Industrial Control System Security in 2025 & Beyond: Staying Resilient in a Connected World
Part I: “A Comprehensive Guide to ICS/SCADA in 2025”
A Comprehensive Guide to ICS/SCADA in 2025
Industrial Control Systems (ICS) and their significant subset, Supervisory Control and Data Acquisition (SCADA) systems, are technologies employed to manage and control industrial processes in sectors such as manufacturing, energy, water and wastewater, transportation, and other critical infrastructures.
These systems are designed with the objectives of automating processes, increasing productivity, and reducing human error. In the modern world, where dependence on industrial infrastructure is growing daily, the security and stability of these systems have become a paramount concern.
Part II: In-Depth Analysis: The State and Future of Industrial Cybersecurity
Section 1: Executive Summary
Overview
The security of industrial operations stands at a critical juncture. The accelerating convergence of Information Technology (IT) and Operational Technology (OT), driven by the pursuit of efficiency and data-driven insights, has irrevocably dismantled the legacy “air-gapped” security model.
This integration, combined with a threat landscape characterized by unprecedented sophistication and diversity, has rendered traditional defensive postures obsolete. For organizations managing critical infrastructure in 2025, the central challenge is no longer the prevention of every intrusion but the assurance of operational resilience in the face of inevitable compromise.
The systems that manage the physical world—from power grids and pipelines to manufacturing plants and water treatment facilities—are now firmly in the crosshairs of adversaries whose actions can have direct kinetic consequences. Navigating this new cyber-physical frontier requires a strategic realignment of governance, technology, and culture.
Key Findings
- Exponentially Expanded Attack Surface: The attack surface for critical infrastructure has grown dramatically. This expansion is a direct result of three concurrent trends: the deep integration of corporate IT networks with industrial OT networks; the proliferation of the Industrial Internet of Things (IIoT), which adds billions of potentially insecure endpoints; and the rollout of 5G technology, which introduces new levels of connectivity and complexity.
- Evolved and Diversified Threat Actors: Adversaries have matured far beyond simple disruption. The 2025 threat landscape is populated by nation-states conducting espionage and pre-positioning for future conflict; highly organized Ransomware-as-a-Service (RaaS) syndicates executing high-stakes extortion campaigns; and, most alarmingly, attackers targeting safety instrumented systems with the potential to cause physical harm and loss of life.
- Pervasive Internal Barriers: The most significant obstacles to effective industrial cybersecurity are often internal. These include the continued operation of legacy systems with unpatchable vulnerabilities, deep-seated cultural divides between IT and OT teams with conflicting priorities, and a persistent skills gap in personnel who understand both domains.
- Urgent Need for a Paradigm Shift: The historical reliance on perimeter security and the belief in a defensible “air gap” is no longer viable. A fundamental strategic shift is required towards a defense-in-depth, zero-trust architecture. This modern approach must be centered on achieving comprehensive asset visibility, ensuring operational resilience, and enabling rapid, effective response to incidents.
Strategic Recommendations
- Establish Unified IT/OT Governance: Organizations must dismantle the operational and cultural silos between IT and OT. This requires creating a unified cybersecurity governance structure with clear executive sponsorship, defined roles, and a shared risk management framework that respects the unique safety and reliability requirements of the OT environment.
- Invest in Visibility and Continuous Monitoring: A foundational security principle is that you cannot protect what you cannot see. Priority investment should be directed toward technologies that provide a complete and continuously updated inventory of all assets within the OT environment. This must be coupled with continuous network monitoring to establish a baseline of normal behavior and detect anomalies that may indicate a compromise.
- Adopt and Tailor the NIST Cybersecurity Framework: The NIST Cybersecurity Framework (CSF) provides a robust, flexible, and internationally recognized model for managing cyber risk. Organizations should formally adopt the CSF and meticulously tailor its functions—Identify, Protect, Detect, Respond, and Recover—to the specific context and constraints of their industrial operations.
- Develop and Test Cyber-Physical Incident Response Plans: The potential for cyberattacks to cause physical consequences necessitates specialized incident response planning. Organizations must develop, document, and regularly test response plans that explicitly account for cyber-physical scenarios. SANS Institute data reveals that only 52% of industrial facilities have a documented and tested ICS/OT-specific incident response plan, a critical vulnerability that must be addressed.
Section 2: The Cyber-Physical Nexus: Defining the Modern Industrial Battlefield
2.1. Introduction to Industrial Control Systems (ICS)
Industrial Control Systems (ICS) represent the nerve center of modern industry and critical infrastructure. It is an umbrella term encompassing a wide range of technologies designed to monitor and control physical processes. Unlike traditional IT systems that manage data, ICS manages physical machinery and operations. This category includes several key types of systems:
- Supervisory Control and Data Acquisition (SCADA): These systems are designed for remote monitoring and control of processes spread over large geographical areas. SCADA is fundamental to industries like oil and gas pipelines, electrical power transmission and distribution grids, and municipal water systems. Operators in a central control room use SCADA to gather data from remote sites and issue commands to equipment miles away.
- Distributed Control Systems (DCS): In contrast to the geographically dispersed nature of SCADA, DCS are typically used to control processes within a single, contained facility. Examples include chemical manufacturing plants, oil refineries, and power generation stations. A DCS uses a network of controllers distributed throughout the facility to manage complex, continuous production processes with a high degree of precision and reliability.
- Programmable Logic Controllers (PLCs): PLCs are the workhorses of industrial automation. These are ruggedized, real-time computers that form the direct interface between the digital control system and the physical world. Located at the lowest levels of the industrial network (often referred to as Level 1 and Level 0 of the Purdue Model), PLCs receive commands from SCADA or DCS systems and directly control actuators, motors, valves, and sensors on the plant floor. They are the components that execute the commands that have physical effects.
2.2. The Core Principle: Where Digital Commands Have Kinetic Consequences
The single most important characteristic that distinguishes Operational Technology (OT) from Information Technology (IT) is its direct interaction with the physical world. In an IT environment, the worst-case scenario of a security breach typically involves data loss, financial theft, or reputational damage. While severe, these consequences remain within the digital or economic realm. In an OT environment, the consequences are fundamentally different and far more dangerous.
A malicious command sent to a PLC, a compromised instruction within a DCS, or a loss of control in a SCADA system can have direct, irreversible physical or kinetic effects. This is the cyber-physical nexus. A successful attack can lead to catastrophic equipment failure, explosions, chemical spills, widespread power blackouts, contamination of water supplies, and, in the most severe cases, significant environmental damage and loss of human life.
The 1999 rupture of the Olympic Pipeline in Bellingham, Washington, serves as a stark, non-cybernetic illustration of this principle. A sequence of events, including a malfunctioning SCADA system that became unresponsive, prevented operators from mitigating a pressure buildup, leading to the pipeline’s rupture. The resulting gasoline spill and explosion killed three people and caused massive environmental and property damage.
This incident, driven by control system failure, provides a clear analog for the potential consequences of a malicious cyberattack that achieves the same end: the loss of safe control over a physical process. The threat is not just theoretical; it is a demonstrated reality that the failure of these systems, whether accidental or intentional, can be catastrophic.
2.3. The Scope of Critical Infrastructure
The reliance on ICS and SCADA systems is not confined to a few niche industries; it is foundational to the functioning of modern society. These technologies underpin the vast majority of sectors designated as critical infrastructure. This includes:
- Energy: Power generation (nuclear, fossil fuel, renewable), oil and gas extraction and refining, and electrical transmission and distribution grids.
- Water and Wastewater: Municipal water treatment and distribution systems, as well as wastewater collection and treatment facilities.
- Manufacturing: From automotive assembly lines to pharmaceutical production, manufacturing relies on precise, automated control.
- Transportation: Rail networks, air traffic control systems, and maritime port operations all depend on complex control systems.
- Building Automation: Modern commercial and government facilities use sophisticated building management systems (BMS) to control HVAC, lighting, and physical access control.
The ownership structure of this infrastructure amplifies the societal risk. In the United States, for example, approximately 90% of critical infrastructure is privately owned and operated. This reality makes robust public-private partnerships essential for national security and underscores the fact that the defense of these assets is a shared responsibility.
An attack on a private energy company is, in effect, an attack on the nation’s ability to function. This broad and deep integration of ICS into every facet of modern life means that its vulnerability is a systemic risk to economic stability, public safety, and national security.
The very definition of “security” in this context must be reframed. In the world of OT, the primary goal is not the protection of data for its own sake, but the assurance of the safe, reliable, and predictable operation of physical processes. The traditional IT security triad of Confidentiality, Integrity, and Availability (CIA) is reordered and redefined. For an OT engineer, the priorities are Safety, Reliability, and Productivity.
This fundamental difference in perspective is the root cause of many of the challenges in securing these converged environments. A security measure that protects data integrity but carries a small risk of causing a process to trip and go into a safe shutdown might be an acceptable trade-off in IT.
Still, it could be entirely unacceptable in an OT environment where unscheduled downtime costs millions of dollars per hour or jeopardizes a delicate continuous process. Understanding this core philosophical divide is the first step toward building an effective cyber-physical defense strategy.
Section 3: The Great Convergence: Navigating the IT/OT Integration Chasm
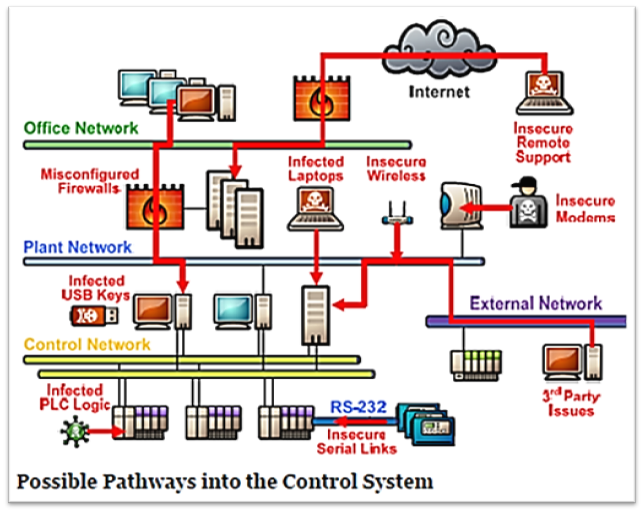
The historical model for securing industrial control systems was simple: isolation. OT networks were “air-gapped,” meaning they had no physical or logical connection to the corporate IT network or the public internet. This physical separation was the primary security control.
However, in the modern industrial landscape, this model is rapidly becoming obsolete. A powerful wave of IT/OT convergence is dismantling the air gap, driven not by technical mandates but by compelling business and economic imperatives.
3.1. The Business Drivers of Convergence
The integration of IT and OT systems is a strategic business decision aimed at unlocking significant value. Organizations are connecting their industrial environments to enterprise networks to achieve a range of benefits that enhance competitiveness and efficiency. Key drivers include:
- Enhanced Operational Efficiency: By feeding real-time data from OT systems (like sensor readings and equipment status) into IT-based analytics platforms, companies can gain unprecedented insight into their operations. This enables process optimization, reduces waste, and improves resource allocation.
- Predictive Maintenance: Analyzing historical and real-time operational data allows organizations to predict equipment failures before they happen. This shift from reactive to predictive maintenance minimizes costly unplanned downtime, extends the life of expensive industrial machinery, and improves overall productivity.
- Cost Reduction: Convergence allows for the elimination of redundant systems and streamlines processes. The use of commercial off-the-shelf (COTS) hardware and software in OT environments, enabled by IP-based networking, is often cheaper than proprietary legacy systems.
- Improved, Data-Driven Decision Making: Integrating the “shop floor to the top floor” provides senior leadership with a holistic view of the entire enterprise, from production metrics to financial performance. This enables more agile and informed strategic decision-making.
- Remote Access and Support: Connectivity allows for remote monitoring and maintenance of industrial systems, reducing the need for on-site personnel, enabling faster support from vendors, and improving worker safety by limiting exposure to hazardous environments.
3.2. Conflicting Worlds: The Foundational Differences Between IT and OT
While the business case for convergence is strong, the integration itself is fraught with friction. This is because IT and OT are two fundamentally different worlds, built on conflicting principles, technologies, and objectives.
Applying IT security practices directly to an OT environment without adaptation is not only ineffective but can be actively dangerous, potentially disrupting operations and creating safety risks.
- Divergent Priorities: The most critical difference lies in priorities. IT security is governed by the triad of Confidentiality, Integrity, and Availability (CIA), with the primary goal of protecting data. OT security, however, is driven by the physical process. Its priorities are Safety, Reliability, and Productivity. An OT engineer will almost always prioritize keeping a process running safely and continuously over implementing a security patch that requires downtime, even if it leaves a known vulnerability exposed.
- Vastly Different Lifecycles: IT assets like servers and laptops have a typical lifecycle of 3-5 years and operate on modern, frequently patched operating systems. In stark contrast, OT assets such as PLCs and DCS controllers are built to last for decades, with lifecycles of 15, 20, or even 30 years. Consequently, many industrial environments are filled with legacy systems running on unsupported operating systems like Windows XP or using proprietary communication protocols (e.g., Modbus, Profibus, DNP3) that were designed in an era before cybersecurity was a concern and often lack basic features like encryption or authentication.
- Opposing Risk Tolerances: The definition of risk differs dramatically. In IT, a significant incident might lead to a multi-million dollar data breach. In OT, a significant incident can lead to the destruction of a multi-billion-dollar plant, an environmental disaster, or human fatalities. The tolerance for any change that could impact the stability of the physical process is therefore extremely low.
- Contrasting Performance Requirements: IT networks are designed for high bandwidth to support applications like email and file transfers. OT networks are designed for high reliability and deterministic, low-latency communication, where a delay of milliseconds can disrupt a sensitive process. Standard IT security tools like antivirus scanners or network vulnerability scanners can overwhelm or crash fragile OT devices, making them unsuitable for direct deployment.
3.3. The Cultural and Organizational Divide
A deep cultural and organizational chasm mirrors these technical differences. IT and OT teams have historically operated in separate silos, governed by different management structures, using different terminology, and possessing different skill sets.
- IT professionals are trained in cybersecurity, networking, and data management, and they value innovation and agility.
- OT professionals are typically engineers (chemical, mechanical, electrical) whose expertise lies in the physical process, control theory, and ensuring operational safety and reliability. They value stability and predictability above all else.
This divide often leads to mistrust and poor communication. IT teams may view OT as technologically backward and insecure. In contrast, OT teams may see IT as a threat to operational stability, fearing that an IT-driven security initiative will “break something” on the plant floor.
A 2024 SANS Institute report noted that OT security functions often report up through IT chains of command, a structural weakness that can lead to the misapplication of IT-centric policies in the OT world. Bridging this cultural gap through cross-training, unified governance, and collaborative processes is one of the most critical and complex challenges of IT/OT convergence.
3.4. The Consequence: A Dramatically Expanded Attack Surface
The ultimate consequence of IT/OT convergence is the creation of a vast, interconnected attack surface. By connecting previously isolated OT networks to corporate IT networks, organizations have built a digital bridge for adversaries. Attackers can now compromise the less-secure, internet-facing IT environment and use it as a staging ground to pivot and move laterally into the high-consequence OT environment.
The data validates this risk unequivocally. A SANS survey revealed that 58% of all security incidents impacting ICS/OT systems originated from a compromise of the IT network. Another 33% were traced back to internet-accessible devices, highlighting the perils of eroding the air gap.
The Colonial Pipeline attack is the quintessential example of this phenomenon: a purely IT-based ransomware attack forced the shutdown of a massive physical infrastructure asset. In the converged world of 2025, securing the OT environment is impossible without first ensuring its connection to the IT world.
To crystallize these fundamental differences, the following table provides a direct comparison of the IT and OT security paradigms.
Table 1: Comparison of IT vs. OT Security Paradigms
Section 4: The 2025 Threat Landscape: A Multi-Vector Analysis
The threat landscape facing industrial control systems in 2025 is more complex, crowded, and dangerous than ever before. The convergence of IT and OT has exposed critical infrastructure to a wide array of adversaries with diverse motivations, from geopolitical dominance to pure financial gain. Understanding these actors and their methods is the first step toward building an effective defense.
4.1. The Adversaries: Who is Targeting Critical Infrastructure and Why?
The threats are no longer monolithic. Organizations must defend against multiple adversary types simultaneously, each with distinct goals and capabilities.
- Nation-State Actors: These are the most sophisticated and well-resourced adversaries, typically operating as arms of a government’s military or intelligence apparatus. Their motivations are geopolitical: espionage to steal intellectual property or state secrets, sabotage to disrupt a rival nation’s economy or infrastructure, and pre-positioning of malware within critical networks for use in future conflicts. Attacks like Stuxnet and the Ukrainian power grid compromises are classic examples of nation-state operations. They are characterized by their stealth, persistence, and focus on achieving strategic objectives rather than immediate financial return.
- Ransomware-as-a-Service (RaaS) Syndicates: This is the most significant and disruptive threat from a financial and operational standpoint. RaaS has industrialized cybercrime, turning it into a highly efficient business model. Core developer groups (like the former DarkSide, LockBit, and Clop gangs) create and maintain sophisticated ransomware, then lease it to “affiliates.” These affiliates conduct the attacks and share the ransom profits with the developers. This model dramatically lowers the technical barrier to entry, allowing a wider pool of criminals to launch devastating attacks. Critical infrastructure is a prime target because the cost of downtime is so immense that victims are under extreme pressure to pay the ransom. The Colonial Pipeline incident, perpetrated by a DarkSide affiliate, perfectly illustrates the RaaS model’s impact on the physical world.
- Hacktivists and Un-sophisticated Actors: This category includes individuals or groups motivated by ideology, as well as less-skilled attackers (sometimes called “script kiddies”). They often target low-hanging fruit, such as ICS/SCADA systems that have been carelessly exposed to the internet with default credentials or no passwords at all. While their methods may be unsophisticated, their impact can be significant if they manage to disrupt a critical process. U.S. government agencies have issued specific warnings about these actors targeting the oil and natural gas sector, noting that poor cyber hygiene at these facilities can turn a simple intrusion into a serious event.
- Insider Threats: This is a pervasive and often underestimated threat vector. Insiders are individuals with authorized access—employees, contractors, or third-party vendors—who pose a risk, either intentionally or unintentionally. An amalicious insider might intentionally sabotage a system for revenge or financial gain. However, the more common and arguably greater threat comes from the negligent insider. According to one study, negligent actions, such as falling for a phishing email, using weak passwords, or misconfiguring a system, account for 55% of all insider-related incidents in ICS environments. These incidents can be just as damaging as a malicious attack, and they originate from a trusted source, making them difficult to detect with traditional perimeter defenses.
4.2. Anatomy of an Intrusion: Common Attack Vectors and TTPs for 2025
While adversaries vary, their methods for gaining and exploiting access to industrial environments follow identifiable patterns, known as Tactics, Techniques, and Procedures (TTPs).
- Initial Access: The “way in” remains stubbornly consistent across threat actor types. The most prevalent initial access vectors are:
- Phishing and Spear-Phishing: Emails with malicious attachments or links remain a dominant entry point, often targeting engineers or administrative staff who have credentials or access to both IT and OT networks.
- Exploitation of Exposed Services: Attackers continuously scan the internet for vulnerable, externally-facing services like Remote Desktop Protocol (RDP) or Virtual Private Networks (VPNs) that are secured with weak or stolen credentials.
- Supply Chain Compromise: Attackers target less-secure third-party vendors or software suppliers to gain a foothold into their ultimate target. The infamous SolarWinds attack is a prime example of this technique in the IT space, and the principle applies directly to OT vendors.
- Malware Delivery: Once a phishing attempt is successful or a vulnerability is exploited, the initial payload is delivered. The most common forms are malicious scripts (JavaScript, HTML), weaponized Microsoft Office or PDF documents, and links to phishing pages designed to harvest credentials.
- Post-Compromise Activity: After gaining initial access, the attack progresses through several stages. Attackers engage in “living off the land,” using legitimate system administration tools (like PowerShell) for malicious purposes to evade detection. They focus on escalating privileges and moving laterally across the network, with the key goal of bridging the gap from the compromised IT network into the sensitive OT environment. Credential theft, using tools like Mimikatz, is a critical step in this process.
4.3. Threat Intelligence Snapshot (Q1 2025)
To move beyond qualitative descriptions, recent data provides a quantitative snapshot of the threats facing industrial systems. Analysis from Kaspersky for the first quarter of 2025 reveals a persistent and active threat environment.
Globally, 21.9% of all ICS computers experienced at least one malicious attack during this period, a figure that held steady from the previous quarter, indicating a consistent level of hostile activity. The primary sources of these threats were:
- The Internet: The leading threat vector, responsible for attacks on 10.11% of ICS computers. This highlights the erosion of the air gap and the risks of connecting OT systems to outside networks.
- Email Clients: The second most common source, impacting 2.81% of systems, confirms the effectiveness of phishing campaigns.
- Removable Media: Still a relevant vector, impacting 0.52% of computers, demonstrating that even physically isolated systems can be breached, as was the case with Stuxnet.
The following table details the most prevalent types of malware and threats blocked on ICS computers in Q1 2025, offering a clear picture of where defensive efforts should be focused.
Table 2: Q1 2025 ICS Threat Landscape Statistics
Source: Adapted from Kaspersky ICS CERT data for Q1 2025.
This data paints a clear picture: the perimeter is porous, and attackers are successfully using web and email-based attacks to breach industrial networks. The high prevalence of spyware indicates that many intrusions are focused on long-term intelligence gathering, a hallmark of nation-state actors. At the same time, the persistent threat of ransomware highlights the acute financial risk from cybercriminal syndicates.
Section 5: Anatomy of Failure: Landmark Incidents and Their Strategic Implications
To fully grasp the nature of the threat to industrial control systems, it is essential to analyze the landmark cyberattacks that have defined and shaped the field. These incidents are not merely historical footnotes; they are crucial data points on an evolutionary curve of adversary capability, intent, and impact. They reveal a clear progression from targeted state-sponsored sabotage to widespread disruption and, most recently, to attacks that directly endanger human life and leverage economic extortion.
5.1. Stuxnet (2007-2010): The Genesis of the Digital Weapon
- The Incident: Stuxnet was a watershed moment in cybersecurity. It was a highly complex and sophisticated computer worm, widely attributed to a joint U.S.-Israeli intelligence operation, designed with a single purpose: to sabotage Iran’s nuclear program physically. The malware was engineered to specifically target Siemens Step7 software, which controlled the PLCs managing the uranium enrichment centrifuges at the Natanz facility. To bypass the facility’s air-gapped security, the worm was introduced via infected USB drives.
- The Innovation: Stuxnet’s brilliance lay in its dual function. First, it subtly manipulated the rotational speed of the centrifuges, causing them to spin too fast or too slow, leading to excessive vibration and eventual physical destruction. Second, and just as critically, it recorded the normal operational data from the PLCs and played it back to the human-machine interface (HMI) screens in the control room. This meant that while the centrifuges were tearing themselves apart, the Iranian engineers saw only normal, healthy operations.
- The Enduring Lesson: Stuxnet shattered two long-held beliefs. It proved that air gaps are not infallible and can be breached by determined adversaries. More profoundly, it was the world’s first publicly acknowledged digital weapon—malware that crossed the “Rubicon” from the digital realm to cause tangible, kinetic damage in the physical world. It set a dangerous and irreversible precedent, demonstrating that cyber operations could be used as an instrument of national power to achieve physical effects, heralding a new era of cyber warfare.
5.2. Triton/TRISIS (2017): The Assault on Safety and Trust
- The Incident: If Stuxnet was about sabotage, the Triton malware (also known as TRISIS or HatMan) represented a far more terrifying escalation. In 2017, attackers targeted a petrochemical facility in Saudi Arabia. Their weapon was a custom-built malware framework explicitly aimed at the Schneider Electric Triconex Safety Instrumented System (SIS). An SIS is the last line of automated defense in an industrial process. It is an independent system designed to detect dangerous conditions (like excessive pressure or temperature) and automatically trigger a safe shutdown to prevent a catastrophic failure, such as an explosion or toxic release.
- The Innovation: The attackers’ goal was not merely to disrupt production. By compromising the SIS, they intended to turn off the very system designed to protect human life. This would have allowed them to subsequently manipulate the central process control system to create a dangerous event, confident that the safety system would not intervene. The attack was only discovered by accident when a flaw in the Triton malware itself inadvertently caused some SIS controllers to enter a fail-safe state, tripping the plant offline and alerting engineers that something was wrong.
- The Enduring Lesson: Triton demonstrated a chilling evolution in adversary intent, from causing operational or economic damage to enabling potential mass-casualty events. The attackers, believed to be a Russian state-sponsored group, invested significant time and resources to reverse-engineer the proprietary Triconex protocols, showcasing a level of dedication aimed at creating a capability for physical destruction. Triton fundamentally changed the threat model for critical infrastructure, proving that attackers were now willing and able to target the systems that serve as the ultimate safeguard for human life.
5.3. Colonial Pipeline (2021): The IT-OT Dependency Crisis
- The Incident: In May 2021, the largest fuel pipeline in the United States, supplying 45% of the East Coast’s gasoline, diesel, and jet fuel, was shut down for nearly a week. The cause was a ransomware attack perpetrated by the DarkSide RaaS group. The attackers gained their initial foothold through a single, compromised password for a VPN account that was not protected by multi-factor authentication. They stole approximately 100 gigabytes of data and then encrypted the company’s IT systems, including its billing and accounting infrastructure.
- The Innovation: The Colonial Pipeline attack was unique because the ransomware did not directly infect the OT network or the pipeline control systems. The company’s leadership decided to proactively shut down the pipeline for two primary reasons: out of an abundance of caution, fearing the attackers could pivot from the IT network to the OT network, and, more pragmatically, because the encrypted billing systems meant they could no longer track fuel flow and bill their customers.
- The Enduring Lesson: This incident was a stark and public demonstration of the critical dependency of OT on IT in a converged environment. It proved that an attack confined solely to the corporate IT network could be sufficient to cripple national critical infrastructure. The concept of a secure OT network isolated from IT risk was shown to be a fallacy. The attack caused widespread fuel shortages, panic buying, and a state of emergency, highlighting the profound societal impact of such disruptions and sparking a fierce debate about the wisdom of paying the $4.4 million ransom.
5.4. Ukrainian Power Grid Attacks (2015): A Blueprint for Infrastructure Warfare
- The Incident: In December 2015, in a meticulously planned operation attributed to Russia, attackers executed the first confirmed cyberattack to take down a nation’s power grid successfully. They targeted multiple electricity distribution companies in western Ukraine, culminating in a power outage for over 230,000 residents that lasted for up to six hours.
- The Innovation: The attack was a masterclass in coordinated cyber warfare. The attackers used spear-phishing emails with malicious Microsoft Office attachments to gain initial access and harvest credentials from IT staff. They then moved laterally into the SCADA network, familiarized themselves with the operations, and used the operators’ remote administration tools to remotely open circuit breakers at dozens of substations simultaneously. To maximize chaos, they also wiped server hard drives to hinder recovery. They launched a telephone denial-of-service (TDoS) attack against the utility’s call centers to prevent customers from reporting the outage.
- The Enduring Lesson: The Ukrainian grid attack provided a real-world playbook for how to use cyber capabilities as an instrument of state power to disrupt a rival’s critical infrastructure. It demonstrated a sophisticated understanding of both IT hacking techniques and OT industrial processes, and it blended technical intrusion with psychological operations to sow confusion and amplify the attack’s impact. It was a clear signal that cyberattacks on infrastructure were no longer theoretical but a proven component of modern conflict.
These incidents, when viewed together, reveal a clear and disturbing trajectory. The threat has evolved from targeted, clandestine sabotage (Stuxnet) to overt, disruptive warfare (Ukraine), to attacks that directly threaten human safety (Triton), and finally to a model where the vast economic leverage of critical infrastructure is exploited for financial extortion (Colonial Pipeline).
This evolution is not linear; instead, the capabilities and motivations are blending. The rise of the RaaS model means that the sophisticated techniques once reserved for nation-states are now available to a much broader range of criminals. A future attack could easily combine the financial motive of a ransomware gang with the catastrophic potential of a Triton-style assault on safety systems, making the defensive challenge more complex than ever.
Table 3: Landmark ICS Cyber Incidents: Summary and Key Lessons
| Incident Name (Year) | Target System/Industry | Primary Attack Vector / Malware | Key Consequence (Impact) | Enduring Strategic Lesson |
| Stuxnet (2007-2010) | Siemens PLCs in the Iranian Nuclear Enrichment Facility | Highly specialized worm (Stuxnet) delivered via USB to breach the air gap. | Physical destruction of ~1,000 centrifuges while hiding the attack from operators. | Proved that air gaps are fallible and that cyber weapons can cause targeted kinetic damage, ushering in the era of cyber warfare. |
| Triton (TRISIS) (2017) | Schneider Electric Triconex Safety Instrumented System (SIS) in a Saudi Petrochemical Plant | Custom malware (Triton) targeting proprietary SIS protocols, likely via spear-phishing. | Disablement of safety systems, which could have enabled a catastrophic physical event, was discovered by accident. | Adversary intent evolved from disruption to targeting systems designed to protect human life, fundamentally changing the risk calculus. |
| Colonial Pipeline (2021) | IT Billing Systems of a significant U.S. Fuel Pipeline | Ransomware (DarkSide) was deployed after initial access via a single compromised VPN password. | Proactive shutdown of the entire pipeline, causing massive fuel shortages on the U.S. East Coast. | Demonstrated the critical dependency of OT on IT; a purely IT-based attack can cripple the national critical infrastructure. |
| Ukraine Power Grid (2015) | SCADA Systems of Ukrainian Electricity Distribution Companies | Coordinated attack using spear-phishing, credential theft, and remote operation of SCADA systems. | First confirmed cyberattack to take down a power grid, affecting over 230,000 people. | Provided a real-world blueprint for using cyberattacks as an instrument of state power to disrupt civilian infrastructure. |
Section 6: Architecting Resilience: Frameworks and Best Practices for Cyber-Physical Defense
In the face of a sophisticated and persistent threat landscape, the traditional cybersecurity objective of perfect prevention is no longer a realistic goal for industrial organizations. The focus must shift from building impenetrable walls to architecting resilience—the ability to anticipate, withstand, and recover from a cyberattack while maintaining critical operational functions. This requires a multi-layered, defense-in-depth strategy that integrates technology, processes, and people.
6.1. The Paradigm Shift: From Prevention to Resilience
The “air gap” is gone, and the perimeter is porous. Adversaries have repeatedly demonstrated their ability to bypass traditional defenses. Therefore, a modern industrial cybersecurity program must operate under the assumption that a breach will eventually occur.
The strategic goal is not to prevent 100% of intrusions but to ensure that when an intrusion happens, it can be detected quickly, contained effectively, and eradicated before it can impact the safety, reliability, or productivity of the physical process. This resilience-focused approach is the core principle of defense-in-depth, where multiple layers of defense are implemented so that the failure of a single control does not lead to a catastrophic compromise.
6.2. Implementing the NIST Cybersecurity Framework (CSF) in OT
The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) is the most widely adopted and respected model for managing cybersecurity risk. While developed with IT in mind, its principles are flexible and can be effectively tailored to the unique challenges of the OT environment. The CSF organizes cybersecurity activities into five core functions:
- Identify: This is the foundational function. An organization cannot protect what it does not know it has. For OT, this means going beyond a simple IT asset list and creating a comprehensive, detailed inventory of all industrial assets, including PLCs, HMIs, RTUs, network switches, and their associated software and firmware versions. This is a critical first step that many organizations have yet to complete, often due to the complexity and geographic dispersion of their assets.
- Protect: This function involves implementing safeguards to ensure the delivery of critical services and limit the impact of a potential event. In an OT context, this translates to core technical controls like robust physical security, strong network segmentation to isolate critical processes, secure remote access protocols with multi-factor authentication (MFA), and access control based on the principle of least privilege, ensuring users and systems only have the permissions essential for their roles.
- Detect: Given the assumption of a breach, rapid detection is paramount. This function requires the deployment of tools and processes to identify cybersecurity events promptly. Essential capabilities for OT include continuous monitoring of network traffic for anomalous behavior, centralized logging of all system and user activity, and the use of Intrusion Detection Systems (IDS) that are specifically designed to understand industrial protocols (like Modbus or DNP3) and can spot malicious or unauthorized commands.
- Respond: This function focuses on having a well-defined and rehearsed plan to take action once an incident is detected. For industrial environments, this is more than a standard IT incident response plan. It must be an ICS-specific incident response plan that considers the physical consequences of both the attack and the response actions. The plan must be documented, and critically, it must be regularly tested through tabletop exercises and drills. Shockingly, SANS Institute data shows that only 52% of industrial facilities have such a plan in place, representing a massive gap in preparedness.
- Recover: This function deals with restoring capabilities and services that were impaired during an incident. Key elements for OT include maintaining reliable, tested, and isolated backups of critical system configurations and software (especially for PLCs and engineering workstations). It also involves having a documented recovery plan that may include the ability to switch to manual operations to maintain the process while digital systems are being restored.
6.3. Essential Technical Controls: The Pillars of Defense-in-Depth
While the NIST CSF provides the strategic framework, its implementation relies on a set of fundamental technical controls.
- Network Segmentation and Segregation: This is arguably the single most crucial architectural control for protecting OT environments. The goal is to divide the network into smaller, isolated zones to limit an attacker’s ability to move laterally after an initial compromise. At a minimum, the OT network must be strictly segregated from the IT network using firewalls and a Demilitarized Zone (DMZ) to broker all communication. Within the OT network, further micro-segmentation can be used to isolate the most critical control systems from less critical assets, ensuring that a compromise in one area does not cascade across the entire plant.
- Secure Remote Access: As a primary vector for intrusions, remote access must be rigorously controlled. All remote access to the OT network should be prohibited by default and only allowed on a case-by-case basis through a secure, monitored pathway, such as a jump server or bastion host located in the DMZ. All remote sessions must be protected by strong, phishing-resistant Multi-Factor Authentication (MFA) and should be logged and monitored for suspicious activity.
- Vulnerability and Patch Management: This is a profound challenge in OT due to the high cost of downtime and the risk of a patch causing system instability. A “patch everything immediately” approach from IT is not feasible. Instead, organizations must adopt a risk-based vulnerability management program. This involves using the asset inventory to identify vulnerable systems, assessing the risk of each vulnerability in the context of the specific operational environment, and prioritizing patching accordingly. Where patching is not immediately possible, compensating controls—such as using an Intrusion Prevention System (IPS) to create “virtual patches” that block known exploits, or tightening network access controls around the vulnerable device—must be implemented.
- Asset and Configuration Management: A complete asset inventory is the starting point, but it must be maintained. Organizations need a process for configuration management, which involves establishing a secure, documented baseline for every critical device and then continuously monitoring for any unauthorized changes. Detecting an unexpected change to a PLC’s logic or a firewall rule can be the earliest indicator of a compromise.
6.4. The Human Firewall: People, Processes, and Culture
Technology alone is insufficient. The most sophisticated defenses can be undermined by human error or a poor security culture.
- Tailored Security Awareness Training: Training programs must be specifically designed for the OT workforce. They need to go beyond generic anti-phishing guidance and address OT-specific risks, such as the dangers of using unauthorized removable media (USB drives), the importance of physical security, and how social engineering attacks can be crafted to manipulate operational personnel.
- Insider Threat Mitigation: Addressing insider threats requires a combination of technical monitoring (logging user activity, detecting anomalous access patterns) and strong organizational processes. This includes strict access control policies, background checks for personnel in critical roles, and clear procedures for off-boarding employees and contractors to ensure their access is immediately revoked.
- Incident Response Planning and Drills: A plan on a shelf is useless. The ICS incident response plan must be a living document, continuously refined through regular tabletop exercises and functional drills. These exercises are critical for building “muscle memory” and ensuring that both IT and OT teams understand their roles and can work together effectively under the extreme pressure of a real cyber-physical incident.
The following table provides a practical guide for translating the NIST CSF for implementation within an OT environment.
Table 4: NIST Cybersecurity Framework (CSF) Application in an OT Environment
| NIST CSF Function | Core Objective | Example IT Implementation | Critical OT-Specific Implementation |
| Identify | Understand and manage cybersecurity risk to systems, assets, data, and capabilities. | Automated discovery of servers and endpoints on the corporate network. | Use a combination of passive monitoring and safe, active polling to create a comprehensive inventory of all OT assets (PLCs, RTUs, HMIs, IEDs), including make, model, firmware version, and communication paths. |
| Protect | Implement safeguards to ensure delivery of critical services and contain the impact of an event. | Deploying antivirus software and enforcing password complexity policies on user laptops. | Implementing strict network segmentation between IT and OT, enforcing least privilege on OT accounts, securing all remote access with MFA via a DMZ, and ensuring robust physical security for control centers and field devices. |
| Detect | Develop and implement activities to identify the occurrence of a cybersecurity event. | Using a Security Information and Event Management (SIEM) tool to analyze logs from IT systems for known attack signatures. | Deploying an OT-native network monitoring solution that understands industrial protocols to detect anomalous commands or traffic patterns. Centralizing and monitoring logs from HMIs and engineering workstations for unauthorized activity. |
| Respond | Take action regarding a detected cybersecurity incident. | Isolating an infected laptop from the network and reimaging it from a clean backup. | Executing a practiced ICS incident response plan that prioritizes operational safety. Actions may include isolating a network segment, failing over to redundant controllers, or transitioning to manual operation, all while coordinating with plant engineers. |
| Recover | Implement activities to maintain resilience and restore capabilities impaired by an incident. | Restoring data from cloud backups to a new server after a ransomware attack. | Restoring PLC logic from verified, offline backups. Following a documented plan to safely bring the physical process back online, verify the integrity of all control system configurations before resuming automated operation. |
Section 7: The Next Frontier: Emerging Technologies and Future Challenges
As industrial organizations look toward 2025 and beyond, the security landscape is being reshaped by a trio of powerful, interconnected technologies: the Industrial Internet of Things (IIoT), 5G wireless communication, and Artificial Intelligence (AI). While each offers transformative potential for efficiency and innovation, they also introduce profound new security challenges and compound existing risks.
