Everything About BOTNETs
BOTNETs typically Take Control Of Several Computers Around The World And Install Malware, Spyware, Spam, And More On These Devices. But How Do Botnets Work? Who controls them, And How Can We Prevent them?
Bunters typically take control of many computers worldwide and install malware, spyware, spam, and more on them. But how do batons work? Who controls them, and how can we prevent them?
What Are BTNETs?
A botnet is a set of Internet-connected devices that are infected with and controlled by malware, including computers, servers, mobile phones, and the Internet of Things. Users usually do not know that their systems are infected with a botnet.
Cybercriminals control devices on which some malware is installed. This malware hides its malicious activities so the user does not notice them. For example, you may spam thousands of people on your tablet without knowing it.
Devices infected with botnet are commonly referred to as “zombies”.
What does Button do?
Depending on Button runs it, a botnet can have many different functions.
1—Spam: Spammers send a lot of spam worldwide. For example, the rate of spam sent via email last year was 56.69%. The number of spammers worldwide has dropped by about 50 percent since FireEye turned off the Srizbi botnet.
2- Malware: Sending malware and spyware to weak devices.
3- Data: Recording passwords and other personal information.
Bitcoin: Those who control the botnet using infected devices to steal bitcoins and other Internet credits.
6- DDoS: Those who control the botnet take control of the infected devices and turn them offline when attacked.
Button operators often exploit these methods for malicious work.
What does your BOTNET look like?
We know that a botnet is a Network of infected computers. However, the central components and architecture of BOTNET are exciting.
Architecture:
Client-Server Model: A client-server botnet typically uses a chat client (previously IRC, but modern botnets use Telegram and other encrypted messaging services) to connect to a domain or website. The operator sends a message to the server that executes the command. While the structure of botnets is very different, it can turn off client-server botnets with effort.
Peer-to-peer: A peer-to-peer (P2P) botnet attempts to turn off Security programs and research programs that identify specific C2 servers by building a decentralized Network. A peer-to-peer Network is more advanced than the client-server model.
Instead of a Network of connected infected devices communicating with each other via IP addresses, operators prefer to use zombie devices connected to the node. As a result, there are many connected devices and different nodes, and the Network is not traceable.
Command and control
Command and control protocols (C&C or C2) appear in different masks:
Telnet: Telnet botnet is relatively simple and uses scripts to scan IPs to enter the Telnet server and SSH to add weak devices.
IRC: IRC networks provide a very low-bandwidth communication method for the C2 protocol. The ability to quickly change channels offers more Security for botnet operators. Still, it makes it easier for infected clients to leave the botnet if they do not receive the updated channel information. IRC traffic tracking is effortless, so many hackers do not use this method.
Domains: Some large botnets use domains instead of messenger clients. Infected devices can access a specific domain that executes a list of control commands. The disadvantage of this method is the very high bandwidth requirement for large botnets, which makes them detectable very quickly.
P2P: A P2P protocol usually implements digital signatures using asymmetric encoding. As a result, while the operator holds the key, the other person can almost not execute other commands on the botnet. As a result, removing a P2P botnet is very difficult due to the lack of a dedicated C2 server.
Others: Over the past year, botnet operators have used exciting command and control channels, including social networking channels such as Twitter, which controls the Android Twitoor botnet.
Instagram is also not very secure. In 2017, for example, a Russian cyber-spy group used the following comments from Britney Spears’ Instagram photos to store the location of a C2 malware distribution server.
Zombies
At the end of the string is a botnet of infected devices.
Button operators infect weak devices to expand their network. Interestingly, some botnet operators do not have good relationships with each other and use infected devices against each other.
Most of the time, zombie device owners are unaware of the existence of botnets. Sometimes, botnet malware also controls other malware.
Types of devices
Internet-connected devices are becoming increasingly popular, and botnets do not only target Windows and Mac devices. IoT devices are also not safe, and smartphones and tablets are not secure. In recent years, Android devices have often been involved in botnet attacks.
