Important Points About TLS That You May Not Be Aware Of
The Transport Layer Security (TLS) Protocol Is One Of The Most Powerful Security Protocols In The Cyber World, First Introduced By The Internet Engineering Group (IETF) In 1999.
This protocol develops to protect users’ privacy and data security transmitted through communication networks and channels.
The main task of this protocol is to encrypt the communication between the web application and, of course, the servers.
Companies typically use the TLS protocol to encrypt communications and messages via email, messaging, and VOIP.
What is the difference between TLS and SSL protocols?
SSL is one of the oldest protocols in security, initially developed by Netscape to establish secure and encrypted communication between the server and the client. Still, eventually, a complete version of it called the TLS protocol became widely available to companies. TLS has better security and more performance than SSL. It also uses a more robust encryption algorithm.
Version 1 of the TLS protocol is the same as version 3.1 of the SSL protocol. For this reason, some sources use the terms TLS and SSL instead of each other. Any site that uses the Secure Hypertext Transfer Protocol (HTTPS) encrypts information through the TLS protocol.
It encrypts all confidential information transmitted between the server and the client to not be visible to unauthorized persons. Only those who have the relevant key can see the information.
Why should businesses and applications use the TLS protocol?
TLS protects data-driven applications from data breaches and other cyber attacks by encrypting information. In addition, the use of HTTPS in websites encrypted with TLS has become a global standard, helping to protect web applications against a variety of cyberattacks. For example, the Google Chrome browser blocks websites that do not have an HTTPS lock icon and warns users against doing so. So that users have to personally click on the links of sites that do not use the protocol.
What does the TLS protocol do?
One of the most critical applications of the TLS protocol is encryption, authentication, and authentication. The protocol encrypts the data transmitted between the server and the client, reassuring the receiver and sender that the third party does not distort the information. In general, the above protocol does the following:
Encryption: Hiding data from third-party tools.
Authentication: Ensuring that the identity of the recipient and sender is correct.
Integrity: Verifies that data has not been forged or tampered it.
What does the TLS protocol do?
Every website or application that uses the TLS protocol must have a TLS certificate known as an SSL certificate. The certification authority issues this certificate to any natural or legal users with an Internet domain that contains information about the domain owner and the server’s public key. This information and public key are essential for server authentication.
A TLS connection involves the process of transmitting preliminary information and building a secure connection for the exchange of information. This process is known as TLS Handshake. In the above process, which is performed between the user device and the web server, the operation is performed as follows:
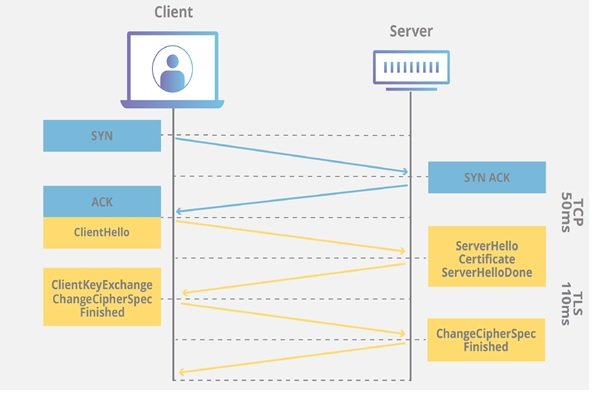
First, one of the TLS versions, which includes 1.0, 1.1, or 1.3, is specified and provided to the user and the server.
At this point, the TLS command generates a token set for each communication session. These tokens are algorithms that determine which shared cryptographic keys are assigned and used for that particular session.
TLS can set session keys on an unencrypted channel through the public key encryption pattern.
In addition, TLS Handshake has the task of authentication, which involves proving the server to the user and using public keys. However, only the original sender can encrypt the data with its private key. Note that the shared server key is part of the TLS certificate.
Finally, creating session keys to encrypt the messages exchanged between the client and the server is performed after completing the TLS access process.
After encryption and authentication, the data is signed with a message authentication code or message authentication code (MAC) to ensure the authenticity of the data. Imagine a seller of foil on a medicine box, in which case the consumer is assured that the drugs will not be tampered with by unauthorized persons. The figure below shows how to do this.
How does TLS affect web application traffic and performance?
Indeed, the latest TLS versions do not impact how web-based applications work, but on the other hand, setting up a TLS connection is almost complex and time-consuming and requires a lot of computing power to load. For example, the client and the server must communicate several times before and after the data transfer. This operation takes a lot of time and takes up part of the client and server memory when it can use to load web applications.
For solving this problem, technologies such as TLS False Start have been installed to reduce the potential delays caused by the TLS handshake. TLS False Start authorizes data transfer to the server and client before starting the TLS Handshake connection.
Interestingly, the technology allows clients and servers that have been connected in the past to use the abbreviated TLS Handshake to reduce authentication time. Therefore, there is no need for the client and server to go through all the TLS Handshake steps.
Such technologies have made TLS a fast protocol that has little effect on load time. By today’s standards, the computational costs associated with TLS are meager. Version TLS 1.3, which was released in 2018, is much faster than previous versions. In this version, the TLS Handshake process requires only a reciprocating connection, shortening the process by a few milliseconds. Additionally, if a user has previously connected to a website, the return time of the TLS Handshake will be zero to increase speed.
How should TLS be implemented on a website?
Cloudflare provides free TLS / SSL certification to applicants to enhance website security. If a user does not want to use the services of this company to receive an SSL certificate, he must buy from other certification companies and install it on a server.