7.1. Securing the Industrial Internet of Things (IIoT)
- The Challenge: The IIoT represents the massive expansion of connectivity to billions of low-cost sensors, actuators, and other “smart” devices embedded throughout the industrial environment. This proliferation creates an enormous and often unmanageable attack surface. Many IIoT devices are designed and built with a focus on cost and functionality, not security. They frequently ship with default, hardcoded credentials, lack mechanisms for secure updates or patching, and use insecure communication protocols, making them easy targets for attackers.
- The Risks: The security weaknesses of IIoT devices create significant risks. A compromised smart sensor could be used to feed false data into a control system, leading to poor operational decisions or even unsafe conditions. More critically, an insecure IIoT device connected to the industrial network can serve as an initial entry point for an attacker, providing a foothold from which they can pivot to attack more critical systems like PLCs or the DCS. The long operational lifespan of these devices means that vulnerabilities can persist in the field for years, creating a permanent, exploitable risk.
- Mitigation Strategies: Securing the IIoT ecosystem is impossible without adopting a zero-trust architecture, where no device is trusted by default, regardless of its location on the network. Key mitigation strategies include:
- Comprehensive Asset Discovery: Organizations must have automated tools to discover, identify, and inventory every IIoT device on their network.
- Network Segmentation: IIoT devices should be placed on isolated network segments, separate from the core control network, to contain the impact of a potential compromise.
- Continuous Behavioral Monitoring: Since patching is often not an option, security relies on monitoring device behavior for anomalies. Any deviation from a device’s standard communication patterns should trigger an alert.
- Secure Lifecycle Management: Implementing strong credential management to eliminate default passwords, ensuring firmware integrity, and having a plan for securely decommissioning end-of-life devices are crucial process controls.
7.2. The 5G Revolution: A Double-Edged Sword
- The Promise: Fifth-generation (5G) wireless technology is poised to revolutionize industrial operations. Its key features—ultra-reliable low-latency communication (URLLC), massive machine-type communications (mMTC), and enhanced mobile broadband (eMBB)—enable applications that were previously impossible. These include real-time control of mobile robotics, large-scale wireless sensor networks, and remote operations requiring near-instantaneous feedback.
- The Peril: The architecture of 5G is fundamentally different from previous generations. It is heavily reliant on software, virtualization, and cloud-native principles, which introduce a new class of vulnerabilities. The attack surface is expanded due to more numerous and open interfaces between network components. Key risks include:
- Cloud and Edge Misconfigurations: As network functions move to virtualized infrastructure in public or private clouds, misconfigured APIs or insecure containers can expose critical network controls.
- Network Slicing Vulnerabilities: Network slicing allows for the creation of multiple virtual networks on a shared physical infrastructure. A misconfigured or hijacked slice could potentially bypass security controls and impact other slices.
- Supply Chain Risks: 5G networks are built from a complex global supply chain of hardware and software. The introduction of untrusted or compromised components poses a significant risk to the integrity of the entire network.
- Legacy Infrastructure Integration: Early 5G deployments are often non-standalone, meaning they are built upon existing 4G LTE infrastructure. This can cause legacy vulnerabilities from the 4G core to be inherited by the new 5G network.
- The Way Forward: Security for 5G in industrial environments cannot be an afterthought; it must be a core design principle. This requires a “secure-by-design” approach that involves hardening the configuration of all network functions and slices, implementing robust authentication and encryption for all communications, and carefully vetting all components in the supply chain.
7.3. The AI Arms Race: The Future of Attack and Defense
- AI for Defense: Artificial Intelligence (AI) and Machine Learning (ML) are becoming indispensable tools for defending complex industrial environments. Their ability to process massive volumes of data in real-time allows them to achieve what human analysts cannot. Key defensive applications include:
- Anomaly Detection: AI/ML algorithms can learn the standard baseline of behavior for an entire OT network—every device, every protocol, every communication path. They can then detect subtle deviations from this baseline that may indicate a novel, zero-day, or insider threat that would be invisible to traditional signature-based security tools.
- Enhanced Asset Inventory: AI can automate the process of identifying and classifying all connected devices, enriching the inventory with contextual data that helps prioritize security efforts.
- Predictive Threat Analysis: By analyzing global threat intelligence and historical attack data, AI can help predict future attack trends, enabling organizations to strengthen their defenses proactively.
- AI for Offense: Adversaries are also weaponizing AI. They are using AI to develop polymorphic malware that constantly changes its code to evade detection, to automate reconnaissance and vulnerability discovery on a massive scale, and to craft compelling, personalized spear-phishing campaigns that are difficult for humans to spot. The AI arms race is on, and defenders must assume that attackers will have access to capabilities as sophisticated as their own.
- The Human-in-the-Loop Imperative: Despite its power, AI is not a panacea, especially in a safety-critical OT environment. The risk of a “false positive”—where an AI system mistakenly identifies a legitimate operational command as malicious—is a profound concern. An automated AI response that blocks a critical safety function or shuts down a process could be catastrophic. Therefore, the role of AI in OT security must be to augment, not replace, the human operator. AI should serve as a robust analysis and alerting tool, providing human security and engineering teams with the high-fidelity intelligence they need to make fast, informed, and safe decisions.
The convergence of these three technologies creates a compounding effect on both capability and risk. 5G provides the ubiquitous, low-latency connectivity required for massive IIoT deployments, while AI provides the analytical power needed to secure and manage this vast, complex ecosystem.
However, this deep interdependence means that risk in one domain can cascade across the others. A vulnerability in the 5G network layer could be exploited to launch a simultaneous attack on millions of connected IIoT devices.