Android is a straightforward target because it is open source, has different operating System versions, and is very weak. Of course, Apple devices have been infected with botnet several times. Another target of botnets is weak routers. Routers with outdated and insecure hardware are easily attacked.
Destroy your baton
Getting rid of BOTNET is not easy. Sometimes, the botnet architecture is such that the operator can quickly rebuild it, and sometimes, the baton is too big. Eliminating batons often requires collaboration between Security researchers, state-owned companies, and hackers, who sometimes require backdoor techniques.
GameOver Zeus
One of the most prominent examples was the destruction of the GameOver Zeus botnet. GOZ was one of the largest botnets in the past few years, infecting nearly one million devices. The primary purpose of this theft botnet was to send spam emails from a unique domain that the algorithm generated, and there did not seem to be a way to get rid of it.
The domain generation algorithm helps the botnet create a long list of domains to use as hotspots for the botnet malware. Too many meeting points make it almost impossible to prevent the botnet from expanding, and only operators know the list of domains.
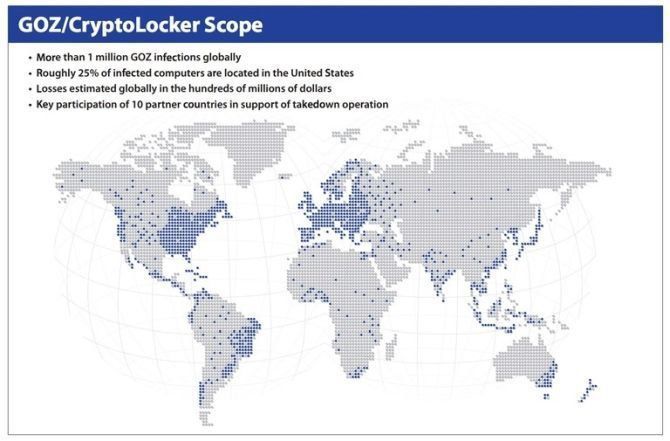
In 2014, a team of Security researchers working with the FBI and other international organizations destroyed GameOver Zeus. Of course, this was by no means easy. After observing the domain registrations, this group registered 150,000 domains in six months, causing no more domains to be registered.
Many ISPs then relinquished control of the GOZ proxy nodes used by botnet operators to communicate between command and control servers.
After an hour, the bot’s owner, Eugene Bogucci, discovered that his buttotongone and spent four to five hours trying to restore it.
The researchers then sent free Coding tools to the victims.
The IoT botnet is different.
In 2016, Mirai was the most prominent and worst detective detected. Before its elimination, an IoT-based botnet targeted many computers with DDoS attacks. The figure below shows the number of countries targeted by Mirai.
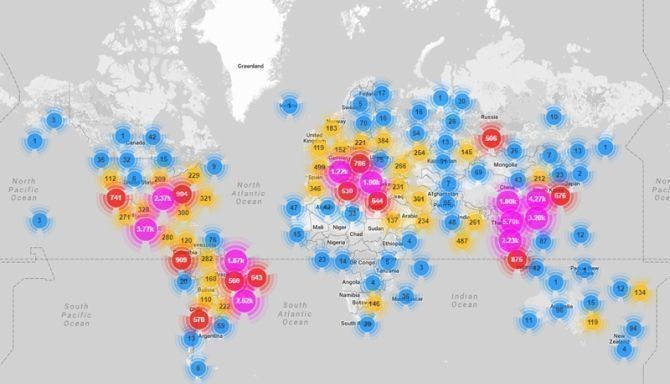
While Mirai was not the largest botnet in the world, it carried out the most significant attacks. This botnet used 62 default IoT device passwords.
Most IoT devices are online in one place and always have Network resources to share. However, with the proliferation of low-security IoT devices, the number of infected devices is increasing.
Keep yourself safe
We learned a lot from the Bentons. But how do we care for our devices? First, update your System. Regular updates correct your operating System’s weaknesses.
Second, download and install antivirus and anti-malware software. There are so many good options available to you.
Third, be careful when browsing the web. For example, you can use the uBlock Origin plugin.

