FTP vs SFTP: What’s the Difference and Which Should You Use
In a digital era where vast amounts of data are constantly transmitted across the globe, ensuring the safe and reliable transfer of files has become more critical than ever. Whether personal documents, financial data, customer information, or proprietary software code, organizations and individuals must protect their data from unauthorized access, interception, or corruption. Among the many protocols developed for transferring files, the Secure File Transfer Protocol, better known as SFTP, has gained a reputation for its robust security and dependability.
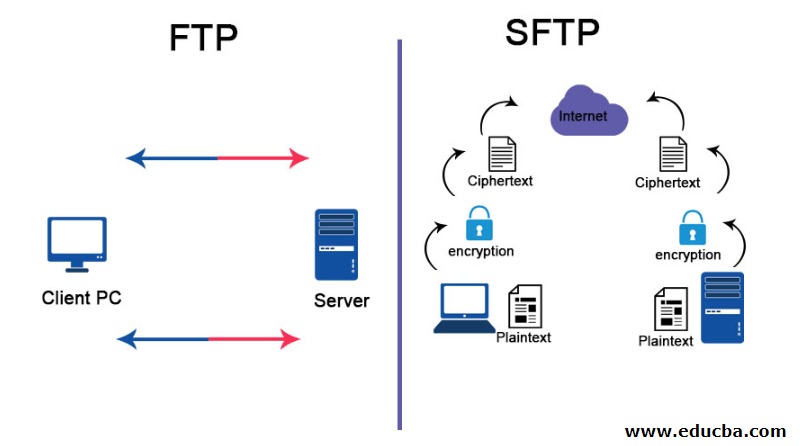
SFTP is a network protocol that provides file access, file transfer, and file management functionalities over any reliable data stream. Built on the SSH (Secure Shell) protocol, SFTP encrypts commands and data, providing a secure channel for file operations. Unlike traditional FTP (File Transfer Protocol), which sends data in plaintext and is vulnerable to eavesdropping and other forms of cyberattacks, SFTP is inherently secure and preferred in security-conscious environments.
Understanding how SFTP works and why it is superior to older file transfer methods is crucial for IT administrators, web developers, software engineers, and anyone managing sensitive digital assets. In this article, we’ll examine SFTP’s architecture, core features, security mechanisms, differences from other protocols, common use cases, and best practices for implementation.
The Technical Foundation of SFTP
SFTP operates as an extension of the SSH protocol. SSH was initially designed to provide secure remote login sessions to servers and is now widely used for various administrative tasks. Because SFTP inherits SSH’s cryptographic capabilities, every session established using SFTP is encrypted from start to finish. This includes not just the files being transferred, but also commands, authentication credentials, and metadata like filenames and directory structures.
SFTP uses port 22 by default, the same as SSH, simplifying firewall configuration. Unlike FTP, which requires opening multiple ports for control and data channels, SFTP uses a single encrypted channel, reducing complexity and minimizing potential attack vectors. This makes SFTP especially suitable for enterprise networks typically protected by strict firewall policies.
SFTP in Practice – Basic Command Usage
If you’re using a Unix-based system like Linux or macOS, or even using WSL on Windows, you can initiate an SFTP session using the following simple command: