How to Increase Cloud Storage Security
Cloud Storage Security: Data storage in the cloud Must Be Secure Against Cyber Attacks. This Article Discusses Cloud Security And How to Secure Your Cloud Servers.
Define cloud storage security.
Cloud-based Internet security is an outsourcing solution for data storage. Instead of storing data on local hard disks, users store data on Internet-connected servers. Data centers manage these servers for secure access and data storage.
Companies have turned to cloud storage solutions to solve various problems, and small businesses use the cloud to cut costs. Whenever you remotely access saved files, you are actually accessing a cloud. IT professionals have devised the best way to store sensitive data in the cloud.
You can refer to the linked article for information about the DBaaS cloud database.
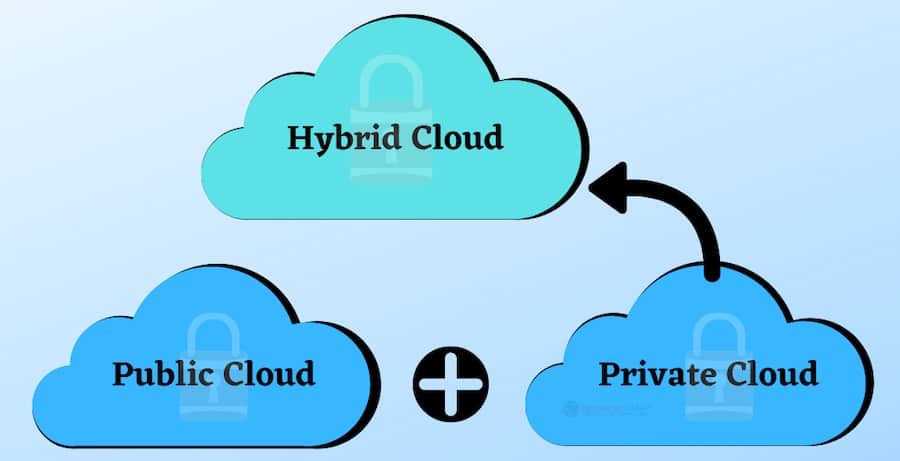
Cloud types: public, private, hybrid
There are three models of cloud computing. Each of these has a specific combination of advantages and disadvantages. Here is a brief description of each. You can refer to the article on Types of Cloud Computing Models for more information.
Public cloud: These services provide access and security. This security is suitable for unstructured data, such as files in folders. This type of public cloud does not provide user control, but it is a cost-effective option.
Private Cloud: Private cloud services are on-site solutions. Users have unlimited control over the system. Private cloud storage is more expensive because the owner of the physical hardware manages and maintains it themselves.
Hybrid cloud: Many companies keep large files in a public cloud and sensitive data in a private cloud. This hybrid approach strikes a balance between cost-effectiveness and personalization.
How To Reach Cloud Storage Security?
Advanced security measures will protect all files stored on secure cloud servers. The security credential that most users are familiar with is the password. Cloud storage security providers secure data using methods beyond encryption.
Some of these are:
Advanced Firewalls: Firewalls inspect data packets. These programs then scan the contents of packages known to contain security threats. In the simplest case, they only check the source and destination data. Advanced verification confirms the contents of the package.
Intrusion Detection: Secure online storage can serve many users simultaneously. Successful cloud security systems rely on identification when identifying someone trying to log in. Having multiple levels of identification gives suppliers the confidence that they can stop intruders from targeting the first layer of the network.
Event Log: Event information helps security analysts understand threats. These sets record network actions. Analysts use this data to document network events, which allows them to anticipate and prevent security vulnerabilities.
Internal firewalls: Not all accounts should have full access to cloud data. This ensures that even a verified account cannot have complete access. Restricting secure cloud access through built-in firewalls increases security.
Encryption: Encryption protects data against unauthorized users. If an attacker steals an encrypted file, he cannot access its information unless he has the secret key. As a result, data is worthless to anyone without a key.
Physical security: Cloud data centers are very secure. Authentic data centers feature 24-hour surveillance, fingerprint locks, and armed security. These locations are more secure than almost any data center. Cloud suppliers take different approaches to each of these factors. For example, some cloud storage systems hide user encryption keys from other users. Others give encryption keys to their users.
First-class cloud infrastructure strikes the ideal balance between access and security. Even if you trust users, they may accidentally give the keys to an unauthorized person. The user must follow safety instructions when using the cloud. There are many different ways to build a cloud security framework.

Cloud data security risks
Security breaches are rarely caused by poor cloud data protection. More than 40% of data security breaches are caused by employee error. Improving user security is one of the most important recommendations for further securing cloud storage space. Many factors affect user security in the cloud storage system. Many of these focus on staff training:
Authentication: Poor passwords are the most common corporate security vulnerability. Many employees write their passwords on paper, which can compromise security. Multi-factor authentication can solve this problem.
Awareness: Cybersecurity is paramount. In organizational work, Employees need to know why security is so important and be trained to be aware of it. Users need to understand how enterprise systems destroy intruders. Users must provide common responses to each type of attack.
Phishing Protection: Phishing scams are the most common form of cyber attack. These attacks try to compromise the user’s email and passwords. Attackers can then log in to commercial systems to access more sensitive files.
Attack Simulation: A Data attack simulation can help employees detect and prevent phishing attacks. This type includes protocols for performing the suspicious activity and for giving users feedback. Users can also improve response time in the event of an actual breach.
Measurement: The results of simulating data attacks should determine future performance. This is effective if analysts evaluate the results and find ways to improve them.
FAQ
What should you do to secure cloud storage?
Use strong, unique passwords and enable multi-factor authentication (MFA) for your cloud accounts.
Why enable encryption for cloud data?
Encryption — both during transfer and at rest — ensures data remains unreadable to unauthorized parties even if breached or intercepted.
How can you manage access safely?
Grant access only to necessary users, review permissions regularly, and disable unused accounts or shared links.