A compromised AI security platform could be manipulated by an adversary to ignore a real attack or, conversely, to cause a denial-of-service against the very industrial process it is meant to protect. A holistic security strategy for 2025 and beyond must address these interdependencies, securing the system-of-systems, not just the individual technologies in isolation.
Section 8: Strategic Recommendations and Concluding Outlook
Securing the cyber-physical frontier is a complex, multi-faceted challenge that requires a coordinated and strategic response from all levels of an organization, as well as from the broader ecosystem of policymakers and regulators. The following recommendations are tailored to provide actionable guidance for key stakeholder groups.
8.1. For Corporate Leadership (CISOs, COOs, CEOs)
The ultimate responsibility for industrial cybersecurity rests with executive leadership, who must set the tone, allocate resources, and establish the governance structures necessary for success.
- Establish Unified Governance: The most critical first step is to definitively break down the organizational and cultural silos between Information Technology (IT) and Operational Technology (OT). Leadership must champion and enforce the creation of a unified cybersecurity governance structure. This structure should have a clear executive sponsor, well-defined roles and responsibilities for both IT and OT personnel, and a single, integrated risk management framework that acknowledges and respects the unique safety and reliability priorities of the industrial environment.
- Fund Resilience, Not Just Prevention: Budgeting for cybersecurity must evolve. The historical focus on building a strong perimeter (prevention) is no longer sufficient. A significant portion of investment must be reallocated to capabilities that support resilience. This means funding robust programs for comprehensive asset visibility, continuous threat detection, incident response, and operational recovery. The goal is to ensure the business can survive and quickly recover from an attack, not just try to prevent it.
- Treat Cyber-Physical Risk as a Core Business Risk: OT cybersecurity cannot be treated as a niche technical issue. It is a fundamental business risk with the potential for catastrophic financial, reputational, and safety impacts. Leadership must integrate OT cyber risk into the organization’s overall enterprise risk management (ERM) program. CISOs and COOs should be required to report on OT security posture to the board of directors, framing the discussion in terms of operational impact, potential downtime, and safety consequences, not just technical metrics like vulnerabilities patched. With Gartner predicting that CEOs may be held personally liable for OT attacks that harm humans by 2025, this has become a matter of fiduciary duty.
8.2. For Operations and Security Managers
Managers on the front lines of IT and OT are responsible for translating strategy into action. Their focus should be on mastering the fundamentals and preparing their teams for a real-world incident.
- Prioritize Visibility: The maxim “you cannot defend what you cannot see” is the first principle of industrial security. The highest priority for managers should be to achieve and maintain a complete, accurate, and continuously updated inventory of all assets within the OT environment. This includes not only servers and workstations but every PLC, RTU, HMI, and IIoT device. This visibility is the prerequisite for all other security activities, from vulnerability management to incident response.
- Master the Fundamentals: While emerging threats are a concern, the vast majority of successful attacks exploit elemental weaknesses in security hygiene. Managers must drive a relentless focus on the fundamentals: implementing and enforcing strong access control policies (least privilege), ensuring robust network segmentation to contain threats, and establishing a pragmatic, risk-based program for managing vulnerabilities. These foundational controls provide the greatest return on investment for reducing risk.
- Plan, Practice, and Drill: An untested incident response plan is not a plan; it is a theory. Managers must ensure that a comprehensive, ICS-specific incident response plan is not only developed but is also regularly practiced. This means conducting realistic tabletop exercises and functional drills that involve both IT and OT personnel. These exercises build the “muscle memory” and collaborative relationships needed to respond effectively under the extreme pressure of a cyber-physical crisis.
8.3. For Policymakers and Regulators
The government has a critical role to play in raising the baseline of security across all critical infrastructure sectors.
- Promote Harmonized, Performance-Based Regulation: Where regulation is necessary, it should move away from rigid, prescriptive checklists that can quickly become outdated. Instead, policy should encourage the adoption of flexible, performance-based frameworks like the NIST CSF. This approach allows organizations to manage risk in a way that is best suited to their specific environment and technology, fostering a culture of continuous improvement rather than rote compliance.
- Foster Public-Private Information Sharing: Incidents like the Colonial Pipeline attack revealed critical communication gaps, where government agencies were not alerted to the attack or the ransom payment promptly. Policymakers must work to strengthen and streamline mechanisms for trusted, bi-directional sharing of threat intelligence and incident data between the private sector and government agencies like CISA. This allows for a more coordinated national response and helps warn other potential victims.
- Incentivize “Secure-by-Design”: For too long, the burden of securing industrial devices has fallen on the end-user. Policymakers should explore regulations and incentives that shift this responsibility upstream, encouraging or mandating that manufacturers of OT and IIoT equipment build security into their products from the very beginning of the design process. This includes eliminating default passwords, providing mechanisms for secure updates, and building on secure-by-design principles.
8.4. Concluding Outlook: The Unceasing Vigil
The convergence of our physical and digital worlds is complete and irreversible. The systems that control our most critical infrastructure are now inextricably linked to the global network, bringing with them both immense efficiencies and profound risks. Securing this cyber-physical frontier is not a project with a defined endpoint; it is a continuous process of adaptation, learning, and vigilance.
The threats will continue to evolve. Adversaries will become more sophisticated, their motivations will shift, and new technologies will introduce unforeseen vulnerabilities. The challenge is immense, but it is not insurmountable. By fostering a culture of security that bridges the IT/OT divide, by committing to the fundamentals of cyber hygiene, by embracing resilience as a core strategic objective, and by building strong partnerships between industry and government, we can effectively manage the risks.
The safety of our communities, the stability of our economies, and the security of our nations depend on our collective ability to defend this new frontier with an unceasing vigil.
FAQ
What makes ICS security more challenging in 2025 compared to the past?
New connectivity (IIoT, cloud, remote access), legacy systems with weak or no security, insecure proprietary protocols, and convergence of OT (Operational Technology) with IT have all expanded the attack surface.
What are the most common threats to Industrial Control Systems today?
Some of the major threats include malware (like Stuxnet-style attacks), Denial-of-Service (DoS), insider threats, third-party/vendor breaches, and exploiting vulnerabilities in outdated firmware or insecure protocols.
How can organizations build resilience and protect their ICS for the future?
Key strategies include: Performing risk assessments and maintaining up-to-date asset inventories. Network segmentation and creating secure zones / DMZs between IT and OT. Using secure and modern communication protocols, patching systems regularly, enforcing strong authentication. Implementing continuous monitoring, anomaly detection, and layering defenses (defense-in-depth).