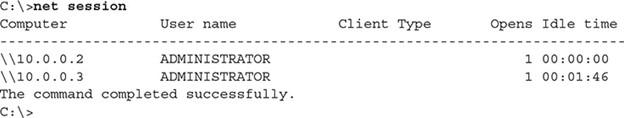
figure 1
- Tasklist: This is one of the favorite commands of network and security experts, and it provides a detailed report on the processes running in the system. When you use the netstat command with the -o switch, you get the program ID that opened the port. You can then use the tasklist command to find the executable file name (EXE) associated with that program or process for more information. Figure 2 shows the output of the above command.
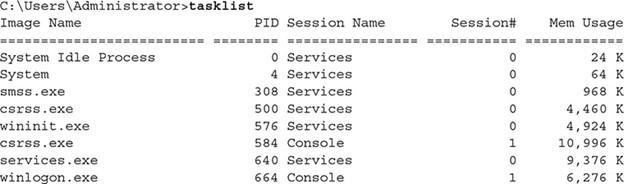
figure 2
- Taskkill: When monitoring a system, if you notice a painful process with performance or security issues, you can use the taskkill command to end the process. To terminate the execution of a function with the process ID number or executable file name, we use the following syntax:
taskkill /IM notepad.exe /F
If you are sure you want to terminate a process and do not want any data stored in the application, you must use the / F switch to end the execution of an application.
If you do not use the / F switch to complete a process in the above command, a request to save the changes will appear in a document, and the method or program will not end. The / IM switch in the above command is called Image Name, and the program name to be terminated will appear.
- Whoami: To get information about people logged in to a system, you should use the whoami command. This command displays the currently entered username. When using the whoami power, you can use the / groups switch to list the groups you are a member of or the / LOGONID switch to view the login ID. Both are useful for troubleshooting access control problems and show what groups you have defined on a server. In this case, you can delete or restrict the authority of these groups.
- Net statistics is another excellent Windows monitoring command that can closely monitor what is happening on the server. This command displays information such as the number of sessions admitted, the number of password breaches (failed login attempts), the number of licenses violated (lack of access to resources due to lack of permits), and activities related to printing in the system. This command gives you some exciting information about server performance.
Figure 3 shows the information visible with this command.
Figure 3
Other commands are used to monitor systems. For example, network and security experts use the net statistics workstation command to view information about client software installed on a plan and the number of requests sent to access network resources. For example, you can view information about each failed request to access resources on the network with that command.
View a list of users: One of the most important things you should do as a security expert is constantly monitoring users, groups, and shared resources. As shown in Figure 4, you can use the net user command to view a list of user accounts in the system.
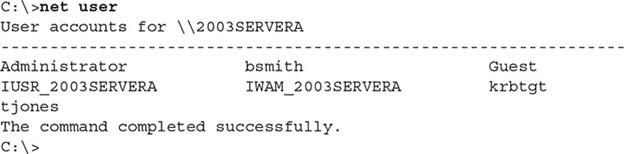
Figure 4
If you need more detailed information about shared groups and folders in a system, the net localgroup command is here. This command lists shared resources in the design and their location on a local disk.
In Figure 5, you can see a summary of the information displayed by the above command.
Figure 5
Linux operating system commands and protocols
The Linux operating system also has instructions for monitoring activities. Important security instructions in this regard include the following:
- Ps: This command is used to view a system’s running processes. The above knowledge is equivalent to the tasklist command in Windows. In Figure 6, you can see the information shown by the above command. When you use the ps command to view a list of processes, you may see a process you do not want to run in memory. To do this, you must use the kill command in Linux to terminate the process running in memory. For example, if a process running an operating system with an ID of 3139 is running, we use the following command to terminate it:
Kill 3139
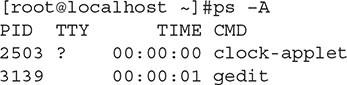
Figure 6
When monitoring user account activity, you can use the Last command to display the last time a user logged in. You can also use the previous log control to view a list of users and the last time they logged in (Figure 7).
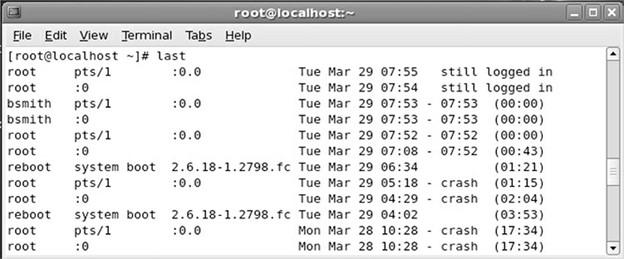
Figure 7
SNMP protocol
Simple Network Management Protocol (SNMP) is one of the oldest network protocols used to manage and monitor devices. Security experts use the above command to gather detailed information about devices running, memory consumed, CPU usage, and the number of users connected to the network.
This protocol also provides access to information about device configuration and settings. The point to note about the above protocol is that you can only use SNMP to monitor or manage a device if the target device supports the SNMP protocol. Of course, most routers, switches, and printers support this protocol.
Fortunately, software for automated use of the SNMP protocol is designed to connect to a device that supports the protocol, making the device data retrieval process more accessible.
From a security perspective, we recommend running the SNMPv3 protocol on your devices, as it is more secure than the original SNMP. SNMPv1 has relatively weak security and sends username and password in plain text.
The SNMPv2 version fixes some security issues, but SNMPv3 provides an accurate monitoring mechanism by encrypting credentials and deploying efficient security mechanisms.